Trustless computing relies on cryptographic protocols to enable secure transactions without the need for a trusted intermediary, enhancing transparency and decentralization in blockchain environments. In contrast, Hardware Security Modules (HSMs) provide physical protection for cryptographic keys through tamper-resistant hardware, ensuring secure key storage and management in enterprise settings. Explore the differences and benefits of trustless computing versus HSMs to better understand their roles in securing digital assets.
Why it is important
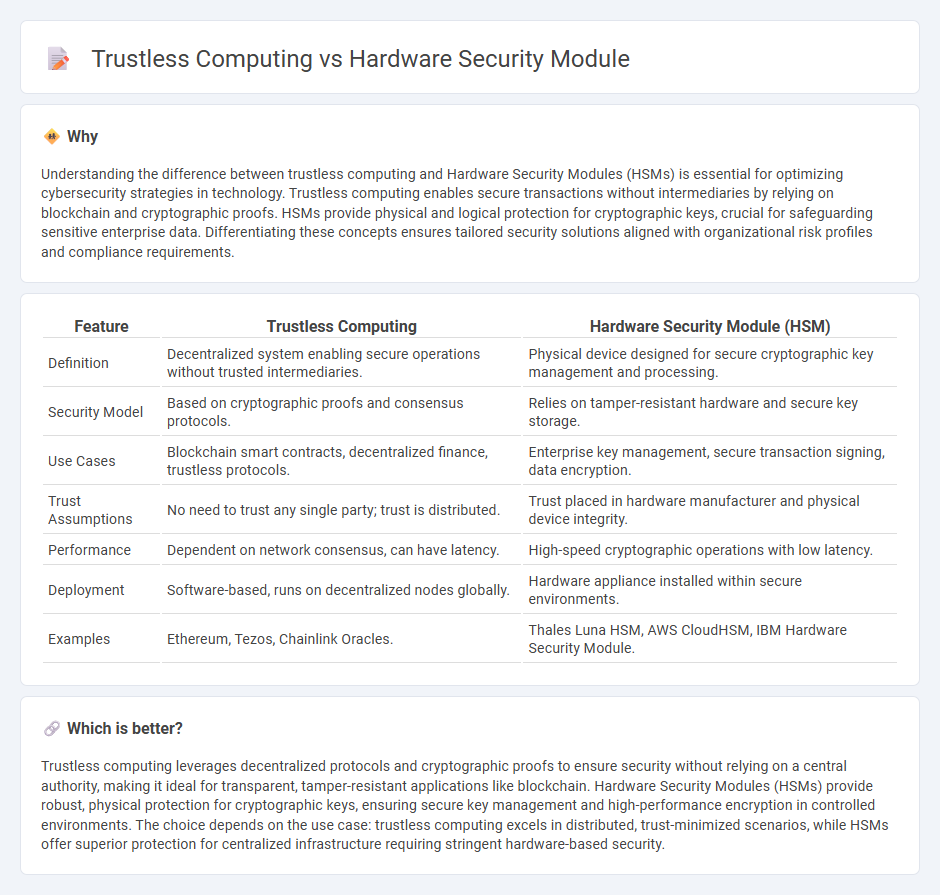
Understanding the difference between trustless computing and Hardware Security Modules (HSMs) is essential for optimizing cybersecurity strategies in technology. Trustless computing enables secure transactions without intermediaries by relying on blockchain and cryptographic proofs. HSMs provide physical and logical protection for cryptographic keys, crucial for safeguarding sensitive enterprise data. Differentiating these concepts ensures tailored security solutions aligned with organizational risk profiles and compliance requirements.
Comparison Table
| Feature | Trustless Computing | Hardware Security Module (HSM) |
|---|---|---|
| Definition | Decentralized system enabling secure operations without trusted intermediaries. | Physical device designed for secure cryptographic key management and processing. |
| Security Model | Based on cryptographic proofs and consensus protocols. | Relies on tamper-resistant hardware and secure key storage. |
| Use Cases | Blockchain smart contracts, decentralized finance, trustless protocols. | Enterprise key management, secure transaction signing, data encryption. |
| Trust Assumptions | No need to trust any single party; trust is distributed. | Trust placed in hardware manufacturer and physical device integrity. |
| Performance | Dependent on network consensus, can have latency. | High-speed cryptographic operations with low latency. |
| Deployment | Software-based, runs on decentralized nodes globally. | Hardware appliance installed within secure environments. |
| Examples | Ethereum, Tezos, Chainlink Oracles. | Thales Luna HSM, AWS CloudHSM, IBM Hardware Security Module. |
Which is better?
Trustless computing leverages decentralized protocols and cryptographic proofs to ensure security without relying on a central authority, making it ideal for transparent, tamper-resistant applications like blockchain. Hardware Security Modules (HSMs) provide robust, physical protection for cryptographic keys, ensuring secure key management and high-performance encryption in controlled environments. The choice depends on the use case: trustless computing excels in distributed, trust-minimized scenarios, while HSMs offer superior protection for centralized infrastructure requiring stringent hardware-based security.
Connection
Trustless computing relies on cryptographic protocols that enable secure transactions without needing a trusted intermediary, while Hardware Security Modules (HSMs) provide a robust physical and cryptographic foundation for key management and secure computation. HSMs safeguard sensitive cryptographic keys and operations, ensuring integrity and confidentiality within trustless environments such as blockchain networks and decentralized applications. Together, they enhance security by combining decentralized trust mechanisms with tamper-resistant hardware, minimizing vulnerabilities in distributed computing systems.
Key Terms
Cryptographic Key Management
Hardware Security Modules (HSMs) provide a dedicated, tamper-resistant environment for cryptographic key storage and management, ensuring high levels of security through physical and logical safeguards. Trustless computing leverages decentralized and verifiable protocols, such as blockchain and secure enclaves, to manage keys without relying on a central trusted authority, enhancing transparency and reducing single points of failure. Explore the strengths and trade-offs between these approaches to optimize cryptographic key management for your security needs.
Secure Enclave
Secure Enclave, a dedicated hardware security module (HSM) integrated within modern processors, offers tamper-resistant storage and isolated execution for sensitive data and cryptographic operations, ensuring robust protection against physical and software attacks. Trustless computing, often associated with decentralized blockchain environments, relies on cryptographic proofs and consensus mechanisms to achieve security without a central trusted authority, contrasting with the hardware-rooted trust model of Secure Enclave. Explore further how Secure Enclave's hardware-based security complements and differs from trustless computing paradigms in safeguarding digital assets.
Zero-Knowledge Proofs
Hardware Security Modules (HSMs) provide tamper-resistant environments for key management and cryptographic operations, ensuring high-assurance security in controlled hardware. Trustless computing leverages cryptographic protocols, notably Zero-Knowledge Proofs (ZKPs), to enable verification of computations without revealing sensitive data, enhancing privacy in decentralized systems. Explore the nuances of these technologies to better understand their roles in securing modern cryptographic applications.
Source and External Links
Hardware Security Module - A hardware security module is a physical computing device that safeguards and manages secrets, performing encryption and decryption functions for digital signatures and authentication.
Hardware Security Modules (HSMs) - Thales CPL - Thales HSMs are dedicated crypto processors designed to protect the crypto key lifecycle by securely managing, processing, and storing cryptographic keys inside a hardened, tamper-resistant device.
What is a Hardware Security Module? - A hardware security module provides extra security for sensitive data by offering a hardened, isolated environment that safeguards against tampering, compromise, and theft.
 dowidth.com
dowidth.com