Quantum-safe cryptography leverages advanced algorithms designed to withstand attacks from quantum computers, unlike classical cryptography that relies on mathematical problems vulnerable to quantum decryption. Classical cryptography methods, such as RSA and ECC, are at risk as quantum algorithms like Shor's algorithm can efficiently break them, necessitating the transition to quantum-resistant solutions. Explore the evolving landscape of cryptographic security to understand how quantum-safe cryptography ensures data protection in the quantum era.
Why it is important
Understanding the difference between quantum-safe cryptography and classical cryptography is crucial as quantum-safe methods are designed to protect data against future quantum computer attacks. Classical cryptography relies on mathematical problems that quantum computers can solve efficiently, potentially rendering current encryption obsolete. Quantum-safe cryptography uses algorithms resistant to quantum attacks, ensuring long-term data confidentiality. This knowledge enables organizations to future-proof their security infrastructure amidst evolving computational threats.
Comparison Table
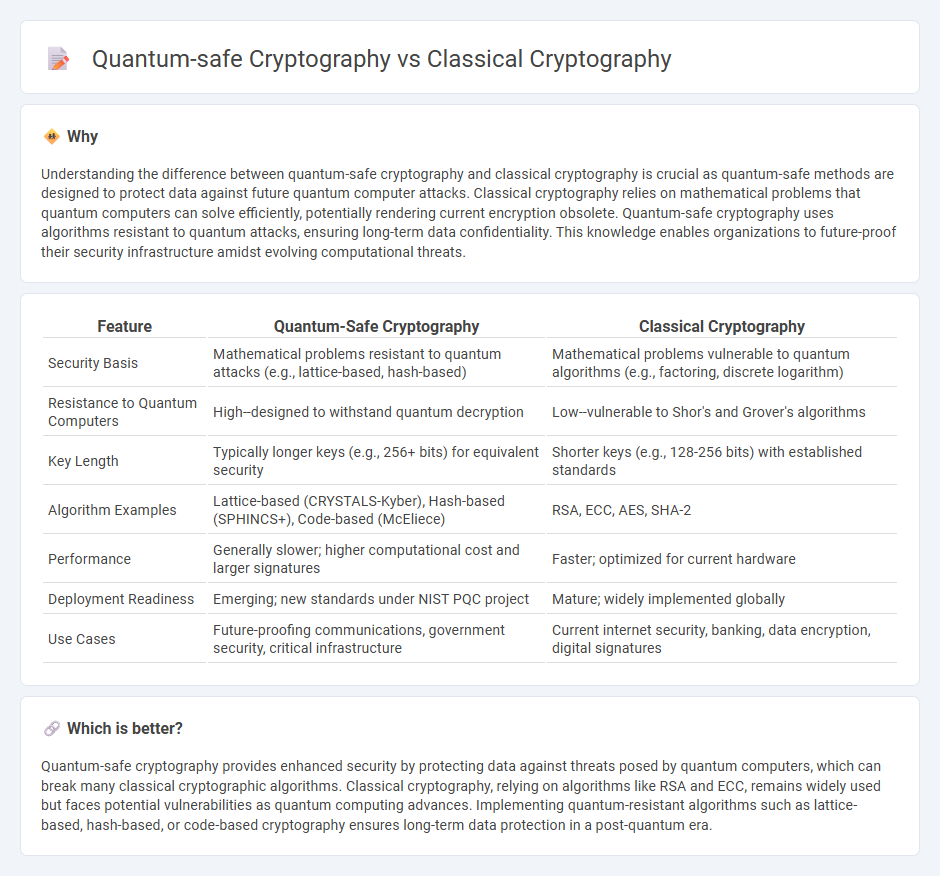
| Feature | Quantum-Safe Cryptography | Classical Cryptography |
|---|---|---|
| Security Basis | Mathematical problems resistant to quantum attacks (e.g., lattice-based, hash-based) | Mathematical problems vulnerable to quantum algorithms (e.g., factoring, discrete logarithm) |
| Resistance to Quantum Computers | High--designed to withstand quantum decryption | Low--vulnerable to Shor's and Grover's algorithms |
| Key Length | Typically longer keys (e.g., 256+ bits) for equivalent security | Shorter keys (e.g., 128-256 bits) with established standards |
| Algorithm Examples | Lattice-based (CRYSTALS-Kyber), Hash-based (SPHINCS+), Code-based (McEliece) | RSA, ECC, AES, SHA-2 |
| Performance | Generally slower; higher computational cost and larger signatures | Faster; optimized for current hardware |
| Deployment Readiness | Emerging; new standards under NIST PQC project | Mature; widely implemented globally |
| Use Cases | Future-proofing communications, government security, critical infrastructure | Current internet security, banking, data encryption, digital signatures |
Which is better?
