Zero Trust security architecture continuously verifies user identity and device integrity before granting access, minimizing security risks in dynamic IT environments. Single Sign-On (SSO) simplifies user authentication by enabling one set of credentials for multiple applications but may have vulnerabilities if compromised. Explore how integrating Zero Trust with SSO enhances cybersecurity frameworks.
Why it is important
Understanding the difference between zero trust and single sign-on is crucial for enhancing cybersecurity strategies and access management. Zero trust is a security model that assumes no user or device is trusted by default, requiring continuous verification, while single sign-on enables users to access multiple applications with one set of credentials. Implementing zero trust can significantly reduce the risk of data breaches by minimizing trust assumptions, whereas single sign-on improves user convenience and productivity but may create a single point of failure if compromised. Organizations must differentiate these concepts to balance security and usability effectively.
Comparison Table
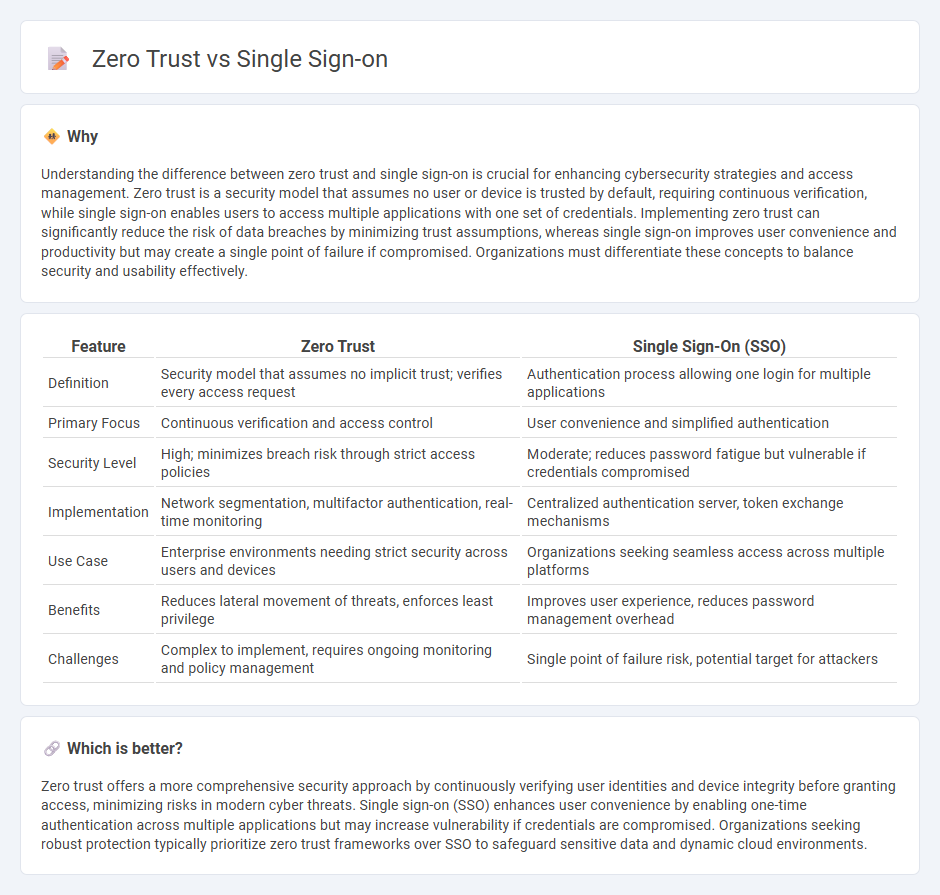
| Feature | Zero Trust | Single Sign-On (SSO) |
|---|---|---|
| Definition | Security model that assumes no implicit trust; verifies every access request | Authentication process allowing one login for multiple applications |
| Primary Focus | Continuous verification and access control | User convenience and simplified authentication |
| Security Level | High; minimizes breach risk through strict access policies | Moderate; reduces password fatigue but vulnerable if credentials compromised |
| Implementation | Network segmentation, multifactor authentication, real-time monitoring | Centralized authentication server, token exchange mechanisms |
| Use Case | Enterprise environments needing strict security across users and devices | Organizations seeking seamless access across multiple platforms |
| Benefits | Reduces lateral movement of threats, enforces least privilege | Improves user experience, reduces password management overhead |
| Challenges | Complex to implement, requires ongoing monitoring and policy management | Single point of failure risk, potential target for attackers |
Which is better?
Zero trust offers a more comprehensive security approach by continuously verifying user identities and device integrity before granting access, minimizing risks in modern cyber threats. Single sign-on (SSO) enhances user convenience by enabling one-time authentication across multiple applications but may increase vulnerability if credentials are compromised. Organizations seeking robust protection typically prioritize zero trust frameworks over SSO to safeguard sensitive data and dynamic cloud environments.
Connection
Zero Trust security models rely on continuous verification of user identity and device trustworthiness, which is effectively enhanced by Single Sign-On (SSO) solutions. SSO streamlines authentication processes by allowing users to access multiple applications with one set of credentials, reducing attack surfaces and minimizing phishing risks. Integrating SSO within Zero Trust frameworks ensures seamless, secure access management while enforcing strict access controls across diverse network environments.
Key Terms
Authentication
Single sign-on (SSO) enables users to access multiple applications with one set of credentials, simplifying authentication but potentially increasing risk if credentials are compromised. Zero Trust Authentication enforces strict verification for every access attempt, relying on continuous validation and least privilege principles to minimize breaches. Explore further to understand how these approaches balance convenience and security in modern authentication strategies.
Identity Management
Single Sign-On (SSO) streamlines Identity Management by allowing users to access multiple applications with a single set of credentials, improving user convenience and reducing password fatigue. In contrast, Zero Trust emphasizes continuous verification of identity and device posture, enforcing strict access controls regardless of the user's location or network. Explore how integrating SSO and Zero Trust can enhance security and user experience in modern Identity Management strategies.
Access Control
Single sign-on (SSO) streamlines user access by enabling one set of credentials for multiple applications, simplifying authentication but potentially increasing risk if compromised. Zero Trust Access Control enforces strict identity verification and least-privilege principles, continuously assessing trustworthiness regardless of network location to mitigate unauthorized access. Explore deeper into how Zero Trust transforms access management while complementing SSO strategies.
Source and External Links
Single sign-on (Wikipedia) - Single sign-on (SSO) is an authentication scheme that allows a user to log in to multiple independent software systems with just one set of credentials.
What Is Single Sign-On (SSO)? (IBM) - SSO simplifies authentication by letting a user log in once and then access all authorized applications during the same session.
What is SSO? (Cloudflare) - SSO combines several application login screens into one, requiring users to input their credentials only once to access all their services.
 dowidth.com
dowidth.com