Quantum-safe cryptography ensures secure communication against threats from quantum computers by employing algorithms resistant to quantum attacks, while code-based cryptography relies on the hardness of decoding random linear codes, offering strong security backed by decades of research. NIST's post-quantum cryptography standardization heavily features code-based schemes like McEliece for its efficiency and proven reliability. Explore more about how these cutting-edge approaches safeguard future digital security.
Why it is important
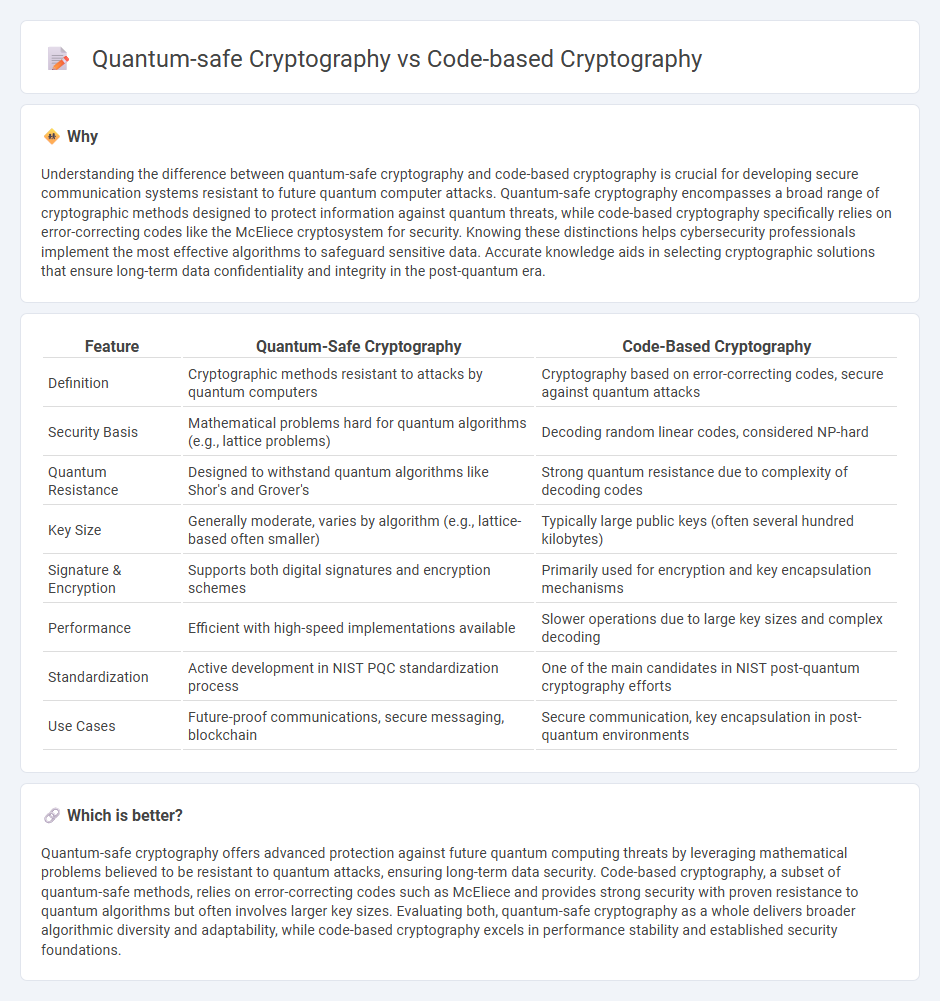
Understanding the difference between quantum-safe cryptography and code-based cryptography is crucial for developing secure communication systems resistant to future quantum computer attacks. Quantum-safe cryptography encompasses a broad range of cryptographic methods designed to protect information against quantum threats, while code-based cryptography specifically relies on error-correcting codes like the McEliece cryptosystem for security. Knowing these distinctions helps cybersecurity professionals implement the most effective algorithms to safeguard sensitive data. Accurate knowledge aids in selecting cryptographic solutions that ensure long-term data confidentiality and integrity in the post-quantum era.
