Post-quantum cryptography focuses on developing encryption algorithms resistant to attacks from quantum computers, ensuring future-proof data security. Multivariate polynomial cryptography relies on the complexity of solving systems of multivariate polynomial equations, offering a promising approach within post-quantum cryptographic schemes. Explore the differences and potentials of these cryptographic techniques to secure information in the quantum era.
Why it is important
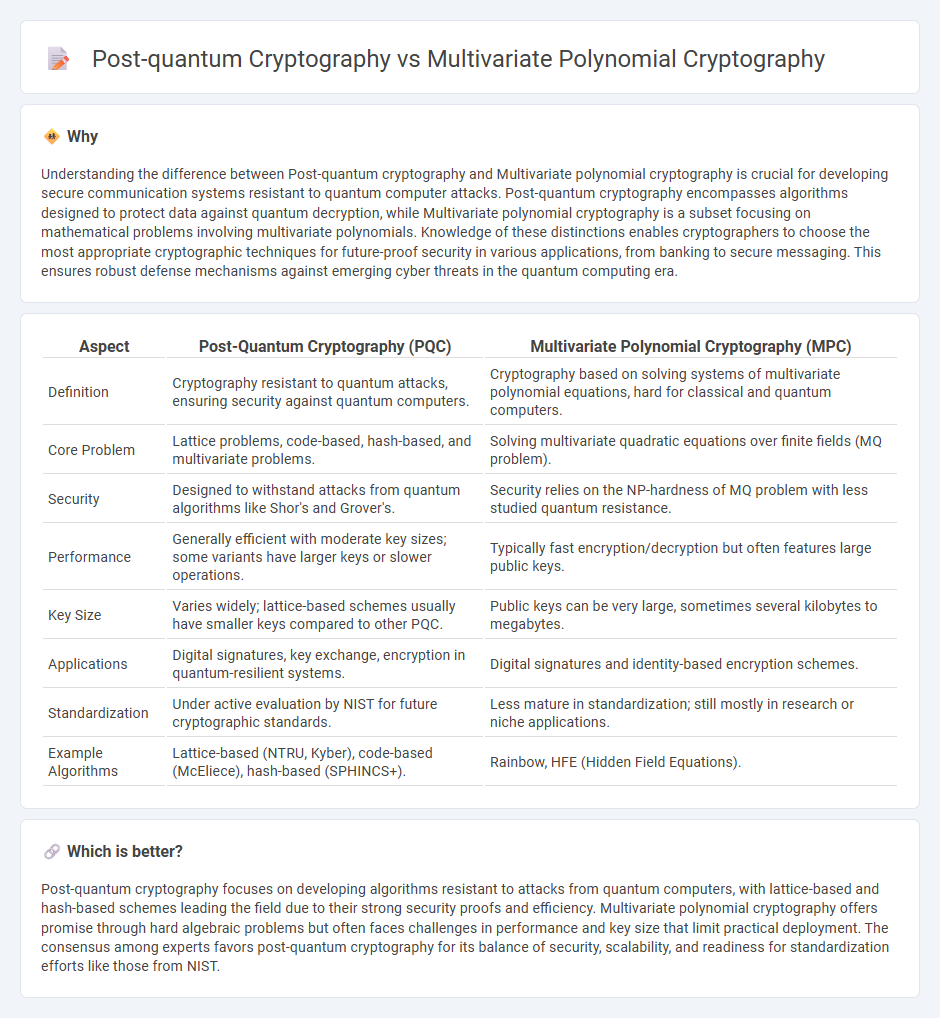
Understanding the difference between Post-quantum cryptography and Multivariate polynomial cryptography is crucial for developing secure communication systems resistant to quantum computer attacks. Post-quantum cryptography encompasses algorithms designed to protect data against quantum decryption, while Multivariate polynomial cryptography is a subset focusing on mathematical problems involving multivariate polynomials. Knowledge of these distinctions enables cryptographers to choose the most appropriate cryptographic techniques for future-proof security in various applications, from banking to secure messaging. This ensures robust defense mechanisms against emerging cyber threats in the quantum computing era.
