Quantum key distribution (QKD) leverages the principles of quantum mechanics to enable secure communication by detecting eavesdropping on encryption keys. Post-quantum cryptography (PQC) focuses on developing classical encryption algorithms resistant to attacks from quantum computers, ensuring data security once quantum computers become widespread. Explore the differences and applications of these groundbreaking technologies to secure your information in the quantum era.
Why it is important
Understanding the difference between quantum key distribution (QKD) and post-quantum cryptography (PQC) is crucial for implementing future-proof security measures in the era of quantum computing. QKD leverages the principles of quantum mechanics to enable secure communication by detecting eavesdropping through quantum states, while PQC involves developing cryptographic algorithms resistant to quantum attacks on classical computers. Organizations need to choose the appropriate technology based on their infrastructure and threat models to protect sensitive data effectively. Knowing these distinctions ensures robust cybersecurity strategies against quantum-enabled threats.
Comparison Table
| Feature | Quantum Key Distribution (QKD) | Post-Quantum Cryptography (PQC) |
|---|---|---|
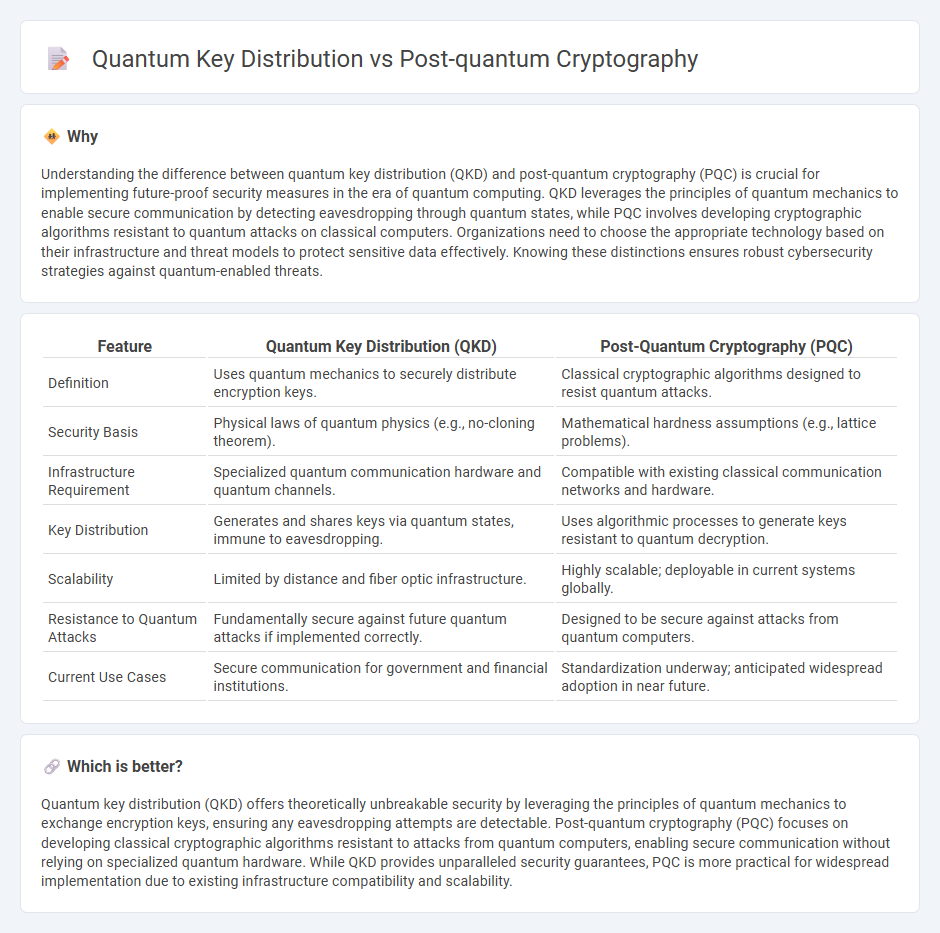
| Definition | Uses quantum mechanics to securely distribute encryption keys. | Classical cryptographic algorithms designed to resist quantum attacks. |
| Security Basis | Physical laws of quantum physics (e.g., no-cloning theorem). | Mathematical hardness assumptions (e.g., lattice problems). |
| Infrastructure Requirement | Specialized quantum communication hardware and quantum channels. | Compatible with existing classical communication networks and hardware. |
| Key Distribution | Generates and shares keys via quantum states, immune to eavesdropping. | Uses algorithmic processes to generate keys resistant to quantum decryption. |
| Scalability | Limited by distance and fiber optic infrastructure. | Highly scalable; deployable in current systems globally. |
| Resistance to Quantum Attacks | Fundamentally secure against future quantum attacks if implemented correctly. | Designed to be secure against attacks from quantum computers. |
| Current Use Cases | Secure communication for government and financial institutions. | Standardization underway; anticipated widespread adoption in near future. |
Which is better?
