Zero Trust Architecture enforces strict identity verification for every user and device attempting to access resources, eliminating implicit trust within a network. Secure Access Service Edge (SASE) combines network security functions with wide-area networking capabilities to deliver secure access to users based on identity, location, and device context. Explore how these innovative frameworks enhance cybersecurity resilience and transform enterprise network strategies.
Why it is important
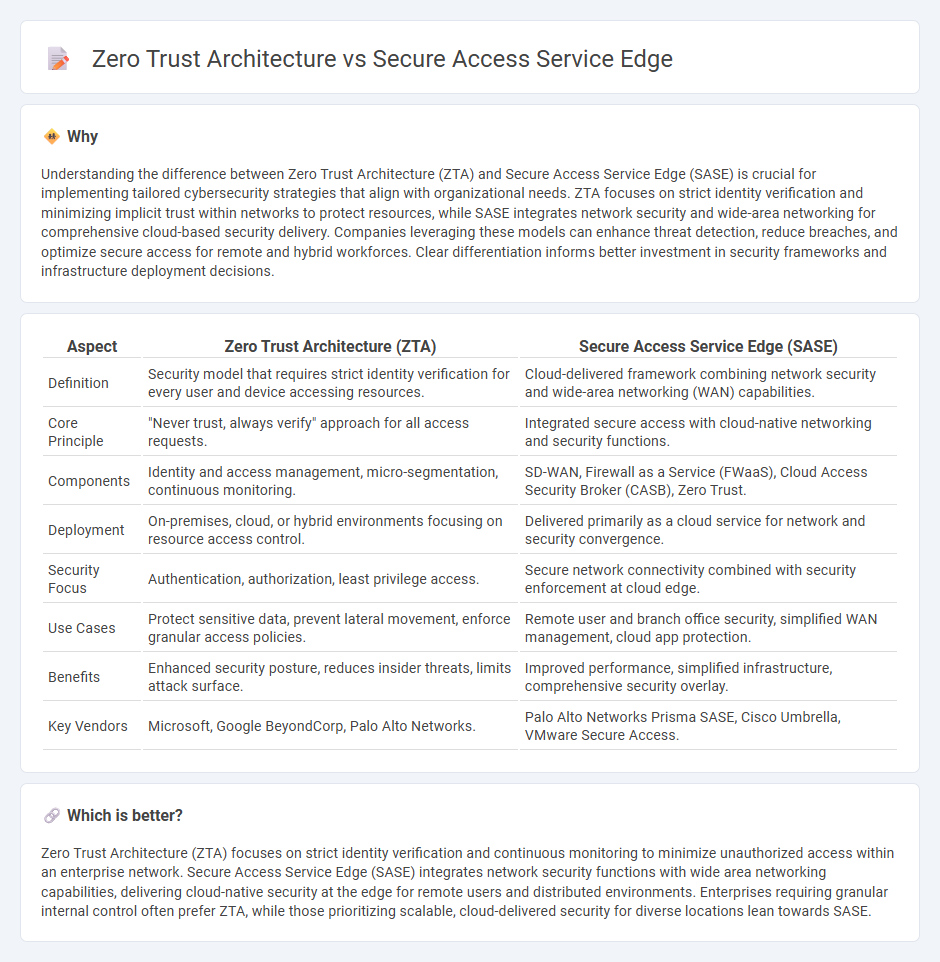
Understanding the difference between Zero Trust Architecture (ZTA) and Secure Access Service Edge (SASE) is crucial for implementing tailored cybersecurity strategies that align with organizational needs. ZTA focuses on strict identity verification and minimizing implicit trust within networks to protect resources, while SASE integrates network security and wide-area networking for comprehensive cloud-based security delivery. Companies leveraging these models can enhance threat detection, reduce breaches, and optimize secure access for remote and hybrid workforces. Clear differentiation informs better investment in security frameworks and infrastructure deployment decisions.
