Quantum-safe cryptography uses mathematical algorithms resistant to quantum computer attacks, ensuring data security in a post-quantum era. Homomorphic encryption enables computation on encrypted data without decryption, preserving privacy while allowing secure data processing. Explore the nuances of these groundbreaking technologies to understand their implications for future cybersecurity.
Why it is important
Understanding the difference between quantum-safe cryptography and homomorphic encryption is essential for securing data against future quantum attacks while enabling computation on encrypted data without compromising privacy. Quantum-safe cryptography focuses on developing algorithms resistant to quantum computers, ensuring long-term data confidentiality. Homomorphic encryption allows processing encrypted information directly, providing secure data analytics and cloud computing capabilities. Distinguishing these technologies enables organizations to implement robust, future-proof security strategies tailored to specific needs.
Comparison Table
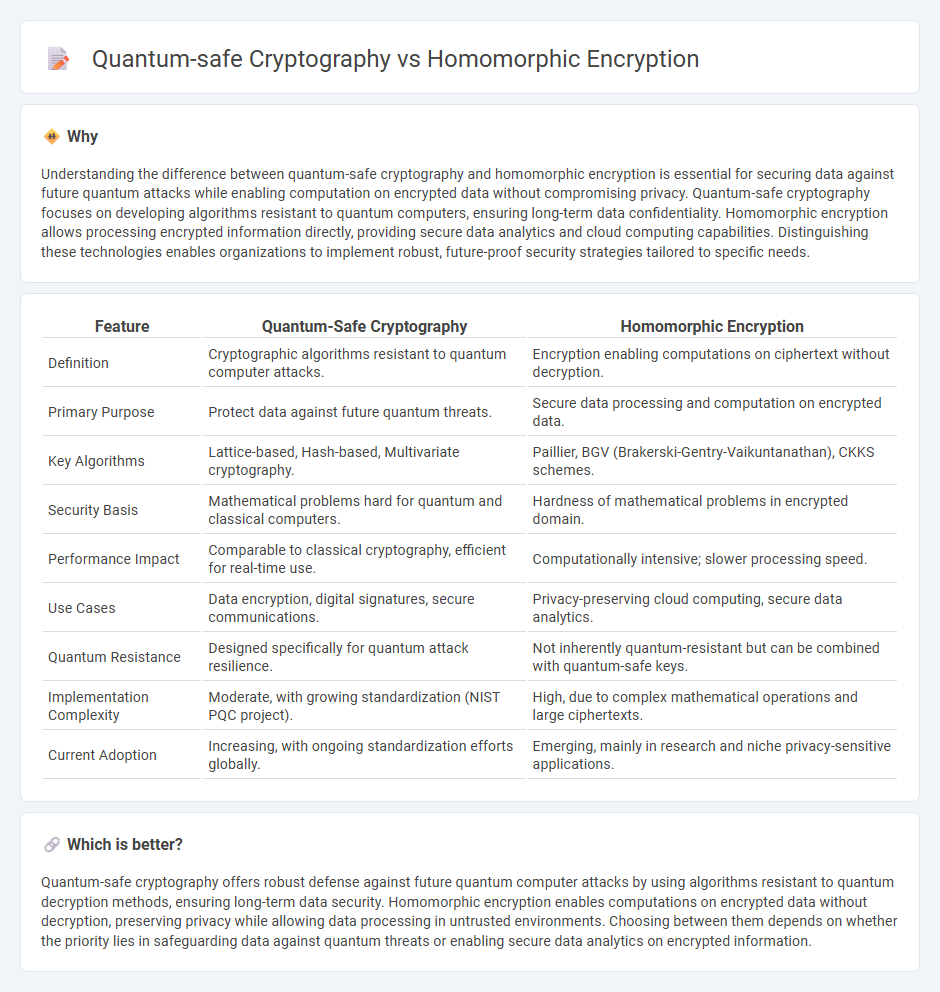
| Feature | Quantum-Safe Cryptography | Homomorphic Encryption |
|---|---|---|
| Definition | Cryptographic algorithms resistant to quantum computer attacks. | Encryption enabling computations on ciphertext without decryption. |
| Primary Purpose | Protect data against future quantum threats. | Secure data processing and computation on encrypted data. |
| Key Algorithms | Lattice-based, Hash-based, Multivariate cryptography. | Paillier, BGV (Brakerski-Gentry-Vaikuntanathan), CKKS schemes. |
| Security Basis | Mathematical problems hard for quantum and classical computers. | Hardness of mathematical problems in encrypted domain. |
| Performance Impact | Comparable to classical cryptography, efficient for real-time use. | Computationally intensive; slower processing speed. |
| Use Cases | Data encryption, digital signatures, secure communications. | Privacy-preserving cloud computing, secure data analytics. |
| Quantum Resistance | Designed specifically for quantum attack resilience. | Not inherently quantum-resistant but can be combined with quantum-safe keys. |
| Implementation Complexity | Moderate, with growing standardization (NIST PQC project). | High, due to complex mathematical operations and large ciphertexts. |
| Current Adoption | Increasing, with ongoing standardization efforts globally. | Emerging, mainly in research and niche privacy-sensitive applications. |
Which is better?
Quantum-safe cryptography offers robust defense against future quantum computer attacks by using algorithms resistant to quantum decryption methods, ensuring long-term data security. Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy while allowing data processing in untrusted environments. Choosing between them depends on whether the priority lies in safeguarding data against quantum threats or enabling secure data analytics on encrypted information.
