Quantum key distribution leverages the principles of quantum mechanics to enable secure communication by detecting eavesdropping attempts, making it a cutting-edge solution for cryptographic key exchange. Hardware security modules are physical devices designed to protect and manage digital keys securely, offering tamper-resistant environments for encryption and decryption processes. Explore the benefits and differences between quantum key distribution and hardware security modules to enhance your understanding of advanced cybersecurity technologies.
Why it is important
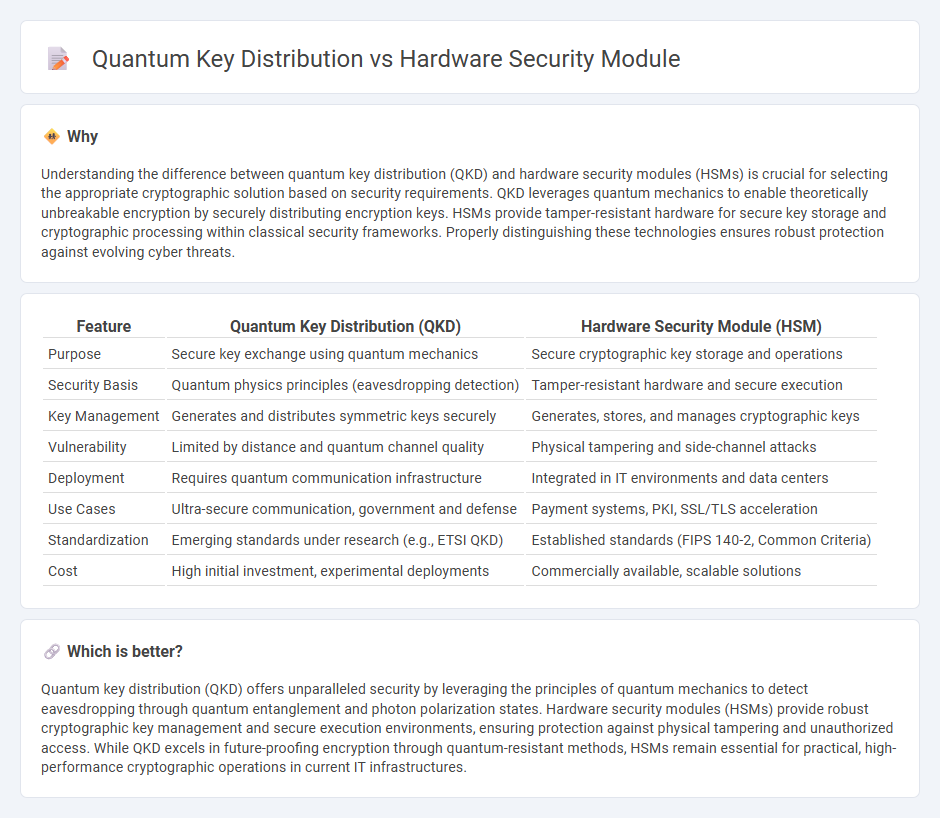
Understanding the difference between quantum key distribution (QKD) and hardware security modules (HSMs) is crucial for selecting the appropriate cryptographic solution based on security requirements. QKD leverages quantum mechanics to enable theoretically unbreakable encryption by securely distributing encryption keys. HSMs provide tamper-resistant hardware for secure key storage and cryptographic processing within classical security frameworks. Properly distinguishing these technologies ensures robust protection against evolving cyber threats.
