Blockchain oracles serve as bridges that securely transmit real-world data to smart contracts, enabling decentralized applications to interact with external information. Trusted Execution Environments (TEEs) create isolated, tamper-proof areas within processors to execute sensitive code and protect data confidentiality from the host system. Explore the differences and applications of blockchain oracles and TEEs to understand their roles in enhancing decentralized security.
Why it is important
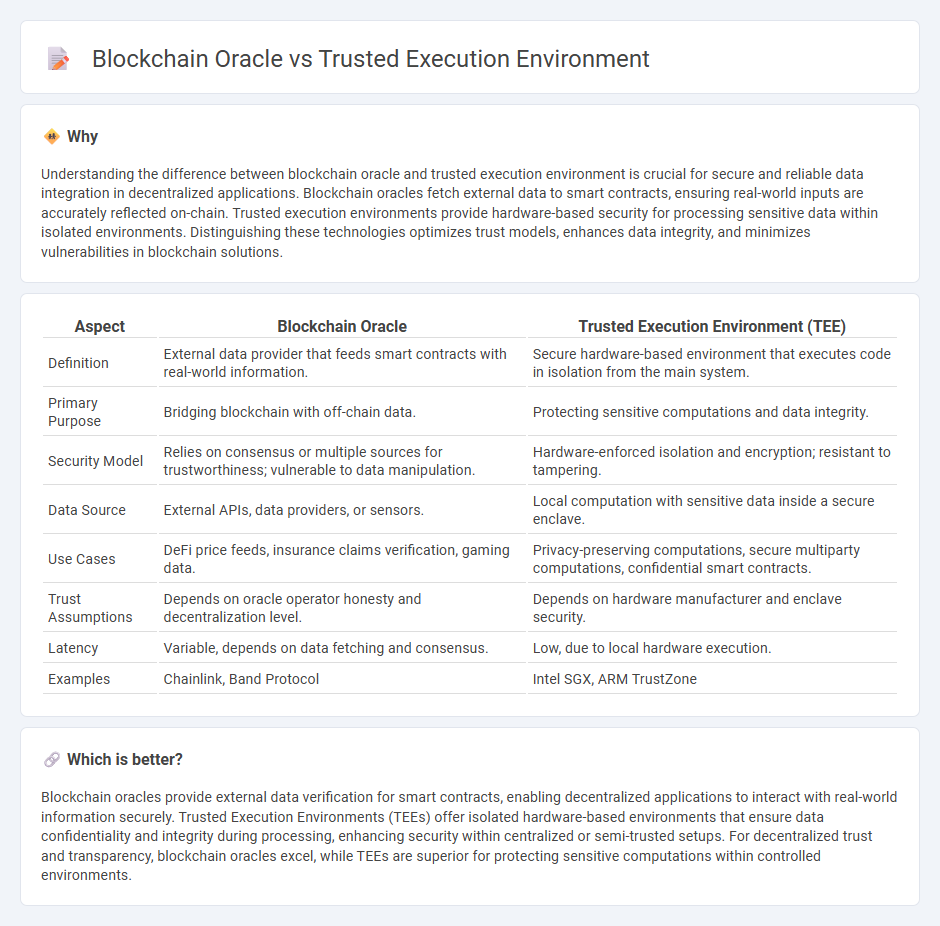
Understanding the difference between blockchain oracle and trusted execution environment is crucial for secure and reliable data integration in decentralized applications. Blockchain oracles fetch external data to smart contracts, ensuring real-world inputs are accurately reflected on-chain. Trusted execution environments provide hardware-based security for processing sensitive data within isolated environments. Distinguishing these technologies optimizes trust models, enhances data integrity, and minimizes vulnerabilities in blockchain solutions.
