Zero-knowledge proofs enable one party to prove knowledge of specific information without revealing the information itself, bolstering privacy in cryptographic protocols. Secure enclaves create isolated hardware environments that protect sensitive data and computations from unauthorized access, even from higher-privileged software. Explore how zero-knowledge proofs and secure enclaves complement each other to enhance data security in modern technology.
Why it is important
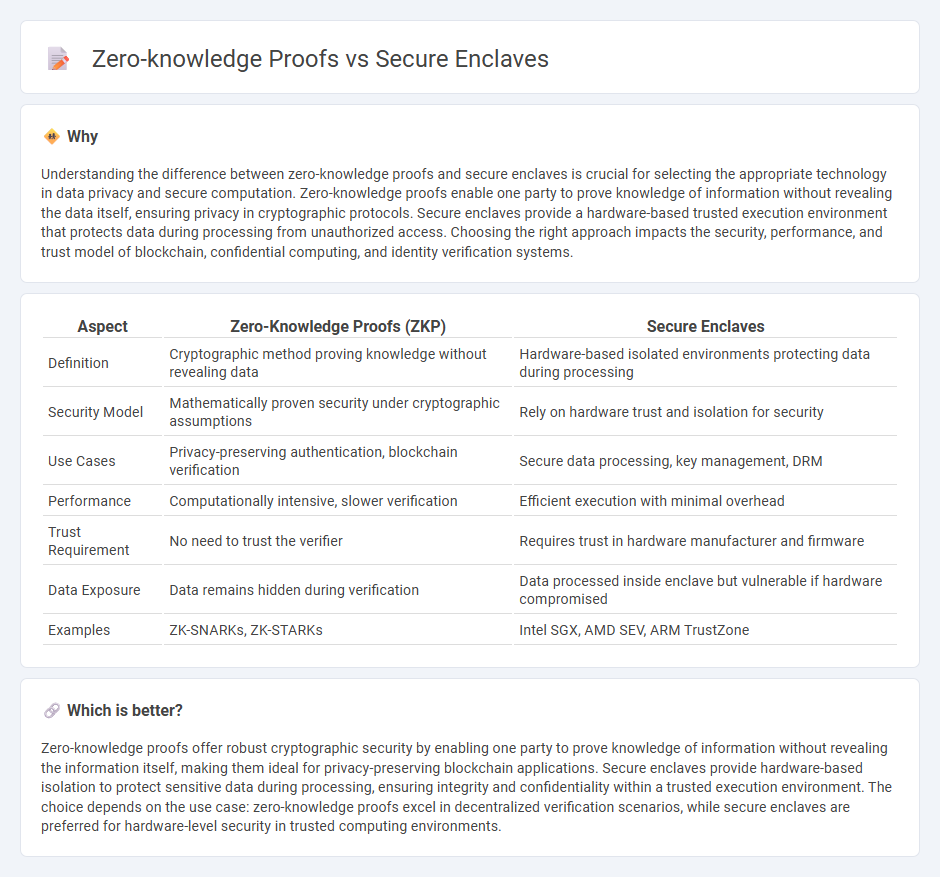
Understanding the difference between zero-knowledge proofs and secure enclaves is crucial for selecting the appropriate technology in data privacy and secure computation. Zero-knowledge proofs enable one party to prove knowledge of information without revealing the data itself, ensuring privacy in cryptographic protocols. Secure enclaves provide a hardware-based trusted execution environment that protects data during processing from unauthorized access. Choosing the right approach impacts the security, performance, and trust model of blockchain, confidential computing, and identity verification systems.
Comparison Table
| Aspect | Zero-Knowledge Proofs (ZKP) | Secure Enclaves |
|---|---|---|
| Definition | Cryptographic method proving knowledge without revealing data | Hardware-based isolated environments protecting data during processing |
| Security Model | Mathematically proven security under cryptographic assumptions | Rely on hardware trust and isolation for security |
| Use Cases | Privacy-preserving authentication, blockchain verification | Secure data processing, key management, DRM |
| Performance | Computationally intensive, slower verification | Efficient execution with minimal overhead |
| Trust Requirement | No need to trust the verifier | Requires trust in hardware manufacturer and firmware |
| Data Exposure | Data remains hidden during verification | Data processed inside enclave but vulnerable if hardware compromised |
| Examples | ZK-SNARKs, ZK-STARKs | Intel SGX, AMD SEV, ARM TrustZone |
Which is better?
Zero-knowledge proofs offer robust cryptographic security by enabling one party to prove knowledge of information without revealing the information itself, making them ideal for privacy-preserving blockchain applications. Secure enclaves provide hardware-based isolation to protect sensitive data during processing, ensuring integrity and confidentiality within a trusted execution environment. The choice depends on the use case: zero-knowledge proofs excel in decentralized verification scenarios, while secure enclaves are preferred for hardware-level security in trusted computing environments.
Connection
Zero-knowledge proofs enable one party to prove knowledge of a secret without revealing the secret itself, enhancing privacy in cryptographic protocols. Secure enclaves provide a hardware-based trusted execution environment that isolates sensitive computations from the main system. Combining zero-knowledge proofs with secure enclaves strengthens overall security by ensuring confidential data is processed in a protected environment while maintaining proof of integrity without data exposure.
Key Terms
Trusted Execution Environment (TEE)
Secure enclaves within a Trusted Execution Environment (TEE) provide hardware-based isolated environments to execute sensitive code and protect data from unauthorized access, ensuring confidentiality and integrity even if the operating system is compromised. Zero-knowledge proofs enable one party to prove knowledge of specific information without revealing the information itself, offering cryptographic security primarily for verification purposes rather than runtime code execution. Explore the detailed comparisons and use cases of TEEs and zero-knowledge proofs to understand which approach best fits your security requirements.
Cryptographic Proofs
Secure enclaves provide hardware-isolated environments that protect cryptographic keys and computations from unauthorized access, ensuring data confidentiality and integrity within the processor. Zero-knowledge proofs enable one party to prove knowledge of a cryptographic secret without revealing the secret itself, enhancing privacy through mathematical verification. Explore the nuances of these cryptographic proofs to strengthen your security strategies.
Data Confidentiality
Secure enclaves protect data confidentiality by isolating sensitive information within a hardware-based trusted execution environment, preventing unauthorized access even from privileged software. Zero-knowledge proofs ensure data confidentiality by allowing one party to prove knowledge of information without revealing the data itself, enabling secure verification without exposure. Discover how these advanced cryptographic technologies enhance privacy in modern computing.
Source and External Links
Secure Enclaves: The Powerful Way to Make Data Secure by Default - Secure enclaves are hardware-level encrypted memory environments within CPUs that isolate applications and data from the rest of the system, making them inaccessible even to system administrators or users with root or physical access.
What are secure enclaves? - Opaque Systems - Secure enclaves, also called trusted execution environments (TEEs), use hardware-based isolation to protect data and code from the operating system and other applications, preventing unauthorized access even by users with physical or administrative privileges.
Secure enclave: How it makes your devices safer - NordVPN - A secure enclave is a hardware-based trusted computing component on modern devices (such as smartphones and laptops) that securely stores and processes sensitive data like biometrics and encryption keys, separate from the main operating system.
 dowidth.com
dowidth.com