Quantum supremacy represents a breakthrough where quantum computers surpass classical counterparts in solving complex problems, posing significant challenges to current cryptographic protocols dependent on classical algorithms. As quantum algorithms like Shor's algorithm threaten to break widely used encryption methods such as RSA and ECC, the cybersecurity landscape must adapt by developing quantum-resistant cryptography and post-quantum encryption standards. Explore the evolving intersection of quantum computing and cryptography to understand the future of secure communication.
Why it is important
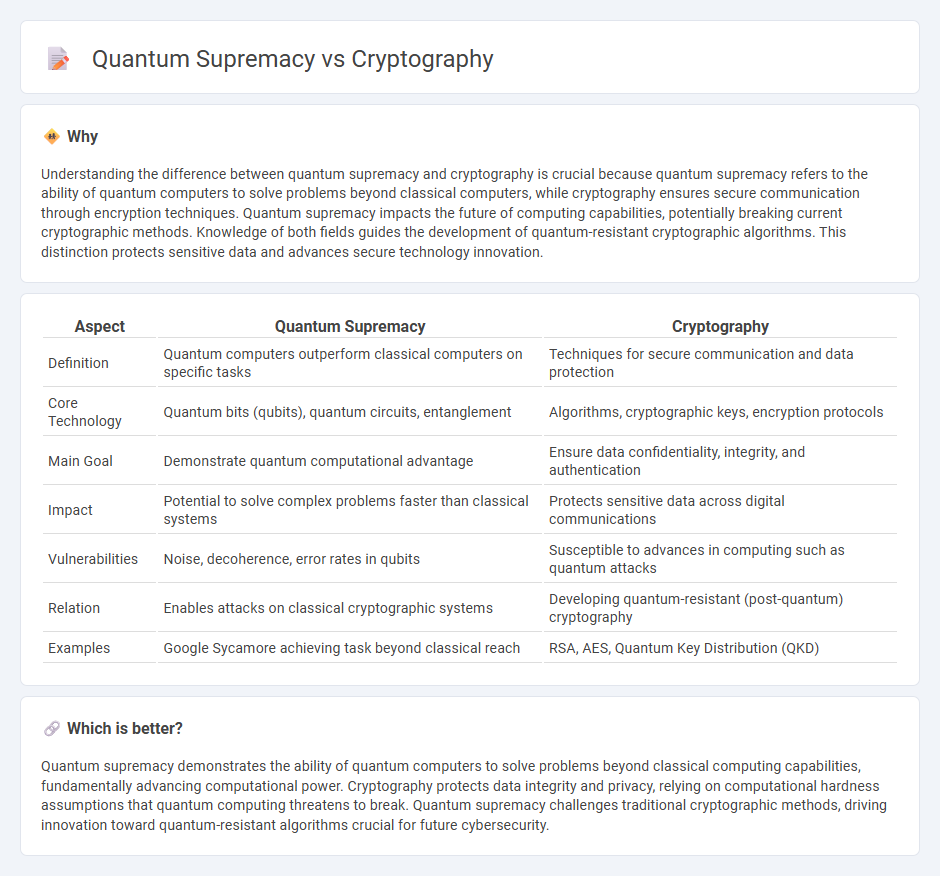
Understanding the difference between quantum supremacy and cryptography is crucial because quantum supremacy refers to the ability of quantum computers to solve problems beyond classical computers, while cryptography ensures secure communication through encryption techniques. Quantum supremacy impacts the future of computing capabilities, potentially breaking current cryptographic methods. Knowledge of both fields guides the development of quantum-resistant cryptographic algorithms. This distinction protects sensitive data and advances secure technology innovation.
Comparison Table
| Aspect | Quantum Supremacy | Cryptography |
|---|---|---|
| Definition | Quantum computers outperform classical computers on specific tasks | Techniques for secure communication and data protection |
| Core Technology | Quantum bits (qubits), quantum circuits, entanglement | Algorithms, cryptographic keys, encryption protocols |
| Main Goal | Demonstrate quantum computational advantage | Ensure data confidentiality, integrity, and authentication |
| Impact | Potential to solve complex problems faster than classical systems | Protects sensitive data across digital communications |
| Vulnerabilities | Noise, decoherence, error rates in qubits | Susceptible to advances in computing such as quantum attacks |
| Relation | Enables attacks on classical cryptographic systems | Developing quantum-resistant (post-quantum) cryptography |
| Examples | Google Sycamore achieving task beyond classical reach | RSA, AES, Quantum Key Distribution (QKD) |
Which is better?
Quantum supremacy demonstrates the ability of quantum computers to solve problems beyond classical computing capabilities, fundamentally advancing computational power. Cryptography protects data integrity and privacy, relying on computational hardness assumptions that quantum computing threatens to break. Quantum supremacy challenges traditional cryptographic methods, driving innovation toward quantum-resistant algorithms crucial for future cybersecurity.
Connection
Quantum supremacy, the point where quantum computers outperform classical ones, directly challenges current cryptographic systems reliant on complex mathematical problems. Quantum algorithms such as Shor's algorithm can efficiently factor large integers, threatening widely-used encryption methods like RSA and ECC. This connection drives the development of quantum-resistant cryptography to secure data against future quantum attacks.
Key Terms
Encryption
Quantum supremacy threatens traditional cryptographic encryption by enabling quantum computers to solve complex mathematical problems exponentially faster than classical systems. Shor's algorithm, for example, can efficiently factor large prime numbers, undermining RSA and ECC encryption methods widely used for secure data transmission. Explore how advancements in post-quantum cryptography are developing resilient encryption standards to safeguard data in a quantum-powered future.
Shor's Algorithm
Shor's Algorithm, a quantum algorithm capable of integer factorization, poses a significant threat to classical cryptographic systems like RSA by potentially breaking their security in polynomial time rather than exponential. Quantum supremacy refers to a quantum computer's ability to solve problems beyond the reach of classical computers, with Shor's Algorithm exemplifying a practical application that endangers current encryption methods. Explore how advancements in quantum computing and Shor's Algorithm are reshaping the future landscape of cybersecurity.
Quantum-resistant algorithms
Quantum-resistant algorithms are designed to secure data against the computational power of quantum computers, which threaten traditional cryptographic methods like RSA and ECC. These algorithms, including lattice-based, hash-based, and code-based cryptography, provide robust defenses against quantum attacks by leveraging mathematical problems believed to be hard for quantum machines to solve. Explore the latest advancements in quantum-resistant algorithms to ensure future-proof cybersecurity.
Source and External Links
Cryptography - Cryptography is the practice and study of techniques for secure communication that prevent unauthorized third parties from reading private messages, involving methods like encryption and decryption to protect information confidentiality and integrity across fields including mathematics, computer science, and engineering.
Cryptography and its Types - Cryptography secures information through codes to ensure confidentiality, integrity, authentication, and non-repudiation, by converting plain text into ciphertext via cryptographic keys and algorithms.
What is Cryptography? - Cryptography protects information at rest, in transit, or in use using coded algorithms and signatures, aiming to maintain confidentiality, integrity, authentication, and non-repudiation, forming the basis for secure internet communications and digital currencies.
 dowidth.com
dowidth.com