Trustless computing ensures secure transactions and data integrity through decentralized verification methods such as blockchain, eliminating the need for a central trusted authority. Trusted computing relies on hardware-based security measures like Trusted Platform Modules (TPMs) to create a secure execution environment enabling software attestation and protection against tampering. Explore how trustless and trusted computing shape the future of secure digital interactions.
Why it is important
Understanding the difference between trustless computing and trusted computing is crucial for designing secure decentralized systems and protecting data integrity. Trustless computing leverages cryptographic protocols to enable transactions without relying on a central authority, enhancing transparency and reducing single points of failure. Trusted computing uses hardware-based security modules like Trusted Platform Modules (TPM) to establish a root of trust and safeguard sensitive operations. Distinguishing these approaches informs technology selection for applications in blockchain, cybersecurity, and privacy-sensitive environments.
Comparison Table
| Aspect | Trustless Computing | Trusted Computing |
|---|---|---|
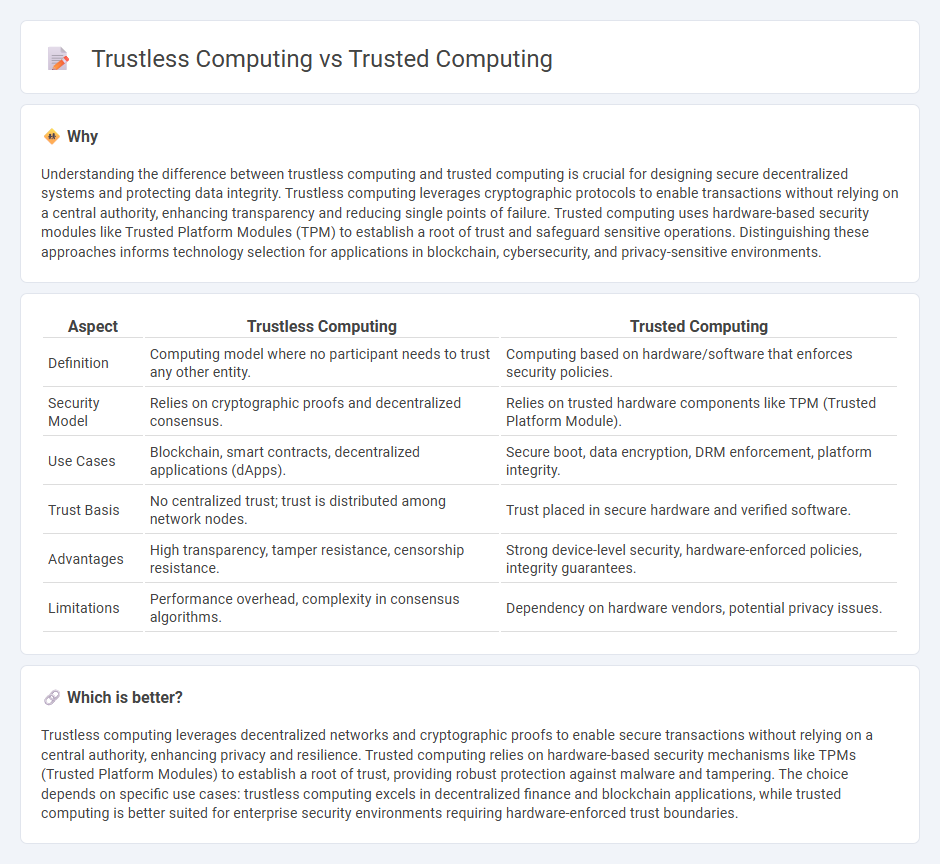
| Definition | Computing model where no participant needs to trust any other entity. | Computing based on hardware/software that enforces security policies. |
| Security Model | Relies on cryptographic proofs and decentralized consensus. | Relies on trusted hardware components like TPM (Trusted Platform Module). |
| Use Cases | Blockchain, smart contracts, decentralized applications (dApps). | Secure boot, data encryption, DRM enforcement, platform integrity. |
| Trust Basis | No centralized trust; trust is distributed among network nodes. | Trust placed in secure hardware and verified software. |
| Advantages | High transparency, tamper resistance, censorship resistance. | Strong device-level security, hardware-enforced policies, integrity guarantees. |
| Limitations | Performance overhead, complexity in consensus algorithms. | Dependency on hardware vendors, potential privacy issues. |
Which is better?
Trustless computing leverages decentralized networks and cryptographic proofs to enable secure transactions without relying on a central authority, enhancing privacy and resilience. Trusted computing relies on hardware-based security mechanisms like TPMs (Trusted Platform Modules) to establish a root of trust, providing robust protection against malware and tampering. The choice depends on specific use cases: trustless computing excels in decentralized finance and blockchain applications, while trusted computing is better suited for enterprise security environments requiring hardware-enforced trust boundaries.
Connection
Trustless computing utilizes cryptographic protocols to enable secure transactions without relying on trusted intermediaries, while Trusted computing relies on hardware-based security modules to establish a secure and verifiable environment. Both concepts aim to enhance security and integrity in digital systems by minimizing trust assumptions, with trusted computing providing the foundational hardware trust anchors that support trustless protocols. The integration of trusted computing hardware in blockchain and decentralized applications facilitates trustless computing by ensuring that code execution and data management remain tamper-proof and verifiable.
Key Terms
Hardware Security Module (HSM)
Trusted computing relies on Hardware Security Modules (HSMs) to provide secure key storage, cryptographic operations, and hardware-based protection against tampering and unauthorized access. Trustless computing emphasizes decentralized and verifiable environments, minimizing reliance on a single hardware root of trust like an HSM. Explore the benefits and limitations of HSMs within trusted and trustless paradigms to understand their roles in enhancing security.
Blockchain
Trusted computing relies on hardware-based security modules and centralized authorities to ensure data integrity and system reliability, often integrating secure enclaves like Intel SGX for protected execution. Trustless computing, fundamental to blockchain technology, eliminates the need for centralized trust by using decentralized consensus algorithms such as Proof of Work or Proof of Stake to validate transactions and maintain ledger integrity. Explore the detailed mechanisms and trade-offs between trusted and trustless systems in blockchain technology to better understand their impact on security and decentralization.
Remote Attestation
Trusted computing relies on hardware-based root of trust and Remote Attestation to verify the integrity of a system before execution, ensuring that software and configurations are secure and unaltered. Trustless computing, often implemented in blockchain environments, eliminates the need for a central authority by using cryptographic proofs and consensus mechanisms to validate transactions and code execution. Explore deeper to understand how Remote Attestation fundamentally differentiates security models in trusted and trustless systems.
Source and External Links
Trusted Computing - Wikipedia - Trusted Computing (TC) is a technology promoted by the Trusted Computing Group ensuring a computer behaves in expected ways enforced by hardware and software, using unique encryption keys, but is controversial due to concerns over owner restrictions and digital rights management enforcement.
The essential building blocks to a secure system - Trusted Computing Group - Trusted Computing leverages hardware Roots of Trust and encryption to secure platforms by ensuring sensitive data and keys are accessible only on systems with identical hardware-software configurations, enhancing resilience against malware and unauthorized access.
Trusted Computing Base (TCB) in Azure Confidential Computing - Microsoft Docs - The Trusted Computing Base includes all critical hardware, firmware, and software components providing a secure environment, where hardware roots of trust validate workloads inside a Trusted Execution Environment, shielding them from host OS and hypervisor visibility through encryption.
 dowidth.com
dowidth.com