Synthetic identity fraud involves criminals creating fake identities using fabricated or stolen information to open fraudulent accounts and evade detection. Insider fraud occurs when trusted employees misuse their access to commit financial crimes, often leading to significant internal losses and reputational damage. Explore the methods and prevention strategies behind these two critical banking fraud threats.
Why it is important
Knowing the difference between synthetic identity fraud and insider fraud is crucial for banks to tailor detection strategies effectively, as synthetic identity fraud involves creating fake identities using fabricated or stolen information, while insider fraud is committed by employees exploiting internal access. Synthetic fraud often targets consumer onboarding and loan origination processes, leading to significant financial losses and regulatory scrutiny. Insider fraud poses risks to data security, operational integrity, and can result in complex legal consequences for the institution. Distinguishing these fraud types enhances risk management, compliance, and fraud prevention frameworks within banking operations.
Comparison Table
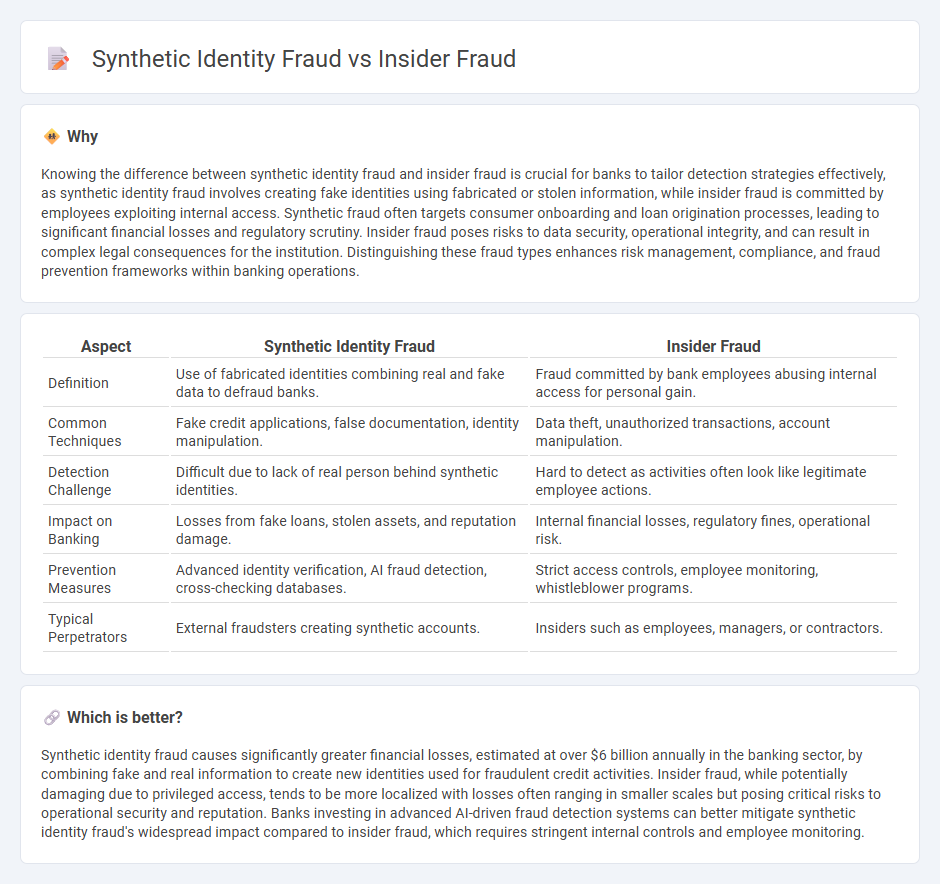
| Aspect | Synthetic Identity Fraud | Insider Fraud |
|---|---|---|
| Definition | Use of fabricated identities combining real and fake data to defraud banks. | Fraud committed by bank employees abusing internal access for personal gain. |
| Common Techniques | Fake credit applications, false documentation, identity manipulation. | Data theft, unauthorized transactions, account manipulation. |
| Detection Challenge | Difficult due to lack of real person behind synthetic identities. | Hard to detect as activities often look like legitimate employee actions. |
| Impact on Banking | Losses from fake loans, stolen assets, and reputation damage. | Internal financial losses, regulatory fines, operational risk. |
| Prevention Measures | Advanced identity verification, AI fraud detection, cross-checking databases. | Strict access controls, employee monitoring, whistleblower programs. |
| Typical Perpetrators | External fraudsters creating synthetic accounts. | Insiders such as employees, managers, or contractors. |
Which is better?
Synthetic identity fraud causes significantly greater financial losses, estimated at over $6 billion annually in the banking sector, by combining fake and real information to create new identities used for fraudulent credit activities. Insider fraud, while potentially damaging due to privileged access, tends to be more localized with losses often ranging in smaller scales but posing critical risks to operational security and reputation. Banks investing in advanced AI-driven fraud detection systems can better mitigate synthetic identity fraud's widespread impact compared to insider fraud, which requires stringent internal controls and employee monitoring.
Connection
Synthetic identity fraud and insider fraud intersect through the exploitation of internal banking systems to create or manipulate fake customer profiles. Insiders with privileged access can facilitate synthetic identities by bypassing verification protocols, enabling fraudulent loan approvals or credit line establishments. This collusion amplifies financial losses and challenges the efficacy of traditional fraud detection mechanisms within banks.
Key Terms
Insider Fraud:
Insider fraud involves employees or trusted individuals exploiting their access to company systems or data to commit financial theft, data breaches, or manipulation of records, often leading to significant organizational losses. This type of fraud can be difficult to detect due to the perpetrator's legitimate access and knowledge of internal controls, making advanced behavioral analytics and access monitoring crucial. Learn more about how organizations can implement robust detection and prevention strategies to combat insider fraud effectively.
Employee Misconduct
Employee misconduct in insider fraud involves trusted employees exploiting access to company systems and data for personal gain, often through unauthorized transactions or data breaches. Synthetic identity fraud, by contrast, manipulates fabricated identities to bypass traditional security measures without direct employee involvement. Explore comprehensive strategies to detect and prevent these distinct fraud types within your organization.
Unauthorized Access
Insider fraud involves employees exploiting legitimate access to systems to steal data, manipulate transactions, or cover tracks, while synthetic identity fraud uses fabricated identities to gain unauthorized access to financial services or sensitive information. Unauthorized access in insider fraud exploits trusted credentials, whereas synthetic identity fraud leverages false identities to bypass security checks. Explore more to understand effective prevention strategies for both fraud types.
Source and External Links
Insider Fraud Prevention: Tips & Tricks for Your Organization - Insider fraud includes actions like data misappropriation and financial schemes, often committed by employees, contractors, or business partners who misuse access to sensitive information or payment systems for personal gain.
Insider Fraud: Combating the Growing Threat in Financial Services - Insider fraud in financial services is often driven by personal crises or grievances, with warning signs including secretive behavior, unusual data access, and poor documentation practices.
Defining Insider Threats - Insider threats can be unintentional (negligence or accidents) or intentional (malicious actions for personal benefit or to harm the organization), and may involve collusion with external actors or risks posed by third-party vendors.
 dowidth.com
dowidth.com