Quantum-safe cryptography leverages advanced algorithms designed to withstand attacks from quantum computers, ensuring secure data encryption in a post-quantum world. Digital signatures, traditionally based on RSA or ECC, face potential vulnerabilities as quantum computing evolves, prompting a shift towards quantum-resistant techniques. Explore the latest advancements in quantum-safe cryptography and digital signature solutions to safeguard digital communications.
Why it is important
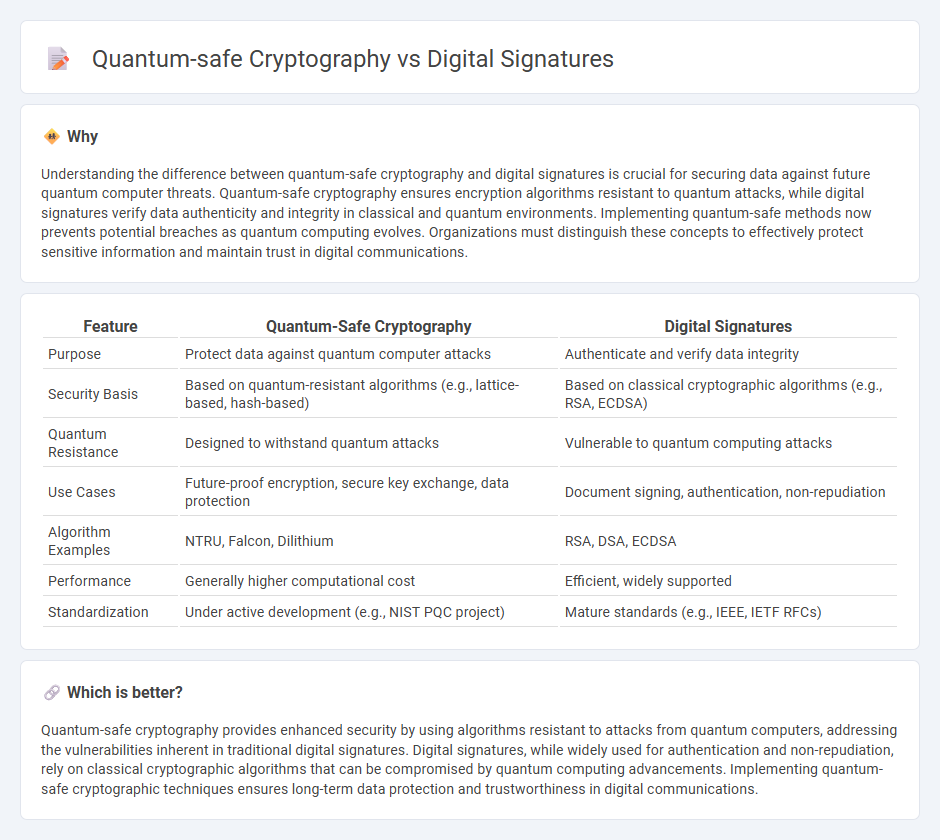
Understanding the difference between quantum-safe cryptography and digital signatures is crucial for securing data against future quantum computer threats. Quantum-safe cryptography ensures encryption algorithms resistant to quantum attacks, while digital signatures verify data authenticity and integrity in classical and quantum environments. Implementing quantum-safe methods now prevents potential breaches as quantum computing evolves. Organizations must distinguish these concepts to effectively protect sensitive information and maintain trust in digital communications.
Comparison Table
| Feature | Quantum-Safe Cryptography | Digital Signatures |
|---|---|---|
| Purpose | Protect data against quantum computer attacks | Authenticate and verify data integrity |
| Security Basis | Based on quantum-resistant algorithms (e.g., lattice-based, hash-based) | Based on classical cryptographic algorithms (e.g., RSA, ECDSA) |
| Quantum Resistance | Designed to withstand quantum attacks | Vulnerable to quantum computing attacks |
| Use Cases | Future-proof encryption, secure key exchange, data protection | Document signing, authentication, non-repudiation |
| Algorithm Examples | NTRU, Falcon, Dilithium | RSA, DSA, ECDSA |
| Performance | Generally higher computational cost | Efficient, widely supported |
| Standardization | Under active development (e.g., NIST PQC project) | Mature standards (e.g., IEEE, IETF RFCs) |
Which is better?
Quantum-safe cryptography provides enhanced security by using algorithms resistant to attacks from quantum computers, addressing the vulnerabilities inherent in traditional digital signatures. Digital signatures, while widely used for authentication and non-repudiation, rely on classical cryptographic algorithms that can be compromised by quantum computing advancements. Implementing quantum-safe cryptographic techniques ensures long-term data protection and trustworthiness in digital communications.
Connection
Quantum-safe cryptography ensures data security against quantum computer attacks by using algorithms resistant to quantum decryption, which is crucial for maintaining the integrity of digital signatures. Digital signatures rely on cryptographic methods to authenticate the origin and integrity of a message, making the adoption of quantum-resistant algorithms essential to prevent forgery in a post-quantum era. Integrating quantum-safe cryptography with digital signature schemes safeguards sensitive transactions and communications from future quantum threats.
Key Terms
Public Key Infrastructure (PKI)
Digital signatures rely on traditional cryptographic algorithms like RSA and ECDSA within Public Key Infrastructure (PKI) to authenticate digital documents and transactions. Quantum-safe cryptography, including lattice-based and hash-based algorithms, aims to secure PKI against the threat posed by quantum computers that can break current cryptographic standards. Explore the evolving landscape of quantum-resistant PKI solutions to future-proof digital security.
Shor’s Algorithm
Shor's Algorithm poses a significant threat to traditional digital signatures by enabling quantum computers to efficiently factor large integers and compute discrete logarithms, which underpin RSA and ECC schemes. Quantum-safe cryptography, including lattice-based, hash-based, and multivariate polynomial cryptography, is designed to resist these quantum attacks and ensure long-term data integrity and authentication. Explore the advances in post-quantum cryptographic methods to secure your digital communications against future quantum threats.
Lattice-based Cryptography
Lattice-based cryptography offers a quantum-safe alternative to traditional digital signatures by leveraging complex mathematical structures that resist quantum attacks, unlike RSA or ECC schemes vulnerable to Shor's algorithm. Its foundation on problems like Learning With Errors (LWE) ensures robust security against future quantum computers while enabling efficient and scalable digital signature schemes. Explore the advancements in lattice-based cryptography to understand how it is shaping the future of secure digital authentication.
Source and External Links
What is a Digital Signature? | DigiCert FAQ - This webpage provides an overview of digital signatures, including their use in validating signer identity and document integrity through public key infrastructure (PKI) technology.
What is a Digital Signature? | Definition from TechTarget - This article explains digital signatures as a mathematical technique for validating the authenticity and integrity of digital documents, messages, or software using public key cryptography.
Understanding digital signatures - This webpage explains how digital signatures work through Public Key Infrastructure (PKI), requiring a digital certificate for identity assurance, and how they securely authenticate electronic documents.
 dowidth.com
dowidth.com