Zero Trust is a security framework that requires continuous verification of user identities and device trust levels before granting access, minimizing the risk of breaches. Multi-Factor Authentication (MFA) enhances login security by requiring users to provide two or more verification factors, reducing unauthorized access through compromised credentials. Explore the key differences and benefits of Zero Trust and MFA to strengthen your cybersecurity strategy.
Why it is important
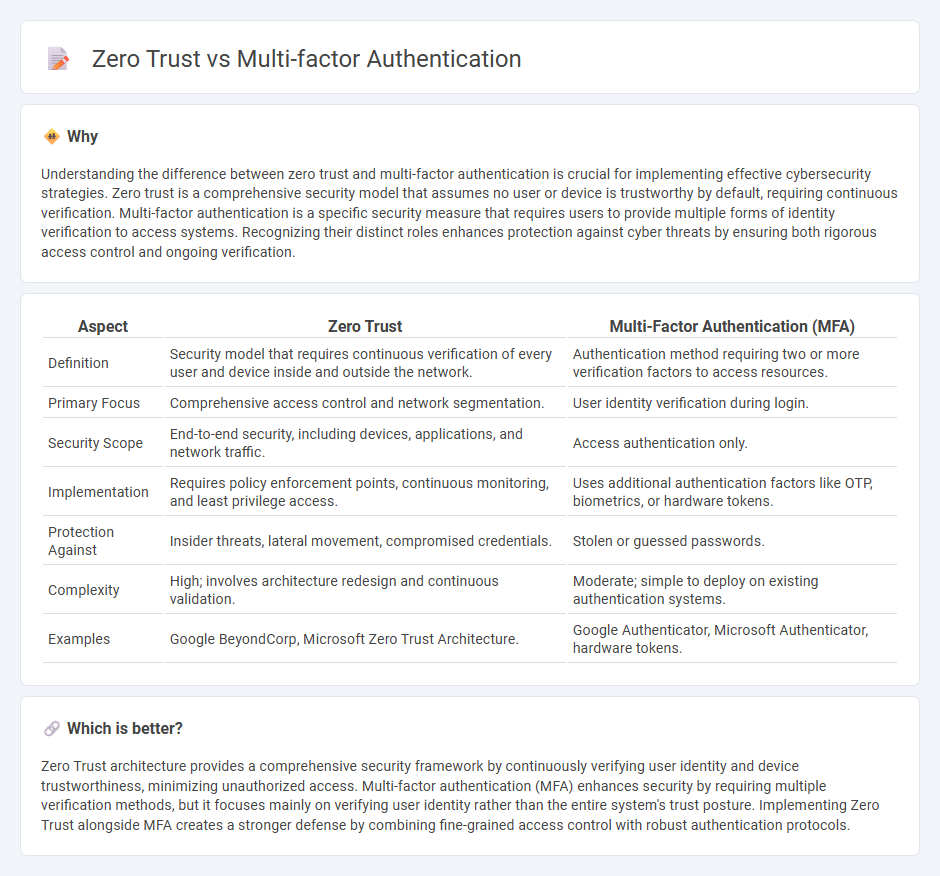
Understanding the difference between zero trust and multi-factor authentication is crucial for implementing effective cybersecurity strategies. Zero trust is a comprehensive security model that assumes no user or device is trustworthy by default, requiring continuous verification. Multi-factor authentication is a specific security measure that requires users to provide multiple forms of identity verification to access systems. Recognizing their distinct roles enhances protection against cyber threats by ensuring both rigorous access control and ongoing verification.
Comparison Table
| Aspect | Zero Trust | Multi-Factor Authentication (MFA) |
|---|---|---|
| Definition | Security model that requires continuous verification of every user and device inside and outside the network. | Authentication method requiring two or more verification factors to access resources. |
| Primary Focus | Comprehensive access control and network segmentation. | User identity verification during login. |
| Security Scope | End-to-end security, including devices, applications, and network traffic. | Access authentication only. |
| Implementation | Requires policy enforcement points, continuous monitoring, and least privilege access. | Uses additional authentication factors like OTP, biometrics, or hardware tokens. |
| Protection Against | Insider threats, lateral movement, compromised credentials. | Stolen or guessed passwords. |
| Complexity | High; involves architecture redesign and continuous validation. | Moderate; simple to deploy on existing authentication systems. |
| Examples | Google BeyondCorp, Microsoft Zero Trust Architecture. | Google Authenticator, Microsoft Authenticator, hardware tokens. |
Which is better?
Zero Trust architecture provides a comprehensive security framework by continuously verifying user identity and device trustworthiness, minimizing unauthorized access. Multi-factor authentication (MFA) enhances security by requiring multiple verification methods, but it focuses mainly on verifying user identity rather than the entire system's trust posture. Implementing Zero Trust alongside MFA creates a stronger defense by combining fine-grained access control with robust authentication protocols.
Connection
Zero Trust architecture fundamentally relies on Multi-Factor Authentication (MFA) to verify users' identities beyond mere passwords, enhancing security by requiring multiple proof factors. MFA is a critical component in enforcing Zero Trust principles, as it minimizes the risk of unauthorized access even if credentials are compromised. Together, they strengthen cyber defense by ensuring continuous verification and limiting access based on strict identity validation.
Key Terms
Authentication
Multi-factor authentication (MFA) enhances security by requiring two or more verification methods, such as passwords, biometrics, or one-time codes, to confirm user identity during login. Zero Trust architecture goes beyond MFA by continuously verifying every access request based on user, device, location, and behavior, enforcing strict access controls regardless of network location. Explore further to understand how integrating MFA within Zero Trust frameworks fortifies authentication strategies for modern cybersecurity.
Authorization
Multi-factor authentication (MFA) enhances authorization by requiring multiple verification methods, such as passwords and biometric data, to ensure user identity before granting access. Zero Trust architecture goes beyond MFA by implementing continuous authorization checks, ensuring that no user or device is implicitly trusted regardless of location, relying on real-time policies and risk assessment. Explore deeper into how these approaches reshape secure access control in modern cybersecurity frameworks.
Trust Verification
Multi-factor authentication (MFA) enhances security by requiring users to provide multiple credentials, such as passwords and biometric verification, ensuring stronger identity confirmation. Zero Trust architecture shifts the focus to continuous trust verification, treating every access request as potentially hostile until verified through strict authentication, authorization, and real-time monitoring. Explore deeper insights into how Trust Verification transforms cybersecurity frameworks by visiting our detailed resource.
Source and External Links
What is MFA (Multifactor Authentication)? - IBM - Multifactor authentication verifies a user's identity by requiring at least two distinct proofs such as a password and a fingerprint, providing extra layers of security beyond passwords alone and is widely used for protecting sensitive accounts and systems.
What is Multi-Factor Authentication (MFA)? - OneLogin - MFA enhances security by requiring users to present two or more verification factors like passwords and biometrics or hardware keys, reducing the risk of cyberattacks on online accounts and resources.
Microsoft Entra multifactor authentication overview - MFA requires two or more authentication methods -- something you know (password), something you have (device), or something you are (biometrics) -- to strengthen protection during sign-in, preventing unauthorized access even if passwords are compromised.
 dowidth.com
dowidth.com