Zero Trust security models eliminate implicit trust by continuously validating every user and device accessing a network, minimizing the risk of breaches in increasingly complex IT environments. In contrast, the Trust But Verify approach allows initial access based on assumed trust, followed by monitoring and verification to detect anomalies. Explore the strengths and challenges of each strategy to enhance your organization's cybersecurity framework.
Why it is important
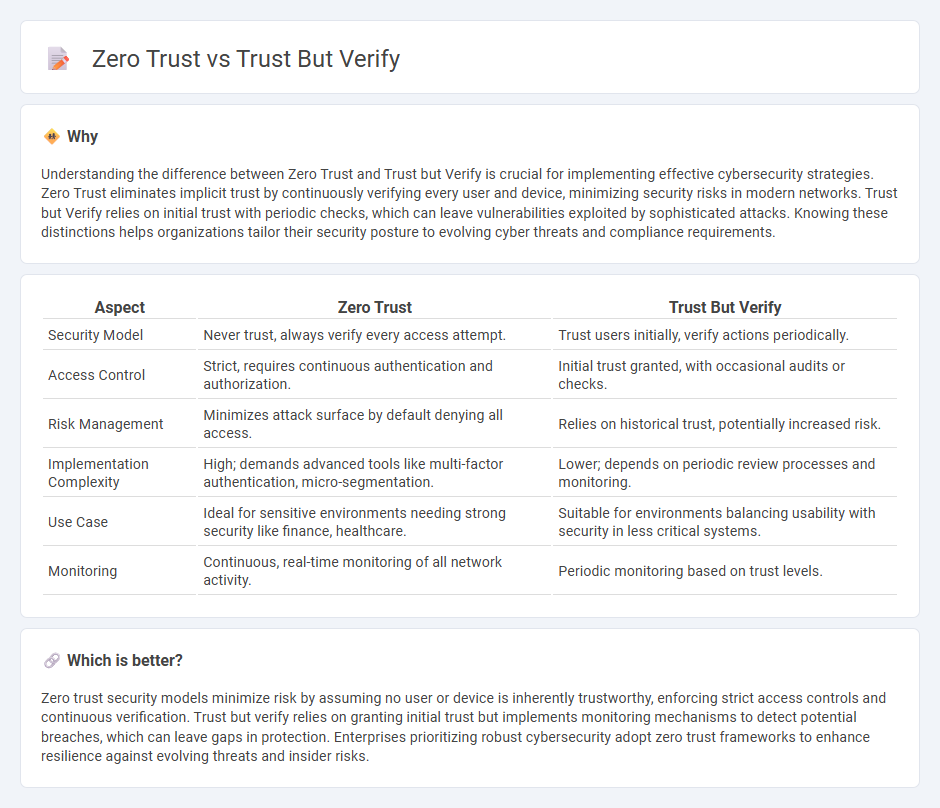
Understanding the difference between Zero Trust and Trust but Verify is crucial for implementing effective cybersecurity strategies. Zero Trust eliminates implicit trust by continuously verifying every user and device, minimizing security risks in modern networks. Trust but Verify relies on initial trust with periodic checks, which can leave vulnerabilities exploited by sophisticated attacks. Knowing these distinctions helps organizations tailor their security posture to evolving cyber threats and compliance requirements.
Comparison Table
| Aspect | Zero Trust | Trust But Verify |
|---|---|---|
| Security Model | Never trust, always verify every access attempt. | Trust users initially, verify actions periodically. |
| Access Control | Strict, requires continuous authentication and authorization. | Initial trust granted, with occasional audits or checks. |
| Risk Management | Minimizes attack surface by default denying all access. | Relies on historical trust, potentially increased risk. |
| Implementation Complexity | High; demands advanced tools like multi-factor authentication, micro-segmentation. | Lower; depends on periodic review processes and monitoring. |
| Use Case | Ideal for sensitive environments needing strong security like finance, healthcare. | Suitable for environments balancing usability with security in less critical systems. |
| Monitoring | Continuous, real-time monitoring of all network activity. | Periodic monitoring based on trust levels. |
Which is better?
Zero trust security models minimize risk by assuming no user or device is inherently trustworthy, enforcing strict access controls and continuous verification. Trust but verify relies on granting initial trust but implements monitoring mechanisms to detect potential breaches, which can leave gaps in protection. Enterprises prioritizing robust cybersecurity adopt zero trust frameworks to enhance resilience against evolving threats and insider risks.
Connection
Zero trust is a cybersecurity framework that assumes no implicit trust within a network, requiring continuous verification of user identities and device integrity before granting access. The "trust but verify" principle aligns with zero trust by emphasizing the need for ongoing authentication and authorization checks rather than relying on initial trust assumptions. Both strategies aim to minimize security breaches by enforcing strict access controls and continuous monitoring in dynamic IT environments.
Key Terms
Authentication
Trust but verify relies on initial authentication followed by monitoring user actions to ensure continuous access security, which can still allow risks if credentials are compromised. Zero trust eliminates implicit trust, requiring strict identity verification and continuous authentication for every access request, minimizing potential breaches. Explore more about how zero trust enhances authentication security in modern networks.
Access Control
Trust but verify relies on granting users access based on initial trust with continuous monitoring to detect anomalies, while Zero Trust enforces strict identity verification and least-privilege access controls at every access attempt without assuming any inherent trust. Zero Trust architecture utilizes multi-factor authentication, micro-segmentation, and real-time access evaluation to minimize the attack surface and prevent lateral movement within networks. Explore more about how these models shape modern access control strategies and cybersecurity frameworks.
Network Segmentation
Trust but verify relies on initial network access combined with continuous monitoring to ensure compliance, creating segmentation based on presumed trust levels. Zero trust enforces strict network segmentation by requiring continuous authentication and authorization for every request, minimizing lateral movement risks. Explore how implementing zero trust enhances network segmentation compared to traditional trust but verify models.
Source and External Links
"Trust, but verify" is sound leadership advice - LBM Journal - The phrase, popularized by Ronald Reagan during nuclear treaty talks with the Soviet Union, advises leaders to balance trust with accountability and verification, especially when challenging existing practices or assumptions.
Trust, but verify - Simple English Wikipedia - "Trust, but verify" is a Russian proverb used by Reagan in Cold War nuclear disarmament talks meaning trust someone but ensure through verification they do not betray that trust.
"Trust, but Verify": How Reagan's Maxim Can Inform International AI Governance - CIGI - Reagan's phrase from arms control negotiations highlights the importance of verification in international agreements, a principle now considered vital in emerging fields like AI governance to ensure compliance and safety.
 dowidth.com
dowidth.com