Homomorphic encryption enables computations on encrypted data without revealing the underlying information, preserving privacy in cloud computing and data analysis. Secure multi-party computation allows multiple parties to jointly compute a function over their inputs while keeping those inputs private from each other. Explore the differences and applications of these advanced cryptographic techniques to enhance data security.
Why it is important
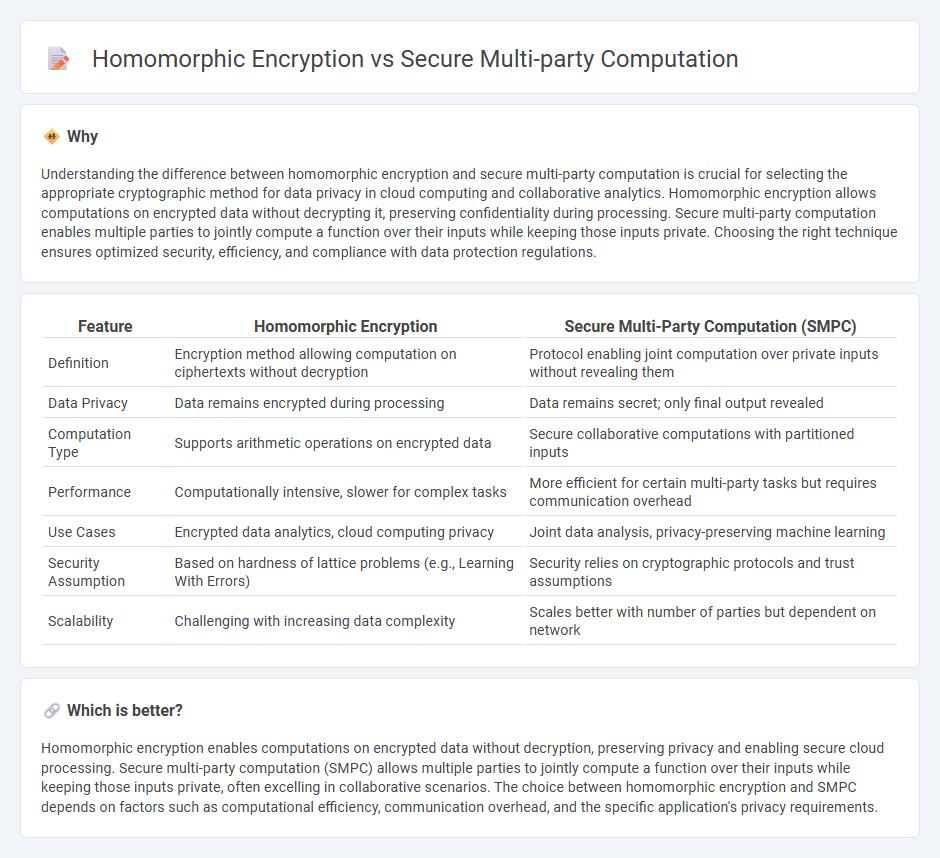
Understanding the difference between homomorphic encryption and secure multi-party computation is crucial for selecting the appropriate cryptographic method for data privacy in cloud computing and collaborative analytics. Homomorphic encryption allows computations on encrypted data without decrypting it, preserving confidentiality during processing. Secure multi-party computation enables multiple parties to jointly compute a function over their inputs while keeping those inputs private. Choosing the right technique ensures optimized security, efficiency, and compliance with data protection regulations.
Comparison Table
| Feature | Homomorphic Encryption | Secure Multi-Party Computation (SMPC) |
|---|---|---|
| Definition | Encryption method allowing computation on ciphertexts without decryption | Protocol enabling joint computation over private inputs without revealing them |
| Data Privacy | Data remains encrypted during processing | Data remains secret; only final output revealed |
| Computation Type | Supports arithmetic operations on encrypted data | Secure collaborative computations with partitioned inputs |
| Performance | Computationally intensive, slower for complex tasks | More efficient for certain multi-party tasks but requires communication overhead |
| Use Cases | Encrypted data analytics, cloud computing privacy | Joint data analysis, privacy-preserving machine learning |
| Security Assumption | Based on hardness of lattice problems (e.g., Learning With Errors) | Security relies on cryptographic protocols and trust assumptions |
| Scalability | Challenging with increasing data complexity | Scales better with number of parties but dependent on network |
Which is better?
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy and enabling secure cloud processing. Secure multi-party computation (SMPC) allows multiple parties to jointly compute a function over their inputs while keeping those inputs private, often excelling in collaborative scenarios. The choice between homomorphic encryption and SMPC depends on factors such as computational efficiency, communication overhead, and the specific application's privacy requirements.
Connection
Homomorphic encryption enables computations on encrypted data without revealing the underlying information, while secure multi-party computation allows multiple parties to jointly compute a function over their inputs without revealing them to each other. Both technologies enhance data privacy and security in distributed computing environments by ensuring sensitive data remains confidential during processing. Their combined application facilitates secure collaborative analysis and decision-making across untrusted parties.
Key Terms
Privacy-preserving computation
Secure multi-party computation (SMPC) enables multiple parties to jointly compute a function over their inputs while keeping those inputs private, ensuring data confidentiality in collaborative environments. Homomorphic encryption allows computations to be performed directly on encrypted data, preserving privacy without revealing the underlying plaintext during processing. Explore both techniques in detail to understand their distinct advantages and practical applications in privacy-preserving computation.
Cryptographic protocols
Secure multi-party computation (MPC) enables multiple parties to jointly compute a function over their inputs while keeping those inputs private, using protocols such as secret sharing and garbled circuits. Homomorphic encryption allows computations to be performed on ciphertexts, producing an encrypted result that, when decrypted, matches the output of operations on the plaintexts, with schemes including partially, somewhat, and fully homomorphic encryption. Explore the latest advancements and practical applications of cryptographic protocols in secure data processing to deepen your understanding.
Encrypted data processing
Secure multi-party computation (SMPC) enables multiple parties to jointly compute a function over their inputs while keeping those inputs private, ensuring encrypted data remains confidential throughout the process. Homomorphic encryption allows computations to be performed directly on encrypted data without decryption, preserving data security but often incurring higher computational overhead. Explore the advantages, use cases, and performance comparisons of SMPC and homomorphic encryption to understand their roles in encrypted data processing.
Source and External Links
What is Secure Multiparty Computation? - Secure Multiparty Computation (SMPC) is a cryptographic technique allowing multiple parties to jointly compute functions on private data without revealing the data itself, ensuring privacy, high accuracy, and quantum-safe security, albeit with computational overhead and communication costs.
Secure multi-party computation - SMPC is a cryptography subfield enabling parties to compute a function collaboratively while keeping their respective inputs private, protecting participants from each other rather than external adversaries.
Secure Multi-Party Computation - SMPC enhances data privacy by letting multiple parties perform accurate joint computations on private data, supporting regulatory compliance and secure cross-institution collaborations, and providing protection against quantum attacks.
 dowidth.com
dowidth.com