Quantum-safe cryptography provides enhanced security by protecting data against threats posed by quantum computers, which can break many classical cryptographic algorithms. Classical cryptography, relying on algorithms like RSA and ECC, remains widely used but faces potential vulnerabilities as quantum computing advances. Implementing quantum-resistant algorithms such as lattice-based, hash-based, or code-based cryptography ensures long-term data protection in a post-quantum era.
Connection
Quantum-safe cryptography and classical cryptography share foundational principles of securing data through complex algorithms, yet quantum-safe methods are specifically designed to withstand attacks from quantum computers. Classical cryptography relies on mathematical problems like integer factorization and discrete logarithms, which quantum algorithms such as Shor's algorithm can efficiently solve, threatening current encryption standards. Quantum-safe cryptography employs alternative mathematical constructs like lattice-based, hash-based, or code-based cryptographic schemes that remain secure against both classical and quantum computational attacks.
Key Terms
Symmetric-key algorithms
Classical symmetric-key algorithms such as AES rely on computational hardness assumptions vulnerable to quantum attacks like Grover's algorithm, which effectively halves their key strength. Quantum-safe symmetric-key cryptography emphasizes increasing key lengths and using quantum-resistant primitives to maintain security against quantum adversaries. Explore the latest standards and research developments in quantum-safe symmetric-key algorithms to ensure robust encryption in the quantum era.
Public-key algorithms
Classical cryptography relies on public-key algorithms such as RSA and ECC, which are vulnerable to Shor's algorithm on quantum computers, risking data security as quantum technology advances. Quantum-safe cryptography employs post-quantum algorithms like lattice-based, hash-based, and multivariate polynomial cryptography to ensure secure key exchange and digital signatures against quantum attacks. Discover the latest developments and comparative analysis of public-key algorithms in the transition from classical to quantum-safe cryptographic standards.
Post-quantum cryptography
Classical cryptography relies on mathematical problems such as prime factorization and discrete logarithms, which are vulnerable to attacks by quantum algorithms like Shor's algorithm. Post-quantum cryptography develops cryptographic systems based on problems believed to be resistant to quantum attacks, including lattice-based, hash-based, and code-based cryptography. Explore the advancements and challenges in securing data against future quantum threats.
Source and External Links
How Do Classical Cryptography and Modern Cryptography Differ? - Classical cryptography involves manual, pre-computer era methods like substitution ciphers--such as the Caesar and Vigenere ciphers--where security relied on keeping the algorithm secret, making these systems vulnerable to frequency analysis and difficult to scale for large data.
Classical Cryptography and Quantum Cryptography - GeeksforGeeks - Classical cryptography uses mathematical techniques and keys to transform plaintext into ciphertext, with symmetric (single key) and asymmetric (public/private key) systems, but faces key distribution challenges and is breakable without a one-time pad.
Classical cipher - Wikipedia - Classical ciphers are historical encryption methods, such as those from Greek, Roman, and Renaissance periods, which are simple to use by hand but generally easy to break with modern computational power, unlike today's complex computer-based algorithms.
 dowidth.com
dowidth.com