Zero Trust architecture enhances cybersecurity by continuously verifying every user and device before granting access, significantly reducing the risk of breaches compared to traditional VPNs that often trust users once connected. VPNs create encrypted tunnels for remote access but can be vulnerable if credentials are compromised or if lateral movement occurs within the network. Explore the differences between Zero Trust and VPN to understand which security model best protects your organization.
Why it is important
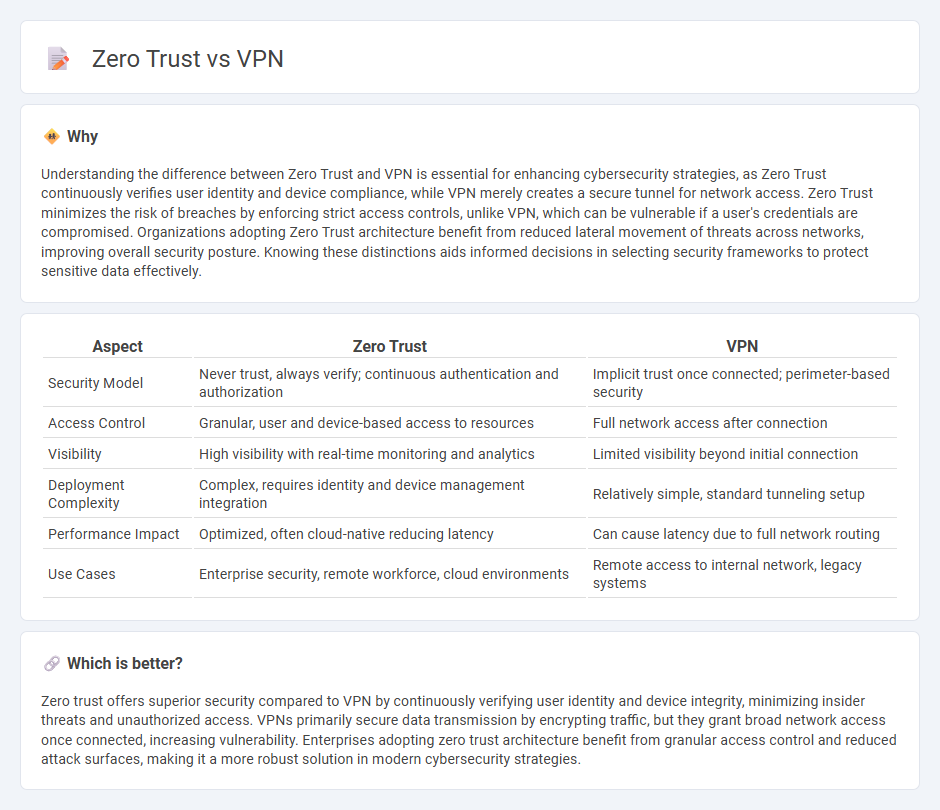
Understanding the difference between Zero Trust and VPN is essential for enhancing cybersecurity strategies, as Zero Trust continuously verifies user identity and device compliance, while VPN merely creates a secure tunnel for network access. Zero Trust minimizes the risk of breaches by enforcing strict access controls, unlike VPN, which can be vulnerable if a user's credentials are compromised. Organizations adopting Zero Trust architecture benefit from reduced lateral movement of threats across networks, improving overall security posture. Knowing these distinctions aids informed decisions in selecting security frameworks to protect sensitive data effectively.
Comparison Table
| Aspect | Zero Trust | VPN |
|---|---|---|
| Security Model | Never trust, always verify; continuous authentication and authorization | Implicit trust once connected; perimeter-based security |
| Access Control | Granular, user and device-based access to resources | Full network access after connection |
| Visibility | High visibility with real-time monitoring and analytics | Limited visibility beyond initial connection |
| Deployment Complexity | Complex, requires identity and device management integration | Relatively simple, standard tunneling setup |
| Performance Impact | Optimized, often cloud-native reducing latency | Can cause latency due to full network routing |
| Use Cases | Enterprise security, remote workforce, cloud environments | Remote access to internal network, legacy systems |
Which is better?
Zero trust offers superior security compared to VPN by continuously verifying user identity and device integrity, minimizing insider threats and unauthorized access. VPNs primarily secure data transmission by encrypting traffic, but they grant broad network access once connected, increasing vulnerability. Enterprises adopting zero trust architecture benefit from granular access control and reduced attack surfaces, making it a more robust solution in modern cybersecurity strategies.
Connection
Zero trust security models assume no implicit trust and require continuous verification of users and devices, aligning closely with the secure access principles of VPNs. VPNs create encrypted tunnels that protect data in transit, while zero trust extends this protection by enforcing strict identity verification and access policies beyond the network perimeter. Combining zero trust with VPN technology enhances overall cybersecurity by minimizing attack surfaces and preventing unauthorized access.
Key Terms
Network Perimeter
VPNs create secure tunnels to extend the network perimeter, allowing remote users to access internal resources as if they were on-site. Zero Trust architecture eliminates reliance on a fixed perimeter by enforcing strict identity verification and least-privilege access policies for every user and device, regardless of location. Explore more about how these approaches redefine network security and protect critical assets.
Authentication
VPN relies on perimeter-based security by creating an encrypted tunnel for authorized users, but authentication primarily depends on username and password combinations, which can be vulnerable to breaches. Zero Trust architecture enforces stringent, continuous authentication methods such as multi-factor authentication (MFA) and adaptive verification to ensure every access request is thoroughly validated regardless of network location. Explore deeper insights into how Zero Trust redefines authentication for robust cybersecurity.
Least Privilege
VPNs provide secure remote access by creating encrypted tunnels but often grant broad network access, posing risks if credentials are compromised. Zero Trust architecture enforces the principle of Least Privilege, ensuring users access only the specific resources necessary for their roles, minimizing potential attack surfaces. Explore how adopting Zero Trust with Least Privilege can enhance your organization's cybersecurity strategy.
Source and External Links
Virtual private network - A VPN is a technology that extends a private network across one or more untrusted or isolated networks by creating secure encrypted tunnels, allowing users to access private network resources remotely and protect their internet privacy.
NordVPN: The best VPN service online for free, open internet - NordVPN encrypts your internet traffic and routes it through secure remote servers to hide your IP address, change your virtual location, and protect you from spying and cybercriminals, with one of the fastest speeds due to its NordLynx protocol.
The best VPN for speed and security - Proton VPN offers a secure and fast VPN service available in over 120 countries, providing options for free use or premium plans with enhanced features to secure and accelerate your internet connection.
 dowidth.com
dowidth.com