Passkey and OAuth are advanced authentication technologies enhancing digital security by simplifying user access and reducing password reliance. Passkeys utilize cryptographic key pairs for seamless, phishing-resistant logins, while OAuth enables secure third-party access authorization without sharing credentials. Explore how these innovative methods transform online identity management and safeguard user data.
Why it is important
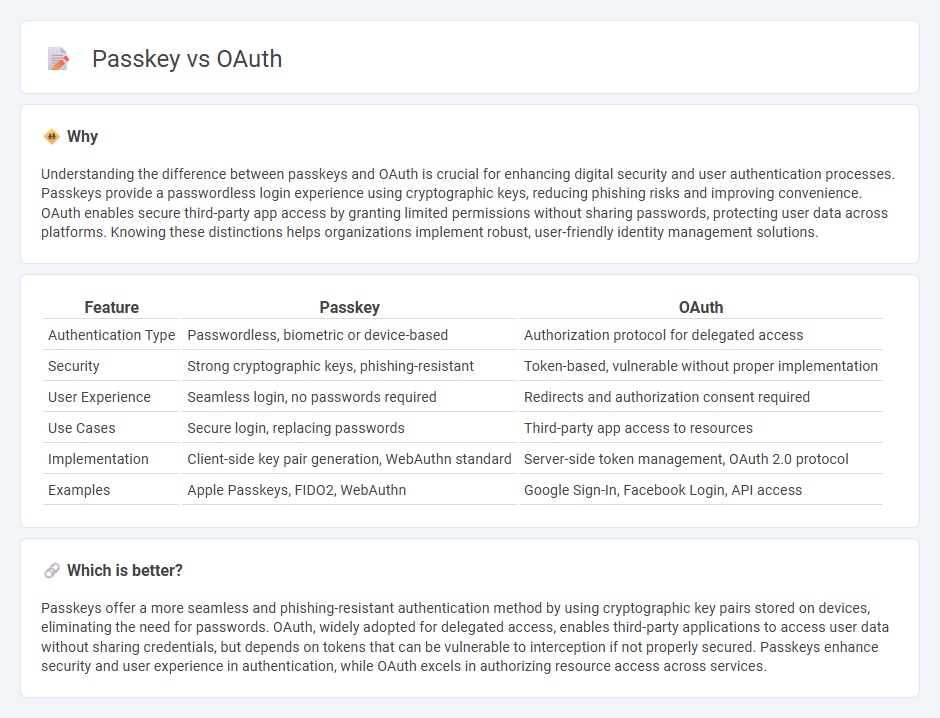
Understanding the difference between passkeys and OAuth is crucial for enhancing digital security and user authentication processes. Passkeys provide a passwordless login experience using cryptographic keys, reducing phishing risks and improving convenience. OAuth enables secure third-party app access by granting limited permissions without sharing passwords, protecting user data across platforms. Knowing these distinctions helps organizations implement robust, user-friendly identity management solutions.
Comparison Table
| Feature | Passkey | OAuth |
|---|---|---|
| Authentication Type | Passwordless, biometric or device-based | Authorization protocol for delegated access |
| Security | Strong cryptographic keys, phishing-resistant | Token-based, vulnerable without proper implementation |
| User Experience | Seamless login, no passwords required | Redirects and authorization consent required |
| Use Cases | Secure login, replacing passwords | Third-party app access to resources |
| Implementation | Client-side key pair generation, WebAuthn standard | Server-side token management, OAuth 2.0 protocol |
| Examples | Apple Passkeys, FIDO2, WebAuthn | Google Sign-In, Facebook Login, API access |
Which is better?
Passkeys offer a more seamless and phishing-resistant authentication method by using cryptographic key pairs stored on devices, eliminating the need for passwords. OAuth, widely adopted for delegated access, enables third-party applications to access user data without sharing credentials, but depends on tokens that can be vulnerable to interception if not properly secured. Passkeys enhance security and user experience in authentication, while OAuth excels in authorizing resource access across services.
Connection
Passkeys enhance security in authentication processes by eliminating passwords and enabling biometric or device-based verification, while OAuth facilitates secure authorization by granting third-party applications limited access to user resources without sharing credentials. Both technologies work together to strengthen identity management frameworks by combining passwordless authentication with delegated access control. This integration reduces phishing risks and improves user experience in modern digital ecosystems.
Key Terms
Authentication
OAuth streamlines authentication by allowing users to grant third-party applications controlled access to their resources without sharing passwords, enhancing security and user convenience. Passkeys eliminate passwords entirely by using cryptographic key pairs stored on devices, offering phishing-resistant, seamless login experiences across platforms. Discover how integrating OAuth or passkey authentication can fortify your security strategy and improve user trust.
Authorization
OAuth is a widely adopted authorization framework that allows third-party applications to access user resources without sharing credentials, enhancing security and user control. Passkeys, grounded in public-key cryptography, streamline authentication by eliminating passwords, but primarily focus on identity verification rather than delegated authorization. Explore the detailed distinctions between OAuth's authorization capabilities and passkeys' authentication mechanisms to optimize your security strategy.
Credential Management
OAuth simplifies credential management by enabling secure delegated access without exposing user passwords, relying on tokens for authentication and authorization. Passkeys enhance security by eliminating passwords entirely, using cryptographic key pairs stored on devices for seamless and phishing-resistant authentication. Explore how these approaches revolutionize digital identity management to secure user credentials effectively.
Source and External Links
OAuth - Wikipedia - OAuth is an open standard for access delegation that lets users grant websites or apps access to their information on other websites without sharing passwords.
What Is OAuth? | Microsoft Security - OAuth is a technological standard that enables one app or service to authorize another to access some of your data securely, without revealing your credentials.
OAuth 2.0 - OAuth 2.0 is the industry-standard protocol for authorization, designed for simplicity and supporting various flows for web, desktop, mobile, and device applications.
 dowidth.com
dowidth.com