Comparison Table
| Feature | Quantum-Safe Cryptography | Code-Based Cryptography |
|---|---|---|
| Definition | Cryptographic methods resistant to attacks by quantum computers | Cryptography based on error-correcting codes, secure against quantum attacks |
| Security Basis | Mathematical problems hard for quantum algorithms (e.g., lattice problems) | Decoding random linear codes, considered NP-hard |
| Quantum Resistance | Designed to withstand quantum algorithms like Shor's and Grover's | Strong quantum resistance due to complexity of decoding codes |
| Key Size | Generally moderate, varies by algorithm (e.g., lattice-based often smaller) | Typically large public keys (often several hundred kilobytes) |
| Signature & Encryption | Supports both digital signatures and encryption schemes | Primarily used for encryption and key encapsulation mechanisms |
| Performance | Efficient with high-speed implementations available | Slower operations due to large key sizes and complex decoding |
| Standardization | Active development in NIST PQC standardization process | One of the main candidates in NIST post-quantum cryptography efforts |
| Use Cases | Future-proof communications, secure messaging, blockchain | Secure communication, key encapsulation in post-quantum environments |
Which is better?
Quantum-safe cryptography offers advanced protection against future quantum computing threats by leveraging mathematical problems believed to be resistant to quantum attacks, ensuring long-term data security. Code-based cryptography, a subset of quantum-safe methods, relies on error-correcting codes such as McEliece and provides strong security with proven resistance to quantum algorithms but often involves larger key sizes. Evaluating both, quantum-safe cryptography as a whole delivers broader algorithmic diversity and adaptability, while code-based cryptography excels in performance stability and established security foundations.
Connection
Quantum-safe cryptography and code-based cryptography are interconnected through their shared goal of securing data against quantum computing threats. Code-based cryptography, relying on hard problems in coding theory such as the syndrome decoding problem, forms a crucial category within quantum-safe algorithms designed to resist attacks from quantum computers. These approaches ensure robust encryption by leveraging mathematically complex structures that remain secure even as quantum computational power advances.
Key Terms
McEliece Cryptosystem
The McEliece Cryptosystem, a prominent code-based cryptographic scheme, offers strong resistance to quantum attacks by leveraging the complexity of decoding random linear codes, contrasting with traditional cryptography vulnerable to Shor's algorithm. Quantum-safe cryptography encompasses various approaches such as lattice-based, multivariate, and code-based systems, with McEliece standing out due to its long-standing security proofs and fast encryption/decryption processes. Explore deeper insights into the McEliece Cryptosystem and its pivotal role in the post-quantum cryptography landscape.
Post-Quantum Cryptography
Post-Quantum Cryptography (PQC) emphasizes developing algorithms resistant to quantum attacks, securing data beyond the capabilities of classical code-based cryptography. Code-based cryptography, such as McEliece and Niederreiter schemes, relies on the hardness of decoding random linear codes but faces challenges in key size and efficiency. Explore the latest advancements in PQC to understand how these cryptographic frameworks safeguard future communications against quantum threats.
Lattice-based Cryptography
Lattice-based cryptography leverages complex mathematical structures called lattices, offering strong resistance against attacks from both classical and quantum computers, making it a leading candidate for quantum-safe cryptographic standards. Unlike traditional code-based cryptography, which relies on error-correcting codes, lattice-based approaches enable efficient key generation, encryption, and digital signatures with proven hardness assumptions linked to lattice problems like the Shortest Vector Problem (SVP). Explore the fundamentals and advances in lattice-based cryptography to understand its pivotal role in securing future digital communications against quantum threats.
Source and External Links
What is Code-based Cryptography? - Utimaco - Code-based cryptography consists of both symmetric and asymmetric cryptosystems whose security relies on the hardness of decoding specific linear error-correcting codes, such as Goppa codes, with the classic example being the McEliece cryptosystem, where the public key is a scrambled version of a private code matrix.
CBCrypto - Code-based cryptography studies cryptographic systems whose security is based on difficult problems in coding theory, is considered promising for post-quantum security, and remains a candidate in ongoing NIST standardization processes for future cryptographic standards.
A Survey on Code-based Cryptography - arXiv - This survey covers the mathematical foundations, main proposals in standardization, and security challenges of code-based cryptography, highlighting its role in public-key encryption, key encapsulation, and digital signatures, especially in the context of NIST's reopened call for post-quantum signature schemes.
 dowidth.com
dowidth.com