eBPF (extended Berkeley Packet Filter) enables advanced, programmable network traffic analysis and monitoring directly within the Linux kernel, offering high performance and flexibility beyond traditional tools. tcpdump, a widely-used command-line packet analyzer, captures and displays packet headers, serving as an essential tool for network troubleshooting and security audits. Discover how eBPF enhances network observability compared to tcpdump's classic packet capturing capabilities.
Why it is important
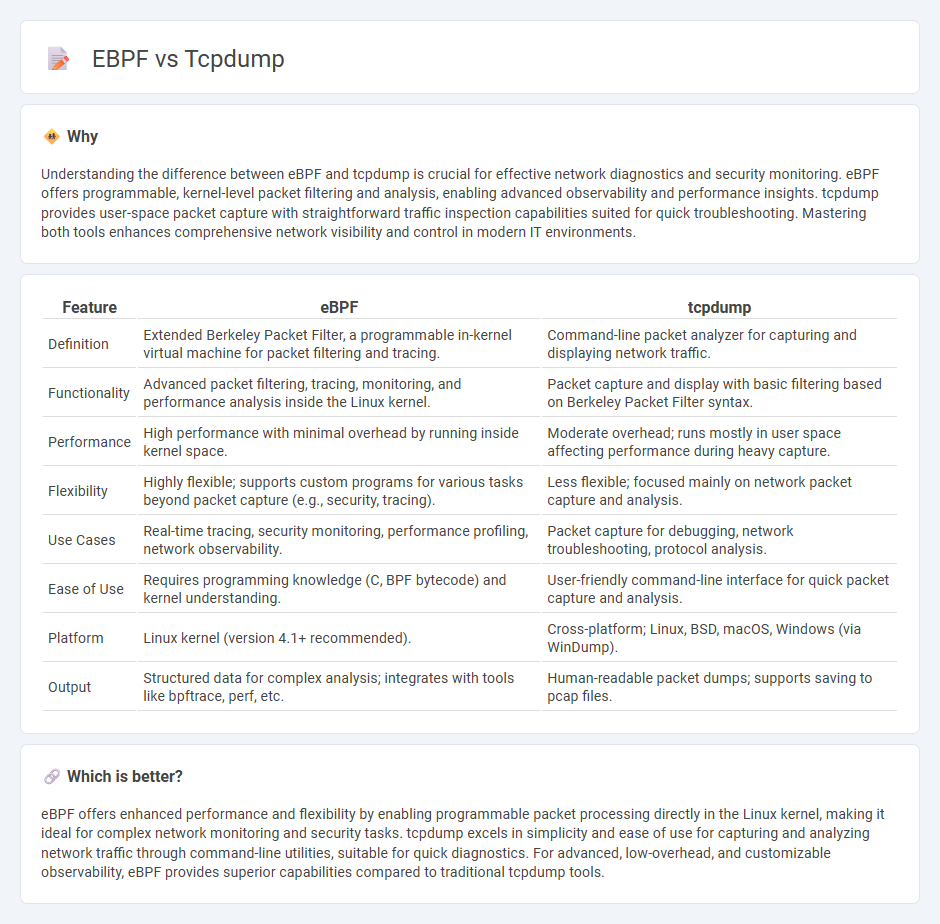
Understanding the difference between eBPF and tcpdump is crucial for effective network diagnostics and security monitoring. eBPF offers programmable, kernel-level packet filtering and analysis, enabling advanced observability and performance insights. tcpdump provides user-space packet capture with straightforward traffic inspection capabilities suited for quick troubleshooting. Mastering both tools enhances comprehensive network visibility and control in modern IT environments.
Comparison Table
| Feature | eBPF | tcpdump |
|---|---|---|
| Definition | Extended Berkeley Packet Filter, a programmable in-kernel virtual machine for packet filtering and tracing. | Command-line packet analyzer for capturing and displaying network traffic. |
| Functionality | Advanced packet filtering, tracing, monitoring, and performance analysis inside the Linux kernel. | Packet capture and display with basic filtering based on Berkeley Packet Filter syntax. |
| Performance | High performance with minimal overhead by running inside kernel space. | Moderate overhead; runs mostly in user space affecting performance during heavy capture. |
| Flexibility | Highly flexible; supports custom programs for various tasks beyond packet capture (e.g., security, tracing). | Less flexible; focused mainly on network packet capture and analysis. |
| Use Cases | Real-time tracing, security monitoring, performance profiling, network observability. | Packet capture for debugging, network troubleshooting, protocol analysis. |
| Ease of Use | Requires programming knowledge (C, BPF bytecode) and kernel understanding. | User-friendly command-line interface for quick packet capture and analysis. |
| Platform | Linux kernel (version 4.1+ recommended). | Cross-platform; Linux, BSD, macOS, Windows (via WinDump). |
| Output | Structured data for complex analysis; integrates with tools like bpftrace, perf, etc. | Human-readable packet dumps; supports saving to pcap files. |
Which is better?
eBPF offers enhanced performance and flexibility by enabling programmable packet processing directly in the Linux kernel, making it ideal for complex network monitoring and security tasks. tcpdump excels in simplicity and ease of use for capturing and analyzing network traffic through command-line utilities, suitable for quick diagnostics. For advanced, low-overhead, and customizable observability, eBPF provides superior capabilities compared to traditional tcpdump tools.
Connection
eBPF (extended Berkeley Packet Filter) enhances packet analysis by allowing programmable, efficient event tracing directly within the Linux kernel, which tcpdump leverages to capture and filter network traffic with high precision. Tcpdump uses the classic Berkeley Packet Filter (BPF) bytecode for filtering packets, while eBPF extends this capability enabling more complex, customizable, and safer kernel-level inspection and monitoring. The integration of eBPF into modern versions of tcpdump improves packet capture performance, detailed visibility, and dynamic filtering beyond traditional BPF limitations.
Key Terms
Packet Capture
TCPdump uses classic packet capture techniques via libpcap to monitor network traffic at the kernel level with broad compatibility and ease of use. eBPF offers advanced, programmable packet capture capabilities enabling deeper inspection, filtering, and real-time analytics directly within the Linux kernel for improved performance and flexibility. Explore how these tools transform network diagnostics by learning more about their packet capture strengths and use cases.
Kernel Space
tcpdump operates by capturing packets in kernel space and passing them to user space for analysis, which may introduce overhead and limit real-time processing capabilities. eBPF (extended Berkeley Packet Filter) executes custom programs directly within the Linux kernel, enabling more efficient packet filtering, monitoring, and performance tracing without context switching. Explore how leveraging eBPF can transform network diagnostics and security through deeper kernel-space insights.
Filtering
TCPdump uses traditional Berkeley Packet Filter (BPF) syntax for packet filtering, enabling users to define simple and clear capture rules based on IP addresses, ports, and protocols. eBPF offers advanced, programmable packet filtering within the Linux kernel, allowing for complex, dynamic filtering and processing beyond static rules, with higher performance and extensibility. Explore the differences and capabilities of tcpdump and eBPF to enhance your network monitoring strategies.
Source and External Links
TCPdump for Beginners: What It Is, How to Install, and Key Commands - This article provides an introduction to tcpdump, its installation, and key commands for capturing network traffic.
Tcpdump - Wikipedia - Tcpdump is a command-line network packet analyzer that runs on Unix-like systems, allowing users to display and analyze network traffic.
An Introduction to Using Tcpdump at the Linux Command Line - This blog post offers an overview of using tcpdump on Linux for network troubleshooting and analysis.
 dowidth.com
dowidth.com