Quantum-safe cryptography utilizes complex algorithms designed to withstand attacks from quantum computers, offering enhanced security compared to traditional symmetric-key cryptography that relies on shared secret keys vulnerable to quantum decryption methods like Shor's algorithm. Symmetric-key cryptography, including AES and DES, remains efficient for current encryption needs but faces future risks as quantum computing advances threaten the integrity of cryptographic protocols. Explore the evolving landscape of cryptographic techniques to understand how quantum-safe solutions are shaping next-generation cybersecurity.
Why it is important
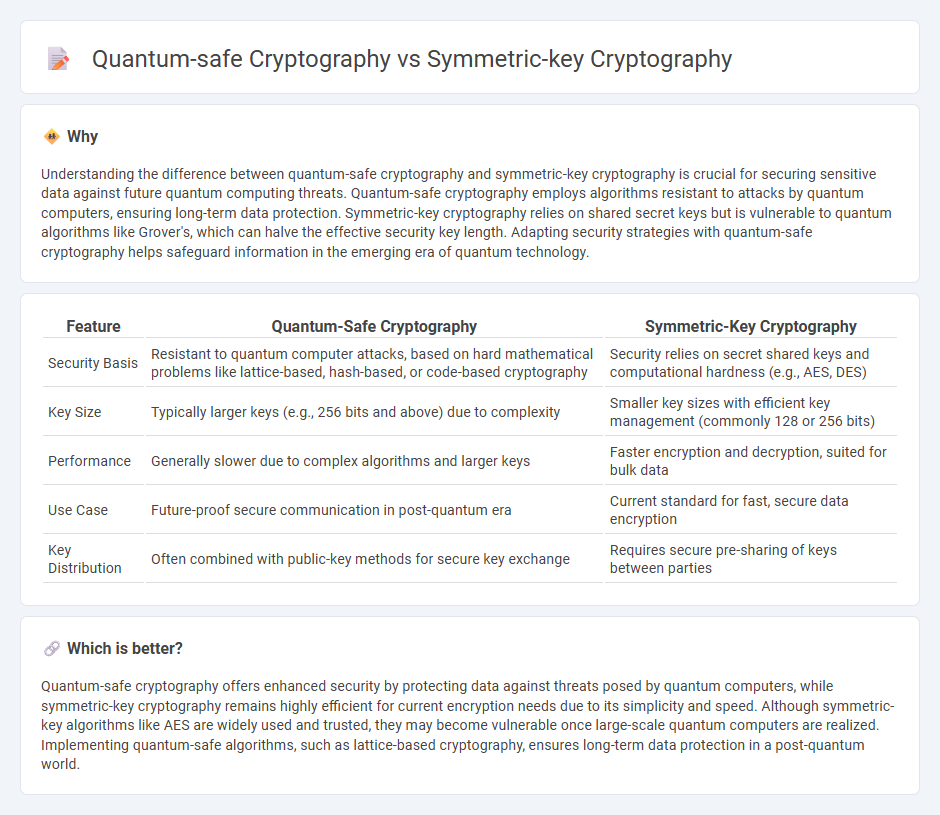
Understanding the difference between quantum-safe cryptography and symmetric-key cryptography is crucial for securing sensitive data against future quantum computing threats. Quantum-safe cryptography employs algorithms resistant to attacks by quantum computers, ensuring long-term data protection. Symmetric-key cryptography relies on shared secret keys but is vulnerable to quantum algorithms like Grover's, which can halve the effective security key length. Adapting security strategies with quantum-safe cryptography helps safeguard information in the emerging era of quantum technology.
Comparison Table
| Feature | Quantum-Safe Cryptography | Symmetric-Key Cryptography |
|---|---|---|
| Security Basis | Resistant to quantum computer attacks, based on hard mathematical problems like lattice-based, hash-based, or code-based cryptography | Security relies on secret shared keys and computational hardness (e.g., AES, DES) |
| Key Size | Typically larger keys (e.g., 256 bits and above) due to complexity | Smaller key sizes with efficient key management (commonly 128 or 256 bits) |
| Performance | Generally slower due to complex algorithms and larger keys | Faster encryption and decryption, suited for bulk data |
| Use Case | Future-proof secure communication in post-quantum era | Current standard for fast, secure data encryption |
| Key Distribution | Often combined with public-key methods for secure key exchange | Requires secure pre-sharing of keys between parties |
Which is better?
Quantum-safe cryptography offers enhanced security by protecting data against threats posed by quantum computers, while symmetric-key cryptography remains highly efficient for current encryption needs due to its simplicity and speed. Although symmetric-key algorithms like AES are widely used and trusted, they may become vulnerable once large-scale quantum computers are realized. Implementing quantum-safe algorithms, such as lattice-based cryptography, ensures long-term data protection in a post-quantum world.
Connection
Quantum-safe cryptography leverages Symmetric-key cryptography principles to ensure data security against quantum computing attacks by using algorithms such as AES and SHA-3 that remain resilient to quantum algorithms like Grover's. Symmetric-key cryptography provides the foundation for quantum-resistant protocols by relying on shared secret keys that quantum adversaries cannot efficiently break without exponential time. The integration of symmetric-key techniques into quantum-safe cryptographic methods is essential for protecting confidential communications and maintaining integrity in the era of advancing quantum technologies.
Key Terms
Shared secret key
Symmetric-key cryptography relies on a shared secret key for both encryption and decryption, making key distribution and management critical challenges, especially as computational power increases. Quantum-safe cryptography, also known as post-quantum cryptography, incorporates algorithms designed to resist attacks from quantum computers while still often depending on shared secret keys or hybrid approaches to maintain security. Explore the latest advancements and practical implementations in shared secret key management within quantum-safe cryptographic frameworks.
Quantum computing
Symmetric-key cryptography relies on shared secret keys and is currently considered secure against quantum attacks if key lengths are sufficiently increased, such as using AES-256 to resist Grover's algorithm. Quantum-safe cryptography, also known as post-quantum cryptography, involves algorithms designed to be secure against quantum computers, focusing on lattice-based, hash-based, and code-based cryptographic schemes. Explore the latest advancements in quantum computing and cryptographic solutions to better understand the future of data security.
Post-quantum algorithms
Post-quantum algorithms in cryptography aim to secure data against threats posed by quantum computers, which can break many symmetric-key schemes relying on traditional hardness assumptions. These algorithms, based on lattice problems, code-based cryptography, and hash-based signatures, provide robust security that classical symmetric-key cryptography cannot guarantee once large-scale quantum computers are realized. Explore the latest advancements in post-quantum cryptographic standards and their implementation challenges to understand the future of data security.
Source and External Links
Symmetric Key Algorithms - Tutorials Point - Symmetric key cryptography uses the same secret key for both encrypting and decrypting messages, enabling fast and efficient secure communication but requiring secure key distribution between sender and receiver.
Symmetric-key algorithm - Wikipedia - Symmetric-key algorithms employ identical or easily transformable keys for encryption and decryption, making them ideal for bulk data encryption, though the need to share the secret key is a major limitation compared to public-key cryptography.
What is Symmetric Key Cryptography? | Security Encyclopedia - HYPR - Symmetric key cryptography relies on a single secret key for both encryption and decryption, is widely used for fast data protection, but requires both parties to securely manage and exchange the key.
 dowidth.com
dowidth.com