Decentralized identity leverages blockchain and cryptographic techniques to provide users with control over their personal data, reducing reliance on centralized authorities. Password-based authentication depends on traditional username-password pairs, which are vulnerable to breaches, phishing, and credential reuse attacks. Explore the advantages and challenges of these authentication methods to enhance your digital security understanding.
Why it is important
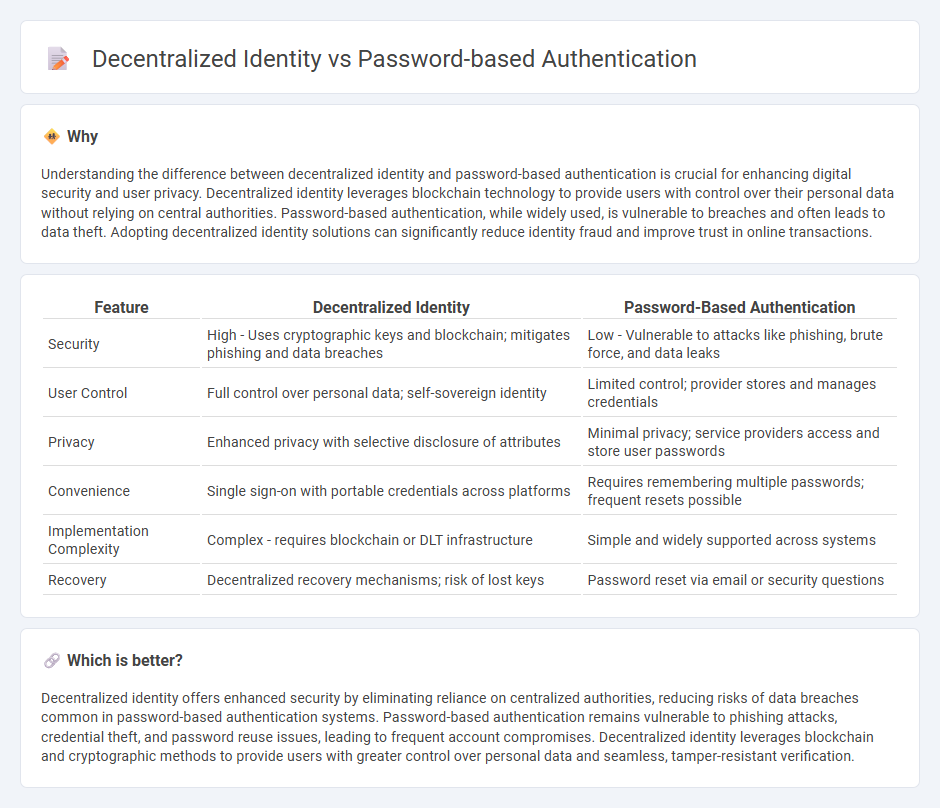
Understanding the difference between decentralized identity and password-based authentication is crucial for enhancing digital security and user privacy. Decentralized identity leverages blockchain technology to provide users with control over their personal data without relying on central authorities. Password-based authentication, while widely used, is vulnerable to breaches and often leads to data theft. Adopting decentralized identity solutions can significantly reduce identity fraud and improve trust in online transactions.
Comparison Table
| Feature | Decentralized Identity | Password-Based Authentication |
|---|---|---|
| Security | High - Uses cryptographic keys and blockchain; mitigates phishing and data breaches | Low - Vulnerable to attacks like phishing, brute force, and data leaks |
| User Control | Full control over personal data; self-sovereign identity | Limited control; provider stores and manages credentials |
| Privacy | Enhanced privacy with selective disclosure of attributes | Minimal privacy; service providers access and store user passwords |
| Convenience | Single sign-on with portable credentials across platforms | Requires remembering multiple passwords; frequent resets possible |
| Implementation Complexity | Complex - requires blockchain or DLT infrastructure | Simple and widely supported across systems |
| Recovery | Decentralized recovery mechanisms; risk of lost keys | Password reset via email or security questions |
Which is better?
Decentralized identity offers enhanced security by eliminating reliance on centralized authorities, reducing risks of data breaches common in password-based authentication systems. Password-based authentication remains vulnerable to phishing attacks, credential theft, and password reuse issues, leading to frequent account compromises. Decentralized identity leverages blockchain and cryptographic methods to provide users with greater control over personal data and seamless, tamper-resistant verification.
Connection
Decentralized identity leverages blockchain and cryptographic methods to give users control over their personal data without relying on centralized authorities, enhancing security and privacy. Password-based authentication, traditionally dependent on centralized databases vulnerable to breaches, can be integrated with decentralized identity by enabling users to authenticate via cryptographic keys linked to their identity wallets. This connection reduces reliance on passwords alone, improving security while facilitating seamless and user-centric access management in digital environments.
Key Terms
Credentials
Password-based authentication relies on centralized storage of credentials, making systems vulnerable to data breaches and phishing attacks. Decentralized identity leverages cryptographic verifiable credentials stored on user-controlled devices or distributed ledgers, enhancing security and privacy by eliminating single points of failure. Explore how decentralized identity transforms credential management and strengthens authentication security.
Blockchain
Password-based authentication relies on centralized databases vulnerable to breaches, whereas decentralized identity leverages blockchain for secure, tamper-proof user credentials stored on distributed ledgers. Blockchain enhances privacy, reduces fraud, and empowers users with self-sovereign identity control, eliminating single points of failure common in traditional systems. Explore how blockchain-based decentralized identity transforms authentication security and user autonomy.
Private key
Password-based authentication relies on users memorizing and entering passwords, which are vulnerable to theft, phishing, and brute-force attacks. Decentralized identity leverages private key cryptography, where the private key remains securely stored on the user's device, enabling stronger security and eliminating reliance on centralized servers. Explore how private key management in decentralized identity enhances user control and security.
Source and External Links
Password-Based Authentication vs. Passwordless Authentication: A Comprehensive Comparison - Password-based authentication relies on a username and confidential password that users input to verify identity, is widely familiar and cost-effective, but vulnerable to weak passwords and reuse which can create security risks.
What is Password-Based Authentication? - Password-based authentication requires a user to enter credentials (username and password) that are checked against stored encrypted credentials in a system, granting access only if they match; despite security concerns, 59% of businesses still use it.
Password Authentication Protocol - Password Authentication Protocol (PAP) is a basic password-based authentication protocol used by Point-to-Point Protocol (PPP) that sends passwords in cleartext and is considered weak, often replaced by more secure methods like CHAP or TLS where security is critical.
 dowidth.com
dowidth.com