Post-quantum cryptography enhances data protection by developing algorithms resistant to quantum computer attacks, addressing vulnerabilities in current encryption methods. Blockchain security relies on cryptographic techniques like hashing and digital signatures, which quantum computing threatens due to its capacity to solve complex problems faster. Explore how emerging post-quantum cryptographic solutions can safeguard blockchain technology against future quantum threats.
Why it is important
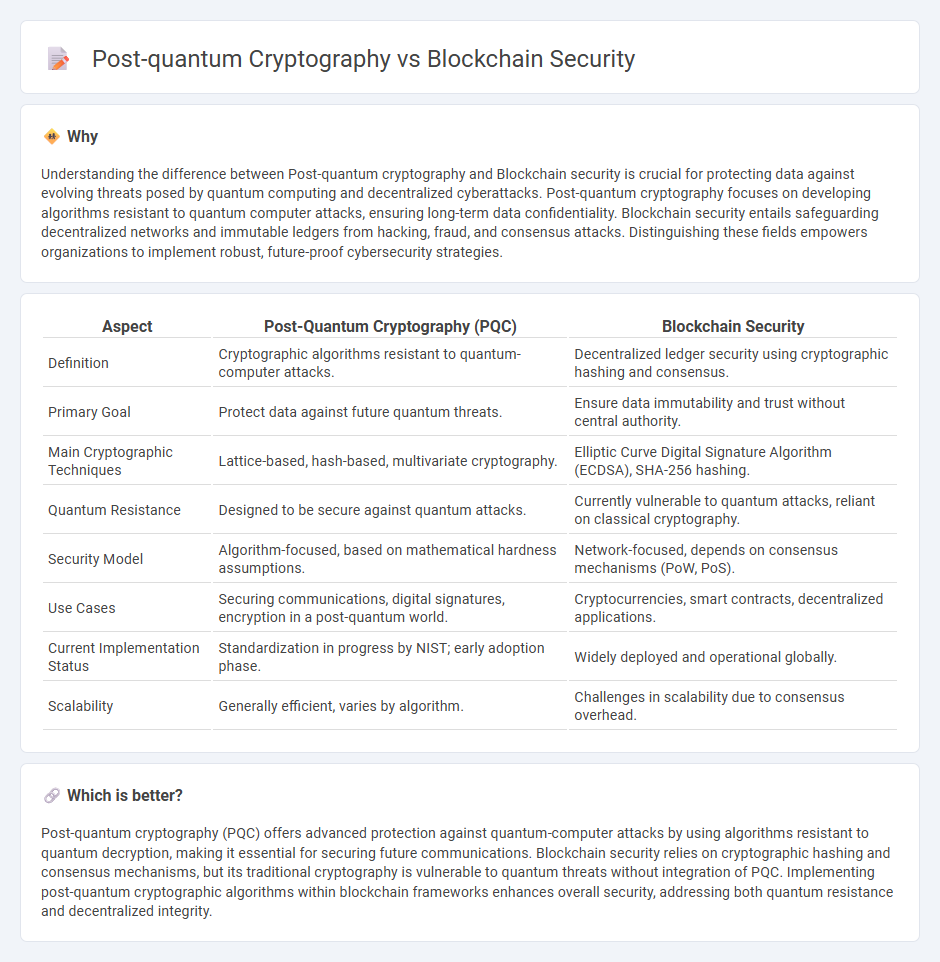
Understanding the difference between Post-quantum cryptography and Blockchain security is crucial for protecting data against evolving threats posed by quantum computing and decentralized cyberattacks. Post-quantum cryptography focuses on developing algorithms resistant to quantum computer attacks, ensuring long-term data confidentiality. Blockchain security entails safeguarding decentralized networks and immutable ledgers from hacking, fraud, and consensus attacks. Distinguishing these fields empowers organizations to implement robust, future-proof cybersecurity strategies.