Comparison Table
| Feature | Quantum Key Distribution (QKD) | Hardware Security Module (HSM) |
|---|---|---|
| Purpose | Secure key exchange using quantum mechanics | Secure cryptographic key storage and operations |
| Security Basis | Quantum physics principles (eavesdropping detection) | Tamper-resistant hardware and secure execution |
| Key Management | Generates and distributes symmetric keys securely | Generates, stores, and manages cryptographic keys |
| Vulnerability | Limited by distance and quantum channel quality | Physical tampering and side-channel attacks |
| Deployment | Requires quantum communication infrastructure | Integrated in IT environments and data centers |
| Use Cases | Ultra-secure communication, government and defense | Payment systems, PKI, SSL/TLS acceleration |
| Standardization | Emerging standards under research (e.g., ETSI QKD) | Established standards (FIPS 140-2, Common Criteria) |
| Cost | High initial investment, experimental deployments | Commercially available, scalable solutions |
Which is better?
Quantum key distribution (QKD) offers unparalleled security by leveraging the principles of quantum mechanics to detect eavesdropping through quantum entanglement and photon polarization states. Hardware security modules (HSMs) provide robust cryptographic key management and secure execution environments, ensuring protection against physical tampering and unauthorized access. While QKD excels in future-proofing encryption through quantum-resistant methods, HSMs remain essential for practical, high-performance cryptographic operations in current IT infrastructures.
Connection
Quantum key distribution (QKD) enhances the security of Hardware Security Modules (HSMs) by enabling the generation and exchange of cryptographic keys through quantum mechanics, ensuring theoretically unbreakable encryption. HSMs utilize these quantum-generated keys to safeguard sensitive operations such as cryptographic key storage, digital signing, and authentication processes. The integration of QKD with HSMs strengthens hardware-based security frameworks, protecting critical data against advanced cyber threats and quantum computing attacks.
Key Terms
Cryptographic keys
Hardware Security Modules (HSMs) provide physical and logical protection for cryptographic keys, ensuring secure key generation, storage, and management within a tamper-resistant environment. Quantum Key Distribution (QKD) leverages quantum mechanics principles to enable secure key exchange, delivering theoretically unbreakable cryptographic keys but requiring specialized quantum communication infrastructure. Explore detailed comparisons to understand their roles in enhancing cryptographic key security in modern cybersecurity frameworks.
Tamper resistance
Hardware Security Modules (HSMs) provide tamper resistance through physical barriers, sensors, and secure enclosures designed to detect and respond to unauthorized access attempts, ensuring cryptographic keys remain protected within a secure environment. Quantum Key Distribution (QKD) offers tamper resistance by leveraging quantum mechanics principles, where any eavesdropping attempt on the quantum channel alters the quantum state and is thus instantly detectable, guaranteeing the integrity of key exchange. Explore in-depth comparisons of HSM tamper resistance technologies and QKD's quantum safeguards to understand their distinct security models.
Quantum entanglement
Hardware security modules (HSMs) provide secure key storage and cryptographic processing using classical hardware and algorithms, while quantum key distribution (QKD) leverages quantum entanglement to enable theoretically unhackable communication by detecting eavesdropping through quantum state disturbances. Quantum entanglement in QKD ensures that any interception attempt alters the entangled particles' states, instantly signaling a breach and guaranteeing the integrity of key exchange beyond classical security limits. Explore how quantum entanglement fundamentally transforms secure communications compared to traditional HSM approaches.
Source and External Links
Hardware security module - Wikipedia - A hardware security module (HSM) is a physical computing device designed to safeguard and manage digital keys and perform encryption, decryption, authentication, and other cryptographic functions within a tamper-resistant environment, often implemented as plug-in cards or external devices containing secure cryptoprocessors.
Hardware Security Modules (HSMs) | Thales Group - Thales HSMs are dedicated crypto processors that protect the cryptographic key lifecycle by securely managing, processing, and storing keys inside tamper-evident, intrusion-resistant hardware, serving as trust anchors for encryption, digital signing, and authentication in security-critical applications.
What is a Hardware Security Module? | TechTarget - An HSM is a physical device providing a hardened, isolated environment to protect sensitive cryptographic keys and perform secure cryptographic operations, essential for safeguarding data in applications such as banking, payments, and identity verification by preventing key exposure even from authorized users.
 dowidth.com
dowidth.com