Comparison Table
| Aspect | Post-Quantum Cryptography (PQC) | Multivariate Polynomial Cryptography (MPC) |
|---|---|---|
| Definition | Cryptography resistant to quantum attacks, ensuring security against quantum computers. | Cryptography based on solving systems of multivariate polynomial equations, hard for classical and quantum computers. |
| Core Problem | Lattice problems, code-based, hash-based, and multivariate problems. | Solving multivariate quadratic equations over finite fields (MQ problem). |
| Security | Designed to withstand attacks from quantum algorithms like Shor's and Grover's. | Security relies on the NP-hardness of MQ problem with less studied quantum resistance. |
| Performance | Generally efficient with moderate key sizes; some variants have larger keys or slower operations. | Typically fast encryption/decryption but often features large public keys. |
| Key Size | Varies widely; lattice-based schemes usually have smaller keys compared to other PQC. | Public keys can be very large, sometimes several kilobytes to megabytes. |
| Applications | Digital signatures, key exchange, encryption in quantum-resilient systems. | Digital signatures and identity-based encryption schemes. |
| Standardization | Under active evaluation by NIST for future cryptographic standards. | Less mature in standardization; still mostly in research or niche applications. |
| Example Algorithms | Lattice-based (NTRU, Kyber), code-based (McEliece), hash-based (SPHINCS+). | Rainbow, HFE (Hidden Field Equations). |
Which is better?
Post-quantum cryptography focuses on developing algorithms resistant to attacks from quantum computers, with lattice-based and hash-based schemes leading the field due to their strong security proofs and efficiency. Multivariate polynomial cryptography offers promise through hard algebraic problems but often faces challenges in performance and key size that limit practical deployment. The consensus among experts favors post-quantum cryptography for its balance of security, scalability, and readiness for standardization efforts like those from NIST.
Connection
Post-quantum cryptography focuses on developing cryptographic algorithms resistant to quantum computer attacks, with multivariate polynomial cryptography serving as a prime candidate due to its reliance on solving systems of multivariate quadratic equations, a problem believed to be NP-hard even for quantum computers. These multivariate schemes leverage the inherent computational complexity of polynomial equations over finite fields to create encryption, digital signatures, and key exchange protocols that withstand quantum decryption methods like Shor's algorithm. As part of post-quantum cryptography standards, multivariate polynomial cryptography provides a pathway to secure communications in a quantum-resilient digital landscape.
Key Terms
Multivariate Quadratic Equations
Multivariate polynomial cryptography, particularly schemes based on multivariate quadratic equations, offers a promising approach to post-quantum cryptography due to its resistance against quantum attacks and efficiency in key generation and signature verification. This cryptographic method relies on the computational hardness of solving systems of nonlinear polynomial equations over finite fields, which remains challenging for both classical and quantum computers. Explore the fundamental principles and recent advancements in multivariate quadratic cryptosystems to understand their potential role in securing future communication.
Lattice-based Cryptography
Lattice-based cryptography, a prominent branch of post-quantum cryptography, offers quantum-resistant security through complex mathematical problems rooted in lattice structures. In contrast, multivariate polynomial cryptography leverages the hardness of solving systems of nonlinear polynomial equations, with both approaches aiming to secure data against future quantum attacks. Explore deeper insights into how lattice-based schemes provide scalable and robust encryption methods in the evolving landscape of quantum-resistant cryptography.
Quantum Resistance
Multivariate polynomial cryptography relies on the hardness of solving systems of nonlinear polynomial equations over finite fields, offering strong resistance against quantum attacks due to its NP-hard problems. Post-quantum cryptography encompasses a variety of cryptosystems, including lattice-based, code-based, and multivariate schemes, all designed to withstand quantum algorithm capabilities like Shor's and Grover's. Discover more about how these cryptographic methods secure data in the quantum computing era.
Source and External Links
Exploring Multivariate Cryptography - This article introduces multivariate cryptography, highlighting its use of polynomial equations for security and its potential as a post-quantum cryptographic method.
Demystifying Multivariate Cryptography - This blog post provides an overview of multivariate cryptography, focusing on its role in post-quantum cryptography and including examples of digital signature schemes.
Multivariate Cryptography - This Wikipedia page offers a comprehensive overview of multivariate cryptography, detailing its construction and application in cryptographic primitives over finite fields.
 dowidth.com
dowidth.com