Silent cyber coverage addresses cyber risks that are not explicitly included or excluded in traditional insurance policies, filling gaps in protection for businesses vulnerable to cyber attacks. Cyber risk pooling involves multiple insurers sharing the financial risks associated with cyber threats, enhancing risk management through collective resources. Discover more about how these approaches can safeguard your organization against evolving cyber threats.
Why it is important
Understanding the difference between silent cyber coverage and cyber risk pooling is crucial for accurate risk management in the insurance industry. Silent cyber coverage refers to unintentional cyber risk exposure in traditional policies without explicit cyber endorsements, while cyber risk pooling involves shared risk among insurers for cyber-related losses. Knowing these distinctions helps insurers design policies that clearly define coverage scope and avoid unexpected liabilities. This clarity ensures businesses receive appropriate protection against cyber threats, reducing financial uncertainty in cyber risk events.
Comparison Table
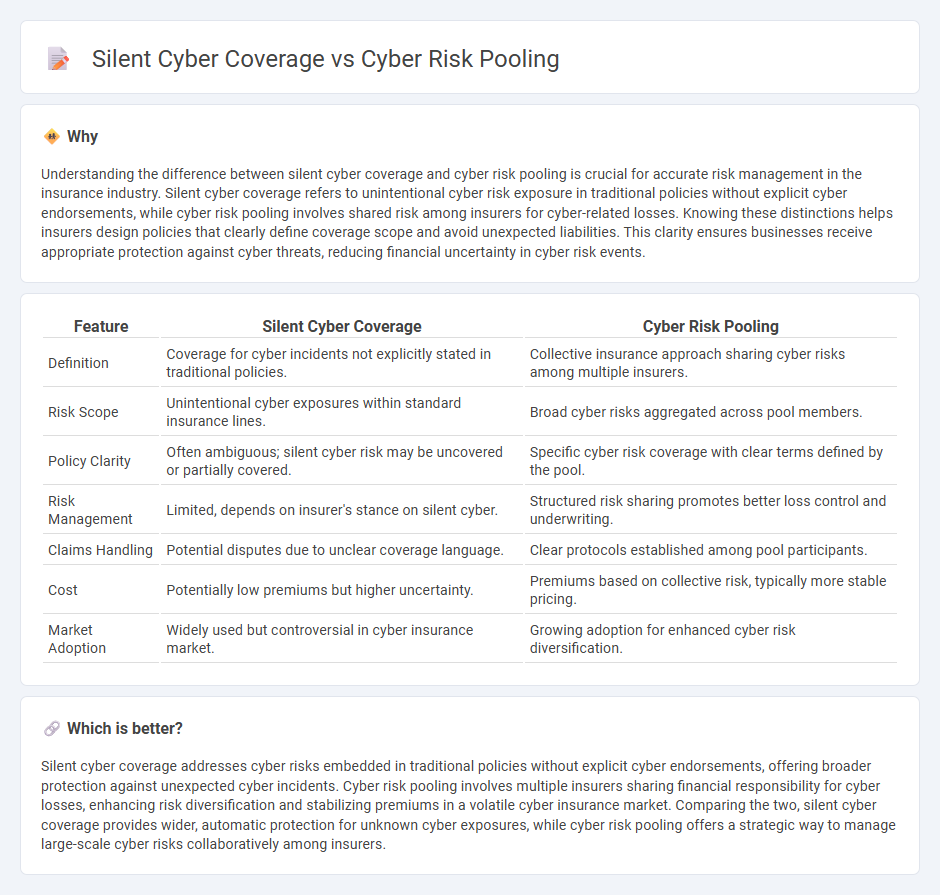
| Feature | Silent Cyber Coverage | Cyber Risk Pooling |
|---|---|---|
| Definition | Coverage for cyber incidents not explicitly stated in traditional policies. | Collective insurance approach sharing cyber risks among multiple insurers. |
| Risk Scope | Unintentional cyber exposures within standard insurance lines. | Broad cyber risks aggregated across pool members. |
| Policy Clarity | Often ambiguous; silent cyber risk may be uncovered or partially covered. | Specific cyber risk coverage with clear terms defined by the pool. |
| Risk Management | Limited, depends on insurer's stance on silent cyber. | Structured risk sharing promotes better loss control and underwriting. |
| Claims Handling | Potential disputes due to unclear coverage language. | Clear protocols established among pool participants. |
| Cost | Potentially low premiums but higher uncertainty. | Premiums based on collective risk, typically more stable pricing. |
| Market Adoption | Widely used but controversial in cyber insurance market. | Growing adoption for enhanced cyber risk diversification. |
Which is better?
Silent cyber coverage addresses cyber risks embedded in traditional policies without explicit cyber endorsements, offering broader protection against unexpected cyber incidents. Cyber risk pooling involves multiple insurers sharing financial responsibility for cyber losses, enhancing risk diversification and stabilizing premiums in a volatile cyber insurance market. Comparing the two, silent cyber coverage provides wider, automatic protection for unknown cyber exposures, while cyber risk pooling offers a strategic way to manage large-scale cyber risks collaboratively among insurers.
Connection
Silent cyber coverage addresses the gaps in traditional insurance policies by covering cyber risks not explicitly included or excluded, while cyber risk pooling aggregates multiple insurers' cyber risk exposures to enhance capacity and share losses. Both mechanisms mitigate the financial impact of cyber incidents by spreading risk across a broader base, improving market stability, and enabling insurers to offer more comprehensive cyber insurance solutions. The interconnected approach allows for better risk assessment and management in the evolving cyber threat landscape.
Key Terms
Aggregation
Cyber risk pooling aggregates multiple cyber exposures to spread and manage overall loss across participants, reducing individual financial impact and stabilizing premiums. Silent cyber coverage, however, addresses cyber risks not explicitly included or excluded in traditional policies, potentially leading to unforeseen accumulation of aggregation risk and coverage gaps. Explore detailed comparisons to understand their effects on aggregation and risk management strategies.
Explicit Coverage
Explicit coverage in cyber risk pooling clearly defines the scope of cyber threats covered within insurance policies, ensuring transparency and tailored risk management. Silent cyber coverage, by contrast, involves unintentional inclusion of cyber risks in traditional policies without explicit acknowledgment, often leading to ambiguity in claims. Explore explicit coverage to better understand how clear policy terms enhance cyber risk protection.
Risk Transfer
Cyber risk pooling involves multiple insurers sharing cyber risk exposures to enhance financial stability and spread losses, whereas silent cyber coverage refers to unintentional cyber risk assumed under traditional policies not explicitly designed for cyber threats. Risk transfer in cyber risk pooling is deliberate and structured, offering clear terms, while silent cyber coverage generates ambiguous risk transfer, often leading to unexpected claims and coverage disputes. Explore further to understand how precise risk transfer mechanisms affect cyber insurance strategies.
Source and External Links
Cyber Risk Pool | Europe Economics - A cyber risk pool operates as a voluntary coinsurance mechanism, often led by a lead insurer who sets terms and conditions, with multiple insurers sharing risks and claims to promote competition and enhance claims handling quality.
Cyber risk pools and public private partnerships - Cyber risk pools can act as government-backed backstops, providing a financial buffer for catastrophic cyber events, leveraging governments' implicit default responsibility while generating income through premiums and investments.
Public Sector Risk Pools - Cyber Risk Insurance - Tailored cyber risk insurance programs are offered to public sector risk pools, providing customized coverage and risk management tools specific to municipalities and public entities, often including primary policies with aggregate limits and 24/7 claims support.
 dowidth.com
dowidth.com