Homomorphic encryption enables computation on encrypted data without decryption, preserving privacy while allowing data processing. Digital signatures ensure data integrity and authenticity by verifying the sender's identity and that the content has not been altered. Explore the differences and applications of homomorphic encryption and digital signatures to enhance your understanding of modern cryptographic technologies.
Why it is important
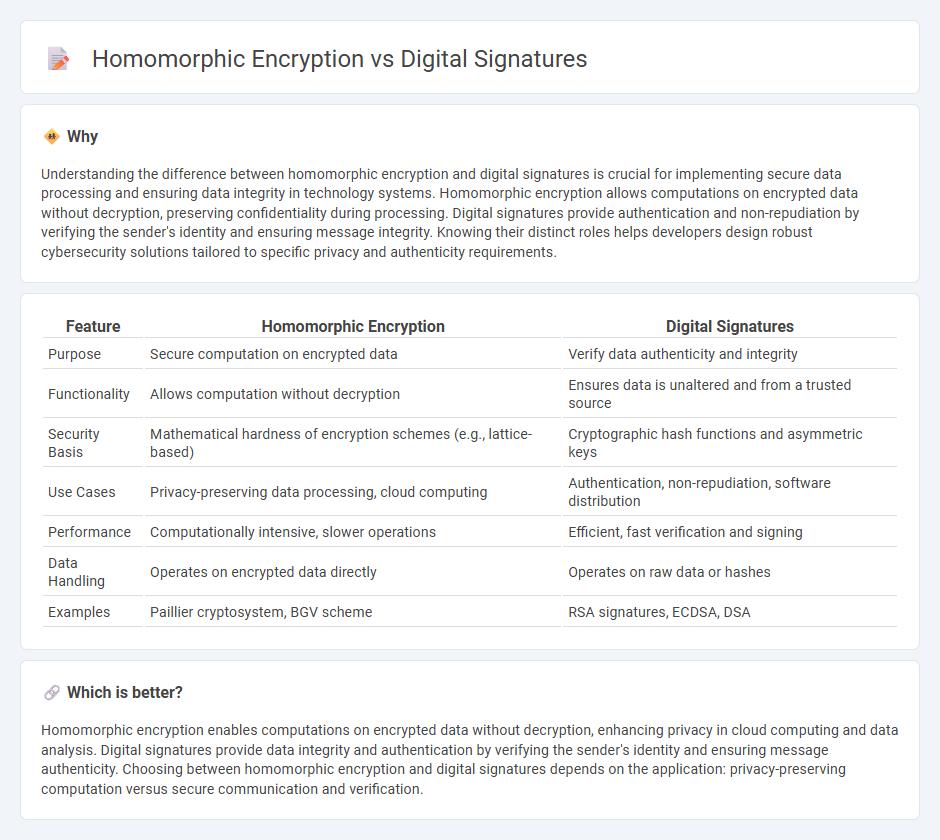
Understanding the difference between homomorphic encryption and digital signatures is crucial for implementing secure data processing and ensuring data integrity in technology systems. Homomorphic encryption allows computations on encrypted data without decryption, preserving confidentiality during processing. Digital signatures provide authentication and non-repudiation by verifying the sender's identity and ensuring message integrity. Knowing their distinct roles helps developers design robust cybersecurity solutions tailored to specific privacy and authenticity requirements.
Comparison Table
| Feature | Homomorphic Encryption | Digital Signatures |
|---|---|---|
| Purpose | Secure computation on encrypted data | Verify data authenticity and integrity |
| Functionality | Allows computation without decryption | Ensures data is unaltered and from a trusted source |
| Security Basis | Mathematical hardness of encryption schemes (e.g., lattice-based) | Cryptographic hash functions and asymmetric keys |
| Use Cases | Privacy-preserving data processing, cloud computing | Authentication, non-repudiation, software distribution |
| Performance | Computationally intensive, slower operations | Efficient, fast verification and signing |
| Data Handling | Operates on encrypted data directly | Operates on raw data or hashes |
| Examples | Paillier cryptosystem, BGV scheme | RSA signatures, ECDSA, DSA |
Which is better?
Homomorphic encryption enables computations on encrypted data without decryption, enhancing privacy in cloud computing and data analysis. Digital signatures provide data integrity and authentication by verifying the sender's identity and ensuring message authenticity. Choosing between homomorphic encryption and digital signatures depends on the application: privacy-preserving computation versus secure communication and verification.
Connection
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy and security in digital processes. Digital signatures verify the authenticity and integrity of messages or data, ensuring non-repudiation and trust in digital communications. Both technologies combine to enhance secure data handling in cryptographic protocols, allowing encrypted data to be signed and verified without exposing sensitive information.
Key Terms
Authentication
Digital signatures provide robust authentication by verifying the origin and integrity of a message through cryptographic algorithms like RSA or ECDSA, ensuring non-repudiation and trust in digital communications. Homomorphic encryption, while primarily designed for secure computations on encrypted data, comes with inherent challenges in authentication, often requiring supplementary protocols to validate user identity and data integrity. Explore the comparative strengths of digital signatures and homomorphic encryption to enhance your cybersecurity strategies.
Data Privacy
Digital signatures ensure data integrity and authentication by allowing recipients to verify the origin and unaltered state of a message, playing a critical role in secure communications. Homomorphic encryption enables computations on encrypted data without revealing the underlying information, preserving data privacy while facilitating secure data processing. Explore further to understand how these technologies complement each other in enhancing data privacy frameworks.
Computation on Encrypted Data
Digital signatures provide authentication and integrity verification but do not allow computation on encrypted data, as they only validate the data's origin and unchanged status. Homomorphic encryption enables direct computation on ciphertexts without decryption, preserving privacy and confidentiality while performing operations on encrypted data sets. Explore the detailed benefits and applications of homomorphic encryption in secure data processing to enhance your understanding.
Source and External Links
What is a Digital Signature? | Definition from TechTarget - A digital signature is a mathematical technique validating the authenticity and integrity of digital documents or messages using public key cryptography, ensuring secure verification and legal binding akin to handwritten signatures.
Understanding digital signatures | Docusign - Digital signatures employ Public Key Infrastructure (PKI) with a private-public key pair to create a unique encrypted signature for each signer, protecting document integrity and identity assurance through trusted certificate authorities.
Digital signature - Wikipedia - Digital signatures use asymmetric cryptography to verify the authenticity of digital messages and documents, offering non-repudiation and security stronger than handwritten signatures across applications like software distribution and financial transactions.
 dowidth.com
dowidth.com