Connection
Quantum-safe cryptography and homomorphic encryption both address future-proof data security in the era of quantum computing. Quantum-safe cryptography develops algorithms resistant to quantum attacks, ensuring secure data transmission, while homomorphic encryption enables computation on encrypted data without exposing sensitive information. Integrating these technologies can create robust systems that maintain privacy and integrity against emerging quantum threats.
Key Terms
Fully Homomorphic Encryption (FHE)
Fully Homomorphic Encryption (FHE) enables computations on encrypted data without decryption, preserving privacy in cloud computing and secure data processing. Quantum-safe cryptography includes diverse methods, such as lattice-based schemes, that resist attacks from quantum computers, ensuring future-proof data security. Explore how FHE and quantum-safe cryptographic algorithms complement each other to enhance secure, privacy-preserving computing environments.
Post-Quantum Cryptography (PQC)
Homomorphic encryption enables computations on encrypted data without decryption, ensuring data privacy in cloud computing and secure multi-party computations. Quantum-safe cryptography, particularly Post-Quantum Cryptography (PQC), develops algorithms resistant to quantum attacks, safeguarding data against threats posed by quantum computers. Explore the latest advances in PQC and homomorphic encryption to secure your data against evolving cyber threats.
Lattice-Based Cryptography
Lattice-based cryptography represents a leading approach in quantum-safe cryptographic solutions, offering resistance against attacks from quantum computers by relying on the hardness of lattice problems like Learning With Errors (LWE). Homomorphic encryption schemes built on lattice-based assumptions enable computations on encrypted data without decryption, combining data privacy with quantum resistance. Explore the advancements in lattice-based cryptography to understand how it secures the future of encrypted computing.
Source and External Links
Homomorphic encryption - Homomorphic encryption allows computations to be performed on encrypted data without decrypting it, enabling privacy-preserving operations across various encryption schemes with varying computational capabilities.
What is homomorphic encryption, and why isn't it ... - Homomorphic encryption algorithms enable mathematical operations on encrypted data, maintaining confidentiality even when data is in use, which is a unique challenge compared to traditional encryption.
What Is Homomorphic Encryption? - Homomorphic encryption comes in several types, ranging from partially homomorphic (one operation), somewhat homomorphic (limited operations), to fully homomorphic (unlimited operations), though practical use is limited by computational costs.
 dowidth.com
dowidth.com