Comparison Table
| Aspect | Blockchain Oracle | Trusted Execution Environment (TEE) |
|---|---|---|
| Definition | External data provider that feeds smart contracts with real-world information. | Secure hardware-based environment that executes code in isolation from the main system. |
| Primary Purpose | Bridging blockchain with off-chain data. | Protecting sensitive computations and data integrity. |
| Security Model | Relies on consensus or multiple sources for trustworthiness; vulnerable to data manipulation. | Hardware-enforced isolation and encryption; resistant to tampering. |
| Data Source | External APIs, data providers, or sensors. | Local computation with sensitive data inside a secure enclave. |
| Use Cases | DeFi price feeds, insurance claims verification, gaming data. | Privacy-preserving computations, secure multiparty computations, confidential smart contracts. |
| Trust Assumptions | Depends on oracle operator honesty and decentralization level. | Depends on hardware manufacturer and enclave security. |
| Latency | Variable, depends on data fetching and consensus. | Low, due to local hardware execution. |
| Examples | Chainlink, Band Protocol | Intel SGX, ARM TrustZone |
Which is better?
Blockchain oracles provide external data verification for smart contracts, enabling decentralized applications to interact with real-world information securely. Trusted Execution Environments (TEEs) offer isolated hardware-based environments that ensure data confidentiality and integrity during processing, enhancing security within centralized or semi-trusted setups. For decentralized trust and transparency, blockchain oracles excel, while TEEs are superior for protecting sensitive computations within controlled environments.
Connection
Blockchain oracles and Trusted Execution Environments (TEEs) connect by enhancing smart contract reliability; oracles feed external, real-world data into blockchain systems, while TEEs provide a secure area within a processor to execute code confidentially and protect data integrity. This combination addresses the oracle problem by ensuring that the data input into the blockchain remains tamper-proof and verifiable through cryptographic attestation within the TEE. Together, they enable trustless environments for decentralized applications that require accurate and secure off-chain information.
Key Terms
Hardware-based Security (TEE)
Trusted Execution Environments (TEEs) provide hardware-based security by creating isolated environments within a processor, ensuring sensitive data and code execute securely against external threats. Blockchain oracles, while crucial for connecting off-chain data to smart contracts, generally rely on software or third-party providers without native hardware isolation, making TEEs more robust in preventing tampering and data leaks. Explore the unique advantages of TEEs in enhancing trusted computation beyond traditional oracle solutions.
Decentralized Validation (Blockchain Oracle)
Decentralized validation in blockchain oracles leverages multiple independent nodes to verify and deliver accurate off-chain data to smart contracts, enhancing security by reducing reliance on a single source. Unlike Trusted Execution Environments (TEEs), which secure computations within isolated hardware, blockchain oracles provide transparency and consensus-driven data authenticity critical for decentralized applications. Explore more about how decentralized validation strengthens the integrity of blockchain ecosystems.
Data Integrity
A Trusted Execution Environment (TEE) ensures data integrity by creating a secure, isolated environment within hardware, preventing unauthorized access and tampering during execution. Blockchain oracles provide data integrity by verifying and transmitting real-world data onto the blockchain, relying on cryptographic proofs and multiple data sources to minimize manipulation risks. Explore how combining TEEs and blockchain oracles can enhance data integrity in decentralized applications.
Source and External Links
Trusted execution environment - Wikipedia - A Trusted Execution Environment (TEE) is a secure area of a main processor that protects the confidentiality and integrity of the code and data loaded inside it, isolating them from unauthorized access including software and hardware attacks, by using hardware-based memory encryption and architectural security features.
What Is Trusted Execution Environment (TEE) & How Does It Work? - A TEE provides a highly trustworthy execution environment by securely starting up, only running authorized code, isolating application data, and attesting its trustworthy state, thereby protecting code and data from unauthorized access and modification.
Introduction to Trusted Execution Environments | GlobalPlatform - The TEE is a secure processor area that isolates sensitive data and trusted applications from the main operating system and other applications, providing protection against software attacks while enabling fast processing and controlled data access.
 dowidth.com
dowidth.com