eBPF (extended Berkeley Packet Filter) enables dynamic, programmable kernel-level monitoring and security, offering fine-grained control over system behavior without modifying kernel source code. SELinux (Security-Enhanced Linux) provides a robust mandatory access control framework enforcing strict security policies to confine processes and limit their capabilities. Explore deeper to understand how eBPF's flexibility compares to SELinux's policy enforcement in enhancing Linux system security.
Why it is important
Understanding the difference between eBPF and SELinux is crucial for optimizing system security and performance; eBPF extends kernel capabilities by executing user-defined programs safely, while SELinux enforces mandatory access controls to restrict system resources. eBPF offers dynamic, programmable networking and monitoring, improving flexibility and debugging, whereas SELinux provides static, policy-based security to prevent unauthorized access. Knowing their roles helps system administrators deploy the right technology for specific security and performance needs. This knowledge enhances efficient resource management and strengthens overall system protection strategies.
Comparison Table
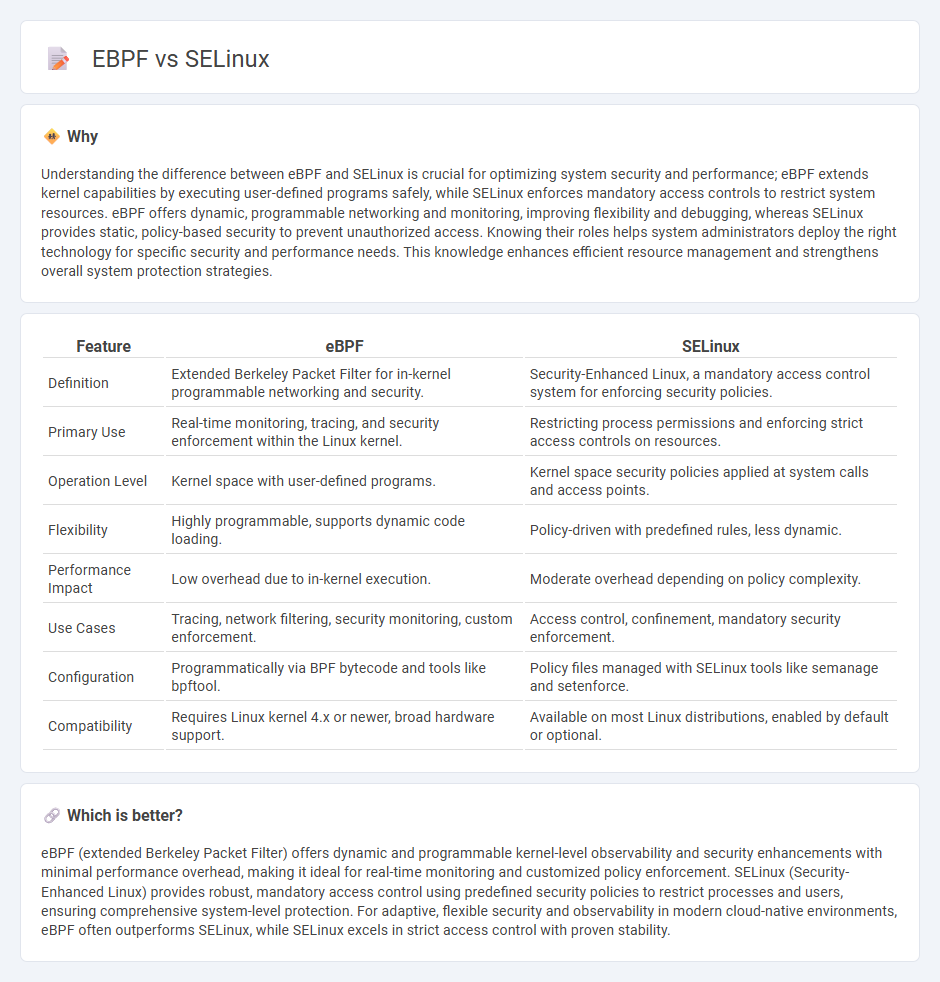
| Feature | eBPF | SELinux |
|---|---|---|
| Definition | Extended Berkeley Packet Filter for in-kernel programmable networking and security. | Security-Enhanced Linux, a mandatory access control system for enforcing security policies. |
| Primary Use | Real-time monitoring, tracing, and security enforcement within the Linux kernel. | Restricting process permissions and enforcing strict access controls on resources. |
| Operation Level | Kernel space with user-defined programs. | Kernel space security policies applied at system calls and access points. |
| Flexibility | Highly programmable, supports dynamic code loading. | Policy-driven with predefined rules, less dynamic. |
| Performance Impact | Low overhead due to in-kernel execution. | Moderate overhead depending on policy complexity. |
| Use Cases | Tracing, network filtering, security monitoring, custom enforcement. | Access control, confinement, mandatory security enforcement. |
| Configuration | Programmatically via BPF bytecode and tools like bpftool. | Policy files managed with SELinux tools like semanage and setenforce. |
| Compatibility | Requires Linux kernel 4.x or newer, broad hardware support. | Available on most Linux distributions, enabled by default or optional. |
Which is better?
