Trustless computing leverages decentralized networks and cryptographic protocols to enable secure interactions without relying on a central authority, enhancing transparency and data integrity. Zero trust architecture enforces strict identity verification and continuous monitoring to minimize security risks by assuming no implicit trust within the network perimeter. Explore the nuances and applications of these cutting-edge security models to understand their impact on modern technology infrastructure.
Why it is important
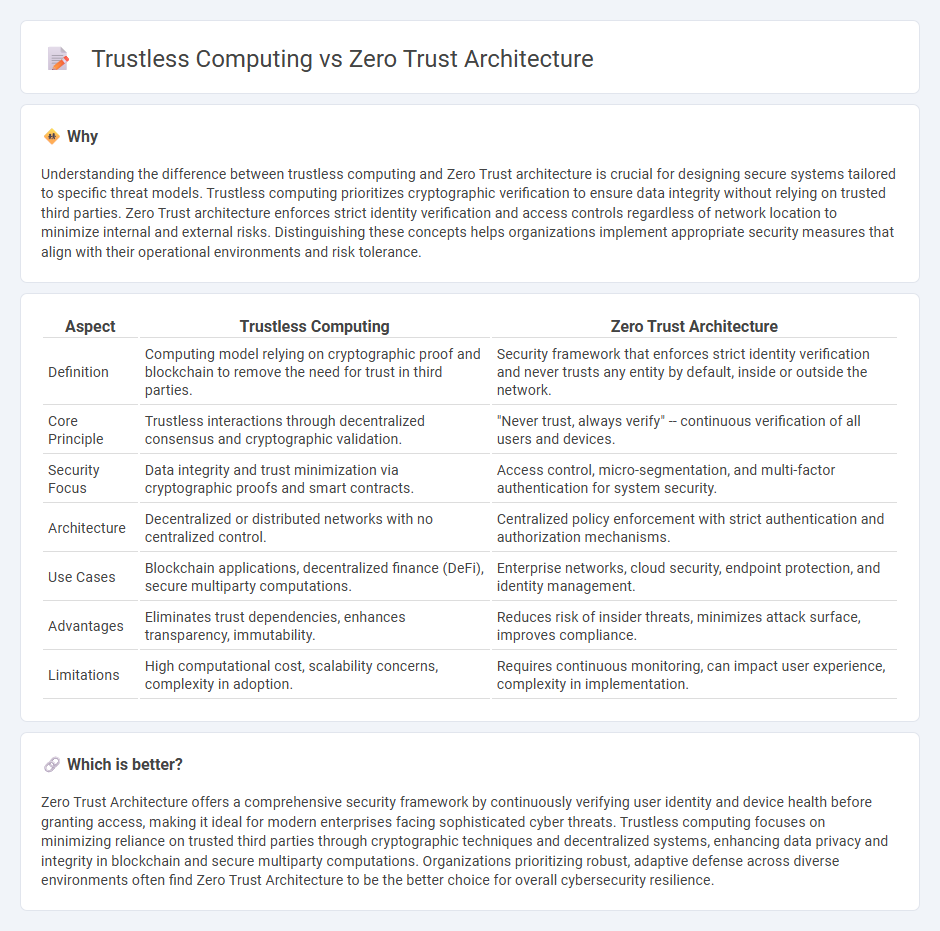
Understanding the difference between trustless computing and Zero Trust architecture is crucial for designing secure systems tailored to specific threat models. Trustless computing prioritizes cryptographic verification to ensure data integrity without relying on trusted third parties. Zero Trust architecture enforces strict identity verification and access controls regardless of network location to minimize internal and external risks. Distinguishing these concepts helps organizations implement appropriate security measures that align with their operational environments and risk tolerance.
Comparison Table
| Aspect | Trustless Computing | Zero Trust Architecture |
|---|---|---|
| Definition | Computing model relying on cryptographic proof and blockchain to remove the need for trust in third parties. | Security framework that enforces strict identity verification and never trusts any entity by default, inside or outside the network. |
| Core Principle | Trustless interactions through decentralized consensus and cryptographic validation. | "Never trust, always verify" -- continuous verification of all users and devices. |
| Security Focus | Data integrity and trust minimization via cryptographic proofs and smart contracts. | Access control, micro-segmentation, and multi-factor authentication for system security. |
| Architecture | Decentralized or distributed networks with no centralized control. | Centralized policy enforcement with strict authentication and authorization mechanisms. |
| Use Cases | Blockchain applications, decentralized finance (DeFi), secure multiparty computations. | Enterprise networks, cloud security, endpoint protection, and identity management. |
| Advantages | Eliminates trust dependencies, enhances transparency, immutability. | Reduces risk of insider threats, minimizes attack surface, improves compliance. |
| Limitations | High computational cost, scalability concerns, complexity in adoption. | Requires continuous monitoring, can impact user experience, complexity in implementation. |
Which is better?
Zero Trust Architecture offers a comprehensive security framework by continuously verifying user identity and device health before granting access, making it ideal for modern enterprises facing sophisticated cyber threats. Trustless computing focuses on minimizing reliance on trusted third parties through cryptographic techniques and decentralized systems, enhancing data privacy and integrity in blockchain and secure multiparty computations. Organizations prioritizing robust, adaptive defense across diverse environments often find Zero Trust Architecture to be the better choice for overall cybersecurity resilience.
Connection
Trustless computing leverages cryptographic protocols to enable secure transactions without relying on a trusted intermediary, aligning seamlessly with Zero Trust Architecture principles that assume no implicit trust within network boundaries. Zero Trust Architecture enforces continuous verification and strict access controls, which complement trustless computing's emphasis on decentralized, tamper-resistant trust mechanisms. Together, they create robust cybersecurity frameworks that minimize vulnerabilities by eliminating single points of trust and enabling secure interactions across distributed systems.
Key Terms
Identity Verification
Zero Trust Architecture strictly enforces identity verification by continuously validating user credentials and access rights before granting entry to any resource, minimizing the risk of unauthorized access. Trustless computing leverages cryptographic proofs and decentralized protocols to ensure transactions and data exchanges are secure without relying on pre-established trust between parties. Explore how both approaches redefine security models and enhance identity verification frameworks for modern digital environments.
Decentralization
Zero trust architecture eliminates implicit trust by continuously verifying every user and device within a network, enhancing security in centralized systems. Trustless computing leverages decentralized networks, like blockchain, to ensure transactions and operations occur without relying on a single trusted authority. Explore the differences between these approaches to understand their impact on security and decentralization.
Access Control
Zero trust architecture enforces strict identity verification for every user and device, regardless of network location, ensuring access control based on continuous authentication and least-privilege principles. Trustless computing eliminates the need for inherent trust by leveraging cryptographic proofs, such as blockchain and secure multiparty computation, to validate access and transactions without relying on a central authority. Explore how these models revolutionize access control and security frameworks by learning more about their practical implementations and benefits.
Source and External Links
Zero trust architecture - Wikipedia - Zero trust architecture (ZTA) is a security model where no user or device is trusted by default, requiring continuous identity verification, device compliance checks, and least-privilege access, even for those inside the corporate network.
What is Zero Trust Architecture (ZTA)? - CrowdStrike - Zero Trust Architecture is a framework that enforces continuous authentication and authorization for all users and devices, denies access by default, and integrates real-time monitoring and controls to detect and respond to threats.
What Is a Zero Trust Architecture? - Zscaler - Zero trust architecture decouples security from the network, enabling secure, one-to-one connections between users, devices, and applications based on identity verification, risk assessment, and real-time policy enforcement regardless of location.
 dowidth.com
dowidth.com