eBPF (extended Berkeley Packet Filter) offers a modern, efficient way to run sandboxed programs in the Linux kernel, providing advanced observability and security features with minimal performance overhead. SystemTap, a traditional Linux tracing tool, enables dynamic instrumentation for deep system analysis but may introduce higher latency and complexity. Explore the key differences between eBPF and SystemTap to enhance your Linux system monitoring strategies.
Why it is important
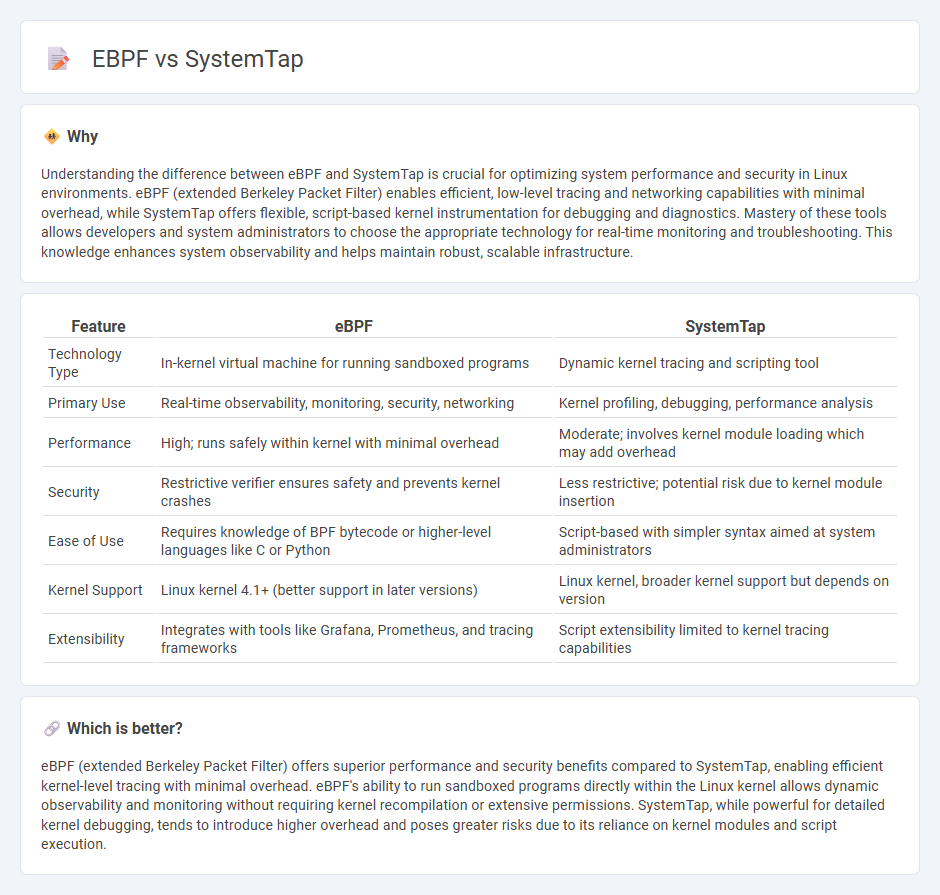
Understanding the difference between eBPF and SystemTap is crucial for optimizing system performance and security in Linux environments. eBPF (extended Berkeley Packet Filter) enables efficient, low-level tracing and networking capabilities with minimal overhead, while SystemTap offers flexible, script-based kernel instrumentation for debugging and diagnostics. Mastery of these tools allows developers and system administrators to choose the appropriate technology for real-time monitoring and troubleshooting. This knowledge enhances system observability and helps maintain robust, scalable infrastructure.
Comparison Table
| Feature | eBPF | SystemTap |
|---|---|---|
| Technology Type | In-kernel virtual machine for running sandboxed programs | Dynamic kernel tracing and scripting tool |
| Primary Use | Real-time observability, monitoring, security, networking | Kernel profiling, debugging, performance analysis |
| Performance | High; runs safely within kernel with minimal overhead | Moderate; involves kernel module loading which may add overhead |
| Security | Restrictive verifier ensures safety and prevents kernel crashes | Less restrictive; potential risk due to kernel module insertion |
| Ease of Use | Requires knowledge of BPF bytecode or higher-level languages like C or Python | Script-based with simpler syntax aimed at system administrators |
| Kernel Support | Linux kernel 4.1+ (better support in later versions) | Linux kernel, broader kernel support but depends on version |
| Extensibility | Integrates with tools like Grafana, Prometheus, and tracing frameworks | Script extensibility limited to kernel tracing capabilities |
Which is better?
eBPF (extended Berkeley Packet Filter) offers superior performance and security benefits compared to SystemTap, enabling efficient kernel-level tracing with minimal overhead. eBPF's ability to run sandboxed programs directly within the Linux kernel allows dynamic observability and monitoring without requiring kernel recompilation or extensive permissions. SystemTap, while powerful for detailed kernel debugging, tends to introduce higher overhead and poses greater risks due to its reliance on kernel modules and script execution.
Connection
eBPF (extended Berkeley Packet Filter) and SystemTap both enable dynamic probing and tracing of Linux kernel events for performance analysis and debugging. eBPF allows safe execution of sandboxed programs within the kernel, providing fine-grained instrumentation with low overhead. SystemTap uses kernel instrumentation points and can leverage eBPF as a backend to enhance tracing capabilities and improve safety.
Key Terms
Kernel Instrumentation
SystemTap provides comprehensive kernel instrumentation using scripts that enable deep tracing, but it requires kernel module compilation and may introduce overhead. eBPF offers efficient, dynamic kernel tracing with minimal performance impact by running sandboxed programs within the kernel, supporting advanced observability and security use cases. Explore the advantages and limitations of both tools to determine the best fit for your kernel instrumentation needs.
Dynamic Tracing
SystemTap enables powerful dynamic tracing of Linux kernel and user-space applications using scripted probes, facilitating in-depth performance analysis and troubleshooting. eBPF offers lightweight, efficient tracing by running custom programs safely within the kernel, providing high scalability and low overhead for real-time monitoring. Explore deeper differences and use cases of SystemTap and eBPF to optimize your dynamic tracing strategy.
Event Probes
SystemTap and eBPF both enable event probe-based monitoring in Linux, with SystemTap relying on kernel module loading and eBPF using in-kernel virtual machines for safer dynamic tracing. eBPF offers superior performance and flexibility by running sandboxed programs in the kernel, while SystemTap provides extensive scripting capabilities for complex event probing. Explore the technical details and use cases to determine which event probe tool suits your Linux monitoring needs best.
Source and External Links
SystemTap Beginners Guide | Red Hat Enterprise Linux | 7 - SystemTap is a Linux tracing and probing tool that compiles scripts into kernel modules to monitor and analyze system and kernel activity in real time.
SystemTap - Wikipedia - SystemTap is a free, open-source scripting tool and language for dynamically instrumenting live Linux systems, widely used for diagnosing complex performance and functional issues.
SystemTap - Sourceware - SystemTap simplifies gathering detailed information about a running Linux system, eliminating the need to instrument, recompile, and reboot, and is especially suited for complex, live system analysis.
 dowidth.com
dowidth.com