Zero Trust Architecture requires strict verification of every user and device attempting to access resources, minimizing security risks by eliminating implicit trust within networks. In contrast, the implicit trust model assumes users and devices inside the network are secure, often leading to increased vulnerability to internal threats and breaches. Explore how transitioning to Zero Trust can enhance your organization's cybersecurity framework and reduce risk exposure.
Why it is important
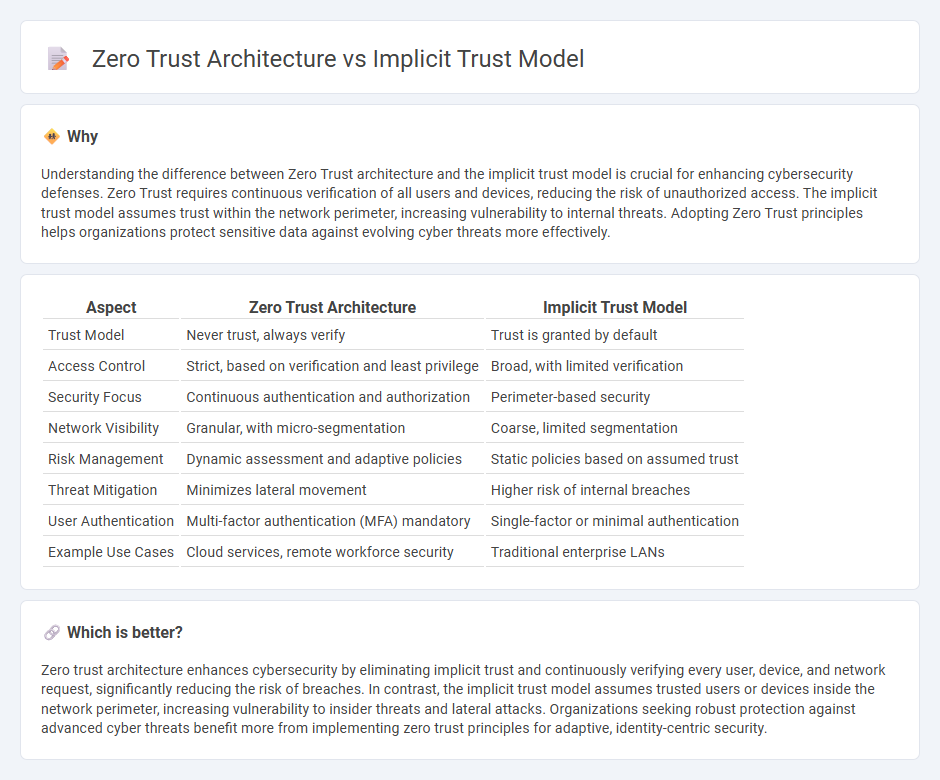
Understanding the difference between Zero Trust architecture and the implicit trust model is crucial for enhancing cybersecurity defenses. Zero Trust requires continuous verification of all users and devices, reducing the risk of unauthorized access. The implicit trust model assumes trust within the network perimeter, increasing vulnerability to internal threats. Adopting Zero Trust principles helps organizations protect sensitive data against evolving cyber threats more effectively.
Comparison Table
| Aspect | Zero Trust Architecture | Implicit Trust Model |
|---|---|---|
| Trust Model | Never trust, always verify | Trust is granted by default |
| Access Control | Strict, based on verification and least privilege | Broad, with limited verification |
| Security Focus | Continuous authentication and authorization | Perimeter-based security |
| Network Visibility | Granular, with micro-segmentation | Coarse, limited segmentation |
| Risk Management | Dynamic assessment and adaptive policies | Static policies based on assumed trust |
| Threat Mitigation | Minimizes lateral movement | Higher risk of internal breaches |
| User Authentication | Multi-factor authentication (MFA) mandatory | Single-factor or minimal authentication |
| Example Use Cases | Cloud services, remote workforce security | Traditional enterprise LANs |
Which is better?
Zero trust architecture enhances cybersecurity by eliminating implicit trust and continuously verifying every user, device, and network request, significantly reducing the risk of breaches. In contrast, the implicit trust model assumes trusted users or devices inside the network perimeter, increasing vulnerability to insider threats and lateral attacks. Organizations seeking robust protection against advanced cyber threats benefit more from implementing zero trust principles for adaptive, identity-centric security.
Connection
Zero Trust Architecture eliminates implicit trust by continuously verifying every access request based on strict identity verification and device health checks. It replaces traditional implicit trust models that assume internal network users are trustworthy by enforcing least-privilege access and micro-segmentation. This connection strengthens cybersecurity by minimizing attack surfaces and preventing lateral movement within networks.
Key Terms
Trust Boundaries
Implicit trust models rely on predefined trust boundaries where internal networks are considered trustworthy, often exposing systems to risks when boundaries are breached. Zero Trust Architecture eliminates implicit trust by continuously verifying all users and devices regardless of their location, enforcing strict access controls and segmentation to minimize exposure. Explore the detailed differences and benefits of both models to enhance your cybersecurity strategy.
Verification
Implicit trust models assume user and device trustworthiness based on location or network presence, leading to limited identity verification and increased security risks. Zero Trust Architecture enforces strict identity verification and continuous authentication regardless of location, minimizing potential breaches by verifying every access request. Discover how robust verification protocols in Zero Trust can transform your cybersecurity strategy.
Least Privilege
The implicit trust model assumes users and devices inside the network are trustworthy, often leading to broad access privileges that can increase security vulnerabilities. Zero Trust Architecture enforces the principle of Least Privilege by continuously verifying identities and limiting access to the minimum necessary resources, reducing the attack surface. Explore how implementing Zero Trust enhances security and minimizes risk through strict access controls.
Source and External Links
The Identity-Driven Reality of Zero Trust - Implicit trust means that actions are allowed between systems, users, and resources simply because of their relationship, rather than explicit verification, which can amplify risk if any link in the chain is compromised.
Zero Trust Architecture - NIST Technical Series Publications - In an implicit trust model, after passing a single point of authentication (like a gateway), all entities and their requests within the internal zone are trusted equally without further checks, potentially exposing resources to risk.
Implicit Trust vs Explicit Trust in Access Management - Implicit trust automatically approves every device and action by default, relying on preset permissions and not considering location or real-time authorization, making it suitable only for low-risk resources.
 dowidth.com
dowidth.com