Quantum key distribution (QKD) leverages the principles of quantum mechanics to enable secure communication by detecting eavesdropping through quantum states, offering theoretically unbreakable encryption. In contrast, classical key exchange relies on mathematical algorithms like RSA and Diffie-Hellman, whose security depends on computational complexity and can be vulnerable to advances in computing power. Discover how these methods transform data security and what the future holds for cryptographic technologies.
Why it is important
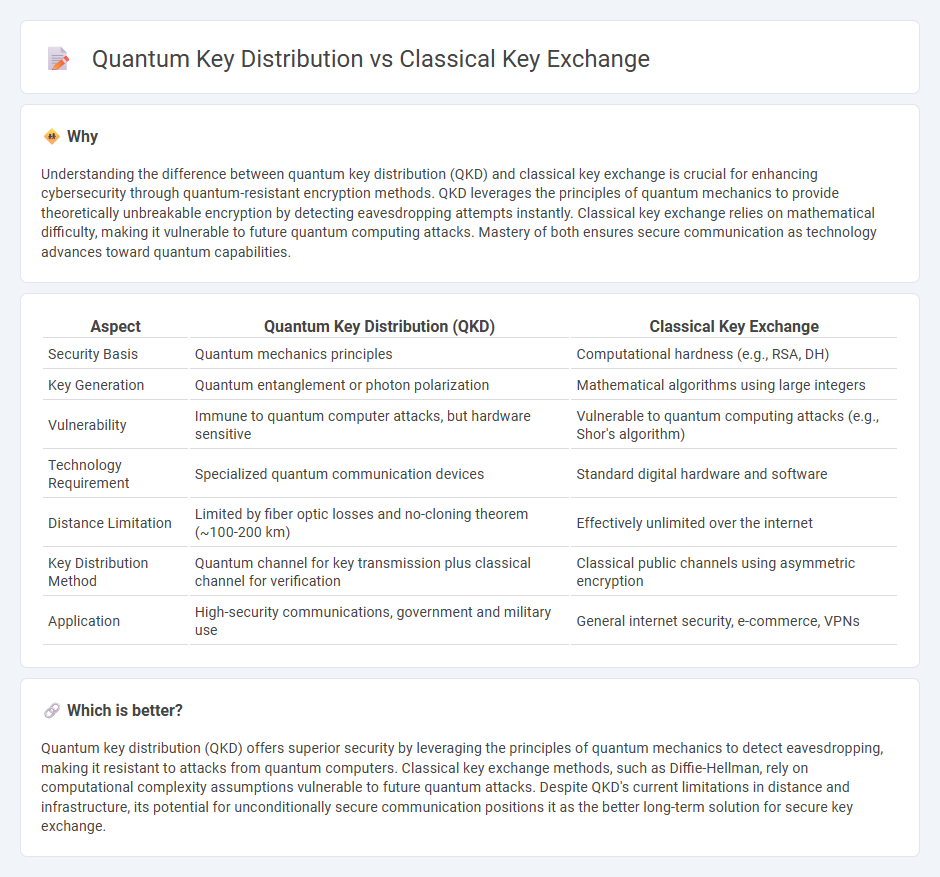
Understanding the difference between quantum key distribution (QKD) and classical key exchange is crucial for enhancing cybersecurity through quantum-resistant encryption methods. QKD leverages the principles of quantum mechanics to provide theoretically unbreakable encryption by detecting eavesdropping attempts instantly. Classical key exchange relies on mathematical difficulty, making it vulnerable to future quantum computing attacks. Mastery of both ensures secure communication as technology advances toward quantum capabilities.
Comparison Table
| Aspect | Quantum Key Distribution (QKD) | Classical Key Exchange |
|---|---|---|
| Security Basis | Quantum mechanics principles | Computational hardness (e.g., RSA, DH) |
| Key Generation | Quantum entanglement or photon polarization | Mathematical algorithms using large integers |
| Vulnerability | Immune to quantum computer attacks, but hardware sensitive | Vulnerable to quantum computing attacks (e.g., Shor's algorithm) |
| Technology Requirement | Specialized quantum communication devices | Standard digital hardware and software |
| Distance Limitation | Limited by fiber optic losses and no-cloning theorem (~100-200 km) | Effectively unlimited over the internet |
| Key Distribution Method | Quantum channel for key transmission plus classical channel for verification | Classical public channels using asymmetric encryption |
| Application | High-security communications, government and military use | General internet security, e-commerce, VPNs |
Which is better?
Quantum key distribution (QKD) offers superior security by leveraging the principles of quantum mechanics to detect eavesdropping, making it resistant to attacks from quantum computers. Classical key exchange methods, such as Diffie-Hellman, rely on computational complexity assumptions vulnerable to future quantum attacks. Despite QKD's current limitations in distance and infrastructure, its potential for unconditionally secure communication positions it as the better long-term solution for secure key exchange.
Connection
Quantum key distribution (QKD) leverages quantum mechanics principles to securely exchange cryptographic keys, ensuring eavesdropping is detectable. Classical key exchange methods like Diffie-Hellman rely on mathematical complexity for security but remain vulnerable to future quantum attacks. Integrating QKD with classical key exchange protocols enhances overall communication security by combining quantum-resistant techniques with established classical frameworks.
Key Terms
Public Key Cryptography
Public key cryptography relies on mathematical problems like integer factorization and discrete logarithms, which classical key exchange protocols such as RSA and Diffie-Hellman use to securely exchange cryptographic keys. Quantum key distribution (QKD) leverages principles of quantum mechanics, including quantum entanglement and the no-cloning theorem, to enable unconditionally secure key exchange resistant to computational attacks. Explore the transformative potential of QKD in enhancing cryptographic security beyond classical public key limitations.
Quantum Entanglement
Classical key exchange methods such as Diffie-Hellman rely on computational hardness assumptions, making them vulnerable to quantum attacks, whereas quantum key distribution (QKD) harnesses quantum entanglement to ensure unconditionally secure key exchange by detecting eavesdropping through quantum state disturbances. Quantum entanglement enables photons to share correlated states instantaneously, forming the basis of protocols like BB84 and E91 that guarantee security through the fundamental principles of quantum mechanics. Explore deeper insights into how entanglement revolutionizes quantum cryptography and secures communication against future quantum threats.
Eavesdropping Detection
Classical key exchange methods like Diffie-Hellman rely on computational hardness assumptions, making eavesdropping detection indirect and vulnerable to advances in computing power. Quantum key distribution (QKD) leverages quantum mechanics principles, enabling direct detection of eavesdropping by observing disturbances in quantum states, ensuring provable security. Explore the fundamental differences in eavesdropping detection mechanisms and their impact on secure communications.
Source and External Links
Key exchange - Wikipedia - Classical key exchange in cryptography involves symmetric-key methods where a secret key must be securely shared between two parties before communication, often requiring trusted channels, contrasted with asymmetric methods like Diffie-Hellman that allow secure key exchange over insecure channels without prior shared secrets.
What is a Key Exchange? - PrivacyEngine - Traditional classical key exchange techniques include Diffie-Hellman and RSA methods where parties share keys through mathematical problems like discrete logarithms or factorization, enabling secure communication over public channels.
Diffie-Hellman key exchange - Wikipedia - The Diffie-Hellman protocol, a foundational classical key exchange method, allows two parties without prior knowledge to establish a shared secret over an insecure channel by exchanging values derived from private secrets combined with a public base, making it computationally infeasible for an eavesdropper to derive the key.
 dowidth.com
dowidth.com