eBPF (extended Berkeley Packet Filter) offers dynamic and programmable kernel-level observability and security enhancements with minimal performance overhead, making it ideal for real-time monitoring and customized policy enforcement. SELinux (Security-Enhanced Linux) provides robust, mandatory access control using predefined security policies to restrict processes and users, ensuring comprehensive system-level protection. For adaptive, flexible security and observability in modern cloud-native environments, eBPF often outperforms SELinux, while SELinux excels in strict access control with proven stability.
Connection
eBPF (extended Berkeley Packet Filter) enhances SELinux by providing dynamic, programmable kernel-level monitoring and enforcement capabilities, enabling more granular security policies. SELinux uses eBPF to implement fine-grained access controls and real-time auditing without compromising system performance. This integration strengthens Linux security frameworks by combining SELinux's mandatory access controls with eBPF's efficient event filtering and handling.
Key Terms
Access Control (SELinux)
SELinux enforces mandatory access control policies within the Linux kernel, restricting process capabilities and file access based on predefined security contexts to enhance system security and prevent unauthorized actions. eBPF, while powerful for monitoring and custom packet processing, lacks native access control enforcement like SELinux and is primarily used for observability and dynamic tracing. Explore how SELinux's robust access control model uniquely secures systems beyond the dynamic capabilities of eBPF.
Packet Filtering (eBPF)
SELinux provides mandatory access control policies to enforce security at the system call and process level, while eBPF (extended Berkeley Packet Filter) offers advanced packet filtering by executing custom programs directly in the Linux kernel with high efficiency. eBPF enables dynamic and fine-grained network traffic analysis and filtering, surpassing traditional iptables performance and flexibility. Explore the latest developments in eBPF packet filtering to enhance network security and performance.
Kernel Security (Both)
SELinux enforces mandatory access control policies to restrict application behavior and protect the kernel from unauthorized access, ensuring system integrity through security labels and fine-grained permissions. eBPF extends kernel security by enabling dynamic, programmable monitoring and filtering of system events at runtime, offering enhanced visibility and custom security enforcement without modifying kernel code. Explore the synergies and differences between SELinux and eBPF to deepen your understanding of Linux kernel security architectures.
Source and External Links
What is SELinux? - Red Hat - SELinux is a Linux security architecture that gives administrators detailed control over access permissions for processes and files, enforcing rules through a policy-based mandatory access control system.
Introduction | Security-Enhanced Linux | Red Hat Enterprise Linux 6 - SELinux implements mandatory access controls in the Linux kernel, enforcing strict policies on what system resources can be accessed by specific processes, adding robust protection beyond traditional discretionary access controls.
Security-Enhanced Linux - Wikipedia - SELinux is a Linux kernel security module that supports advanced access control policies, defaults to a deny-all stance, and separates policy enforcement from policy decision-making for high-security environments.
 dowidth.com
dowidth.com