Quantum key distribution (QKD) offers theoretically unbreakable security by leveraging the principles of quantum mechanics to exchange encryption keys, ensuring any eavesdropping attempts are detectable. Post-quantum cryptography (PQC) focuses on developing classical cryptographic algorithms resistant to attacks from quantum computers, enabling secure communication without relying on specialized quantum hardware. While QKD provides unparalleled security guarantees, PQC is more practical for widespread implementation due to existing infrastructure compatibility and scalability.
Connection
Quantum key distribution (QKD) uses quantum mechanics to securely exchange encryption keys, ensuring information-theoretic security against eavesdropping. Post-quantum cryptography (PQC) develops classical algorithms resistant to attacks by quantum computers, addressing potential vulnerabilities in traditional cryptographic systems. Both QKD and PQC aim to safeguard data confidentiality in the emerging era of quantum computing threats.
Key Terms
Lattice-based cryptography
Lattice-based cryptography, a cornerstone of post-quantum cryptography, offers practical encryption and digital signature schemes resistant to quantum attacks, relying on hard mathematical problems like Learning With Errors (LWE). Unlike quantum key distribution (QKD), which requires specialized quantum communication channels for secure key exchange, lattice-based methods operate efficiently on classical networks, enabling widespread adoption without quantum hardware. Explore the distinctions and advantages of lattice-based cryptography to secure digital communication against future quantum threats.
Quantum entanglement
Quantum entanglement is a fundamental principle utilized in quantum key distribution (QKD) to generate secure encryption keys based on the correlated quantum states of entangled particles, ensuring high levels of security against eavesdropping. Post-quantum cryptography (PQC) relies on classical algorithms designed to resist attacks from quantum computers but does not inherently employ quantum entanglement or quantum mechanics in its processes. Explore the distinctions and applications of quantum entanglement in cryptographic methods to understand the future of secure communication.
Shor's algorithm
Post-quantum cryptography develops algorithms resistant to quantum attacks, particularly Shor's algorithm, which can efficiently factorize large integers threatening RSA and ECC security. Quantum key distribution utilizes quantum mechanics principles to secure communication channels, offering theoretically unbreakable key exchange immune to Shor's algorithm's computational power. Explore our detailed analysis comparing both approaches and their implications for future cryptographic security.
Source and External Links
Post-quantum cryptography - Wikipedia - Post-quantum cryptography encompasses cryptographic algorithms designed to resist attacks from quantum computers, focusing on six main approaches including lattice-based, multivariate, and symmetric-key cryptography.
Post-Quantum Cryptography | CSRC - Post-quantum cryptography aims to develop quantum-resistant cryptographic systems interoperable with current networks, with NIST actively working on standardizing such algorithms to secure information systems against future quantum threats.
Post-quantum cryptography (PQC) - Google Cloud - PQC delivers new cryptographic algorithms to withstand quantum computer attacks, with recent NIST standards guiding widespread adoption and industry efforts focused on protecting data long-term against emerging quantum risks.
 dowidth.com
dowidth.com