Quantum key distribution (QKD) leverages principles of quantum mechanics to enable secure communication by generating shared cryptographic keys immune to eavesdropping. Hash-based cryptography relies on the computational difficulty of hash functions to ensure data integrity and authentication, offering post-quantum security resilience. Explore the detailed comparisons and practical applications of QKD versus hash-based cryptography to understand their roles in advancing cybersecurity.
Why it is important
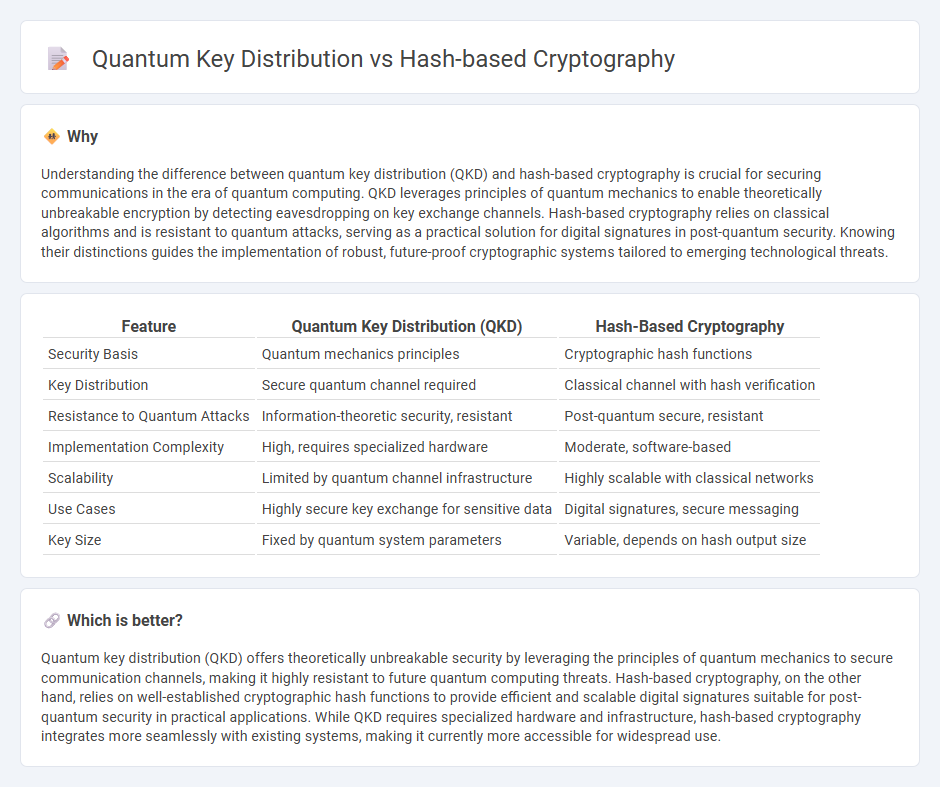
Understanding the difference between quantum key distribution (QKD) and hash-based cryptography is crucial for securing communications in the era of quantum computing. QKD leverages principles of quantum mechanics to enable theoretically unbreakable encryption by detecting eavesdropping on key exchange channels. Hash-based cryptography relies on classical algorithms and is resistant to quantum attacks, serving as a practical solution for digital signatures in post-quantum security. Knowing their distinctions guides the implementation of robust, future-proof cryptographic systems tailored to emerging technological threats.
Comparison Table
| Feature | Quantum Key Distribution (QKD) | Hash-Based Cryptography |
|---|---|---|
| Security Basis | Quantum mechanics principles | Cryptographic hash functions |
| Key Distribution | Secure quantum channel required | Classical channel with hash verification |
| Resistance to Quantum Attacks | Information-theoretic security, resistant | Post-quantum secure, resistant |
| Implementation Complexity | High, requires specialized hardware | Moderate, software-based |
| Scalability | Limited by quantum channel infrastructure | Highly scalable with classical networks |
| Use Cases | Highly secure key exchange for sensitive data | Digital signatures, secure messaging |
| Key Size | Fixed by quantum system parameters | Variable, depends on hash output size |
Which is better?
Quantum key distribution (QKD) offers theoretically unbreakable security by leveraging the principles of quantum mechanics to secure communication channels, making it highly resistant to future quantum computing threats. Hash-based cryptography, on the other hand, relies on well-established cryptographic hash functions to provide efficient and scalable digital signatures suitable for post-quantum security in practical applications. While QKD requires specialized hardware and infrastructure, hash-based cryptography integrates more seamlessly with existing systems, making it currently more accessible for widespread use.
Connection
Quantum key distribution (QKD) leverages quantum mechanics principles to enable secure exchange of cryptographic keys, ensuring detection of eavesdropping. Hash-based cryptography provides post-quantum security by using cryptographic hash functions resistant to quantum attacks, complementing QKD in securing digital communication. Combining QKD with hash-based cryptographic methods enhances overall security by integrating quantum-resistant key distribution with robust digital signature schemes.
Key Terms
Post-quantum security
Hash-based cryptography offers a practical approach to post-quantum security by leveraging the hardness of hash functions, which are resistant to attacks from quantum computers. Quantum key distribution (QKD) utilizes principles of quantum mechanics to enable theoretically unbreakable communication, but it requires specialized hardware and suffers from distance limitations. Explore the differences between these cutting-edge methods to understand their applications in securing communications against future quantum threats.
One-way hash functions
One-way hash functions are fundamental in hash-based cryptography, providing secure, irreversible mappings essential for digital signatures and data integrity in classical and post-quantum contexts. Unlike quantum key distribution (QKD), which relies on quantum states and entanglement to enable theoretically unbreakable key exchange, hash-based methods do not require quantum channels and are resistant to quantum attacks based on their mathematical properties. Explore how one-way hash functions underpin practical quantum-resistant solutions beyond QKD frameworks to secure future communications.
Quantum entanglement
Hash-based cryptography relies on the collision resistance of cryptographic hash functions to secure digital signatures against quantum attacks, while quantum key distribution (QKD) leverages quantum entanglement to enable provably secure communication by detecting eavesdropping through quantum state disturbances. Quantum entanglement, a phenomenon where particles become linked such that the state of one instantly influences the state of another, underpins QKD protocols like BB84 and E91, ensuring unbreakable encryption keys based on fundamental physics rather than computational hardness assumptions. Explore the cutting-edge implications of quantum entanglement in quantum key distribution and its role in future-proofing cybersecurity.
Source and External Links
Hash-based cryptography - Hash-based cryptography refers to cryptographic constructions based on hash functions, prominent in post-quantum cryptography for digital signature schemes like the Merkle signature scheme; key standards include XMSS, LMS, and the recently announced Stateless Hash-Based Digital Signature Standard by NIST in 2024.
Post-quantum cryptography: Hash-based signatures - Hash-based signatures create secure digital signatures by using random value pairs hashed into public keys, relying on hash functions' preimage resistance to ensure security against quantum attacks, making them a well-studied candidate for post-quantum cryptography.
Hash-based Signatures: An illustrated Primer - Hash-based signature schemes, originating from Lamport and Merkle, sign messages by selecting secret random strings based on message bits and verify signatures through hash checks, illustrating a simple yet robust cryptographic approach.
 dowidth.com
dowidth.com