Post-quantum cryptography develops algorithms designed to secure data against attacks from quantum computers, which can potentially break traditional RSA encryption by factoring large integers efficiently. RSA encryption, widely used for secure communication, relies on the computational difficulty of prime factorization, a challenge quantum algorithms like Shor's algorithm threaten to overcome. Explore the advancements and implications of these cryptographic methods to understand the future of data security.
Why it is important
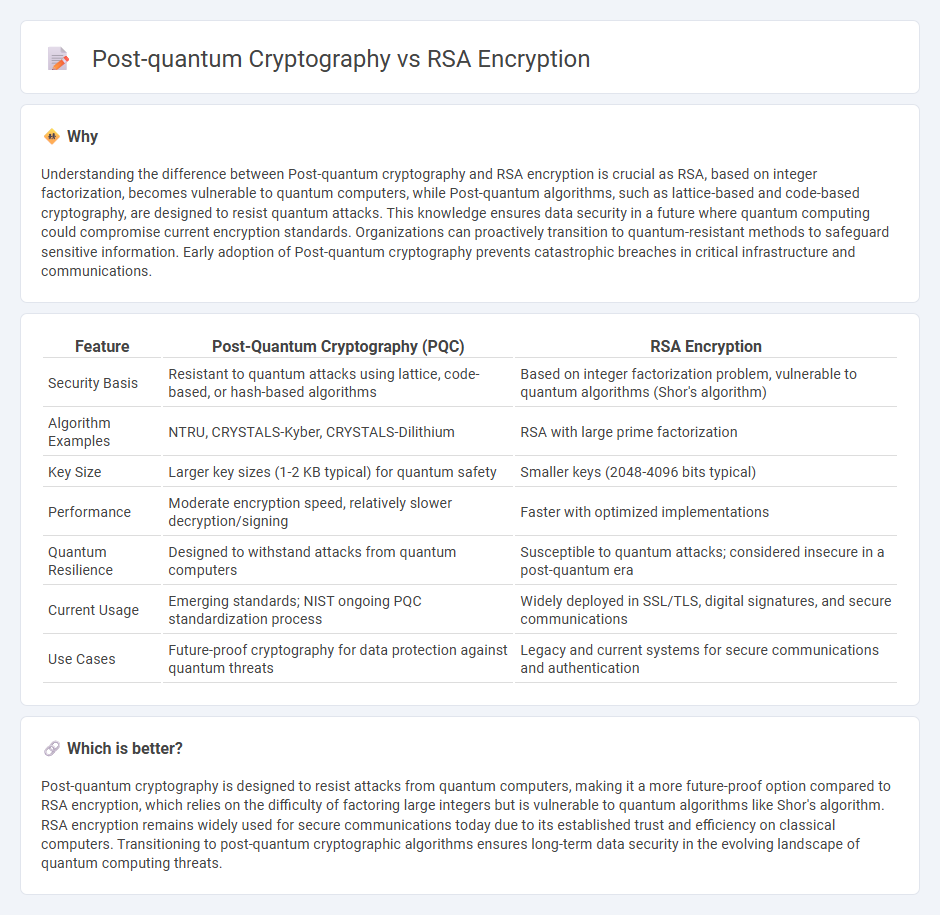
Understanding the difference between Post-quantum cryptography and RSA encryption is crucial as RSA, based on integer factorization, becomes vulnerable to quantum computers, while Post-quantum algorithms, such as lattice-based and code-based cryptography, are designed to resist quantum attacks. This knowledge ensures data security in a future where quantum computing could compromise current encryption standards. Organizations can proactively transition to quantum-resistant methods to safeguard sensitive information. Early adoption of Post-quantum cryptography prevents catastrophic breaches in critical infrastructure and communications.
Comparison Table
| Feature | Post-Quantum Cryptography (PQC) | RSA Encryption |
|---|---|---|
| Security Basis | Resistant to quantum attacks using lattice, code-based, or hash-based algorithms | Based on integer factorization problem, vulnerable to quantum algorithms (Shor's algorithm) |
| Algorithm Examples | NTRU, CRYSTALS-Kyber, CRYSTALS-Dilithium | RSA with large prime factorization |
| Key Size | Larger key sizes (1-2 KB typical) for quantum safety | Smaller keys (2048-4096 bits typical) |
| Performance | Moderate encryption speed, relatively slower decryption/signing | Faster with optimized implementations |
| Quantum Resilience | Designed to withstand attacks from quantum computers | Susceptible to quantum attacks; considered insecure in a post-quantum era |
| Current Usage | Emerging standards; NIST ongoing PQC standardization process | Widely deployed in SSL/TLS, digital signatures, and secure communications |
| Use Cases | Future-proof cryptography for data protection against quantum threats | Legacy and current systems for secure communications and authentication |
Which is better?
Post-quantum cryptography is designed to resist attacks from quantum computers, making it a more future-proof option compared to RSA encryption, which relies on the difficulty of factoring large integers but is vulnerable to quantum algorithms like Shor's algorithm. RSA encryption remains widely used for secure communications today due to its established trust and efficiency on classical computers. Transitioning to post-quantum cryptographic algorithms ensures long-term data security in the evolving landscape of quantum computing threats.
Connection
Post-quantum cryptography aims to develop encryption algorithms resistant to quantum computing attacks, posing a threat to classical RSA encryption. RSA encryption relies on the difficulty of factoring large prime numbers, a problem quantum computers can solve efficiently using Shor's algorithm. Transitioning to post-quantum cryptographic methods ensures data security against the future capabilities of quantum machines, maintaining confidentiality in digital communications.
Key Terms
Public-key cryptography
RSA encryption relies on the computational difficulty of factoring large prime numbers, making it vulnerable to quantum algorithms like Shor's, which can efficiently solve this problem. Post-quantum cryptography encompasses cryptographic algorithms designed to resist quantum attacks, including lattice-based, hash-based, and multivariate polynomial cryptography, ensuring the long-term security of public-key systems. Explore the latest advancements in post-quantum public-key cryptography to future-proof secure communications.
Quantum resistance
RSA encryption relies on the computational difficulty of factoring large prime numbers, making it vulnerable to quantum attacks via Shor's algorithm, which can efficiently break RSA in polynomial time. Post-quantum cryptography employs algorithms based on lattice problems, code-based cryptography, or multivariate polynomials that are believed to be resistant to quantum algorithms, ensuring stronger long-term security against quantum threats. Explore our detailed analysis on post-quantum cryptographic solutions and their implementation challenges to safeguard your data future-proof.
Shor's algorithm
RSA encryption relies on the difficulty of factoring large composite numbers, a task efficiently solvable by Shor's algorithm on a quantum computer, threatening its security. Post-quantum cryptography develops algorithms based on problems believed to be resistant to quantum attacks, such as lattice-based, hash-based, and code-based cryptosystems. Explore more about how post-quantum methods safeguard data against emerging quantum threats.
Source and External Links
RSA Algorithm in Cryptography - Provides an overview of the RSA algorithm, including its key generation, encryption, and decryption processes based on asymmetric cryptography.
What is the RSA algorithm? - Explains RSA as a public key cryptosystem using linked public and private keys for secure data transmission over the internet.
RSA cryptosystem - Describes the RSA algorithm's operation, including key generation, encryption, decryption, and its application in secure data transmission.
 dowidth.com
dowidth.com