Comparison Table
| Aspect | Zero Trust Architecture (ZTA) | Secure Access Service Edge (SASE) |
|---|---|---|
| Definition | Security model that requires strict identity verification for every user and device accessing resources. | Cloud-delivered framework combining network security and wide-area networking (WAN) capabilities. |
| Core Principle | "Never trust, always verify" approach for all access requests. | Integrated secure access with cloud-native networking and security functions. |
| Components | Identity and access management, micro-segmentation, continuous monitoring. | SD-WAN, Firewall as a Service (FWaaS), Cloud Access Security Broker (CASB), Zero Trust. |
| Deployment | On-premises, cloud, or hybrid environments focusing on resource access control. | Delivered primarily as a cloud service for network and security convergence. |
| Security Focus | Authentication, authorization, least privilege access. | Secure network connectivity combined with security enforcement at cloud edge. |
| Use Cases | Protect sensitive data, prevent lateral movement, enforce granular access policies. | Remote user and branch office security, simplified WAN management, cloud app protection. |
| Benefits | Enhanced security posture, reduces insider threats, limits attack surface. | Improved performance, simplified infrastructure, comprehensive security overlay. |
| Key Vendors | Microsoft, Google BeyondCorp, Palo Alto Networks. | Palo Alto Networks Prisma SASE, Cisco Umbrella, VMware Secure Access. |
Which is better?
Zero Trust Architecture (ZTA) focuses on strict identity verification and continuous monitoring to minimize unauthorized access within an enterprise network. Secure Access Service Edge (SASE) integrates network security functions with wide area networking capabilities, delivering cloud-native security at the edge for remote users and distributed environments. Enterprises requiring granular internal control often prefer ZTA, while those prioritizing scalable, cloud-delivered security for diverse locations lean towards SASE.
Connection
Zero Trust Architecture (ZTA) and Secure Access Service Edge (SASE) intersect by reinforcing security through continuous verification and policy enforcement at the network edge, ensuring that every access request is authenticated and authorized regardless of location. SASE integrates networking and security functions like secure web gateways, firewall-as-a-service, and zero trust network access into a unified cloud-delivered service, enabling seamless implementation of Zero Trust principles. This combination mitigates risks from remote work, cloud adoption, and evolving cyber threats by minimizing trust zones and providing context-aware security policies.
Key Terms
Network Security
Secure Access Service Edge (SASE) integrates network security functions with wide-area networking capabilities, delivering cloud-native security such as secure web gateways, firewall-as-a-service, and zero trust network access in a unified framework. Zero Trust Architecture (ZTA) centers on strict identity verification and continuous validation of user and device trust levels, minimizing attack surfaces by assuming no implicit trust within or outside the network perimeter. Explore in-depth comparisons and implementation strategies to strengthen your organization's network security posture effectively.
Identity Verification
Secure Access Service Edge (SASE) integrates identity verification by enforcing user authentication and policy-based access at the network edge, providing seamless security across distributed environments. Zero Trust Architecture (ZTA) emphasizes strict identity verification through continuous authentication and authorization, ensuring that no user or device is trusted by default regardless of location. Explore the detailed differences in identity verification approaches between SASE and ZTA to enhance your cybersecurity strategy.
Cloud Integration
Secure Access Service Edge (SASE) integrates network security functions with cloud-native architecture to enhance secure access to distributed cloud resources, leveraging technologies like SD-WAN and cloud security gateways. Zero Trust Architecture (ZTA) enforces strict identity verification and least privilege access across users and devices, focusing on continuous authentication in dynamic cloud environments. Explore more to understand how SASE and ZTA complement each other in optimizing cloud integration and security.
Source and External Links
Secure access service edge - Wikipedia - SASE is a cloud-based technology that delivers WAN and security controls directly to users or edge devices, combining SD-WAN with network security functions like CASB, FWaaS, and VPN as a single cloud service close to dispersed users, improving network performance and security based on digital identity and real-time context rather than traditional hardware appliances.
What is SASE? Secure Access Service Edge - Cato Networks - SASE unifies SD-WAN, a Cloud Network, and Security Service Edge functions including FWaaS, CASB, DLP, SWG, and ZTNA into a cloud-native service to optimize network routing, enhance security posture, enable secure work from anywhere, and reduce infrastructure complexity.
What is SASE? | Secure access service edge - Cloudflare - SASE is a cloud-based architecture that integrates networking and security services on a single platform at the cloud edge, enabling secure, simple, and consistent access for users to applications from any location, using Zero Trust security principles and cloud edge points instead of corporate data centers.
 dowidth.com
dowidth.com