Comparison Table
| Aspect | Post-Quantum Cryptography (PQC) | Blockchain Security |
|---|---|---|
| Definition | Cryptographic algorithms resistant to quantum-computer attacks. | Decentralized ledger security using cryptographic hashing and consensus. |
| Primary Goal | Protect data against future quantum threats. | Ensure data immutability and trust without central authority. |
| Main Cryptographic Techniques | Lattice-based, hash-based, multivariate cryptography. | Elliptic Curve Digital Signature Algorithm (ECDSA), SHA-256 hashing. |
| Quantum Resistance | Designed to be secure against quantum attacks. | Currently vulnerable to quantum attacks, reliant on classical cryptography. |
| Security Model | Algorithm-focused, based on mathematical hardness assumptions. | Network-focused, depends on consensus mechanisms (PoW, PoS). |
| Use Cases | Securing communications, digital signatures, encryption in a post-quantum world. | Cryptocurrencies, smart contracts, decentralized applications. |
| Current Implementation Status | Standardization in progress by NIST; early adoption phase. | Widely deployed and operational globally. |
| Scalability | Generally efficient, varies by algorithm. | Challenges in scalability due to consensus overhead. |
Which is better?
Post-quantum cryptography (PQC) offers advanced protection against quantum-computer attacks by using algorithms resistant to quantum decryption, making it essential for securing future communications. Blockchain security relies on cryptographic hashing and consensus mechanisms, but its traditional cryptography is vulnerable to quantum threats without integration of PQC. Implementing post-quantum cryptographic algorithms within blockchain frameworks enhances overall security, addressing both quantum resistance and decentralized integrity.
Connection
Post-quantum cryptography (PQC) enhances blockchain security by providing cryptographic algorithms resistant to quantum computing attacks, safeguarding data integrity in decentralized ledgers. Integrating PQC into blockchain protocols prevents vulnerabilities that quantum computers could exploit, ensuring the longevity of secure transactions. This synergy addresses future threats by enabling quantum-resistant consensus mechanisms and secure key management within blockchain networks.
Key Terms
Consensus Algorithms
Consensus algorithms like Proof of Work (PoW) and Proof of Stake (PoS) play crucial roles in blockchain security by validating transactions and maintaining network integrity against attacks. Post-quantum cryptography introduces quantum-resistant algorithms aimed at securing cryptographic primitives within consensus mechanisms, protecting against threats posed by quantum computers. Explore advancements in quantum-safe consensus protocols to understand how blockchain systems can evolve for future resilience.
Quantum-resistant Algorithms
Quantum-resistant algorithms are essential for safeguarding blockchain security against future quantum computer threats, which can potentially break classical cryptographic schemes like RSA and ECC. Lattice-based, hash-based, and code-based cryptographic algorithms are the leading candidates designed to withstand quantum attacks and ensure data integrity and confidentiality within decentralized networks. Explore the latest advancements in quantum-resistant blockchain technologies to understand how they secure the digital future.
Cryptographic Hash Functions
Cryptographic hash functions play a critical role in blockchain security by ensuring data integrity and enabling secure transaction verification; however, their resistance to quantum attacks remains a pivotal concern as quantum computers threaten to undermine classical cryptographic assumptions. Post-quantum cryptography introduces hash functions specifically designed to withstand quantum adversaries, leveraging algorithms like lattice-based and multivariate polynomial schemes that maintain collision resistance and preimage resistance under quantum computational models. Explore the evolving landscape of cryptographic hash functions in blockchain and learn how post-quantum algorithms are shaping the future of secure decentralized systems.
Source and External Links
Blockchain Security: Essential Measures and Beyond - McAfee - Blockchain security ensures data integrity and authenticity via cryptographic hashes, secures IoT devices by decentralizing data, and streamlines identity management by eliminating centralized repositories, making fraud and cyber threats computationally infeasible.
What Is Blockchain Security? | IBM - Blockchain security is a comprehensive risk management system using cryptography, decentralization, and consensus mechanisms to prevent tampering and fraud, with distinctions between public (open access) and private (restricted access) blockchains impacting their security models.
Blockchain Security: Preventing Threats Before They Strike - Blockchain security combines cybersecurity tools and practices to prevent unauthorized access and attacks, highlighting that public blockchains rely on open source vetting and decentralization for security, while private blockchains depend on institutional controls and have a single point of failure risk.
 dowidth.com
dowidth.com