Quantum key distribution (QKD) leverages quantum mechanics to enable secure communication by generating cryptographic keys that are theoretically immune to eavesdropping, contrasting RSA encryption which relies on the computational difficulty of factoring large prime numbers. RSA encryption's security diminishes as quantum computing advances, while QKD offers future-proof protection through quantum principles like entanglement and no-cloning theorem. Explore the nuances of quantum key distribution versus RSA encryption to understand the evolution of secure digital communication.
Why it is important
Understanding the difference between quantum key distribution (QKD) and RSA encryption is crucial for advancing secure communication technologies. QKD leverages principles of quantum mechanics to enable theoretically unbreakable encryption by detecting eavesdropping, while RSA encryption relies on computational complexity that can be compromised by quantum computing. As quantum computers evolve, RSA's vulnerability increases, making QKD a vital technology for future-proof cybersecurity. This knowledge helps organizations prepare for emerging threats and adopt the most effective encryption methods.
Comparison Table
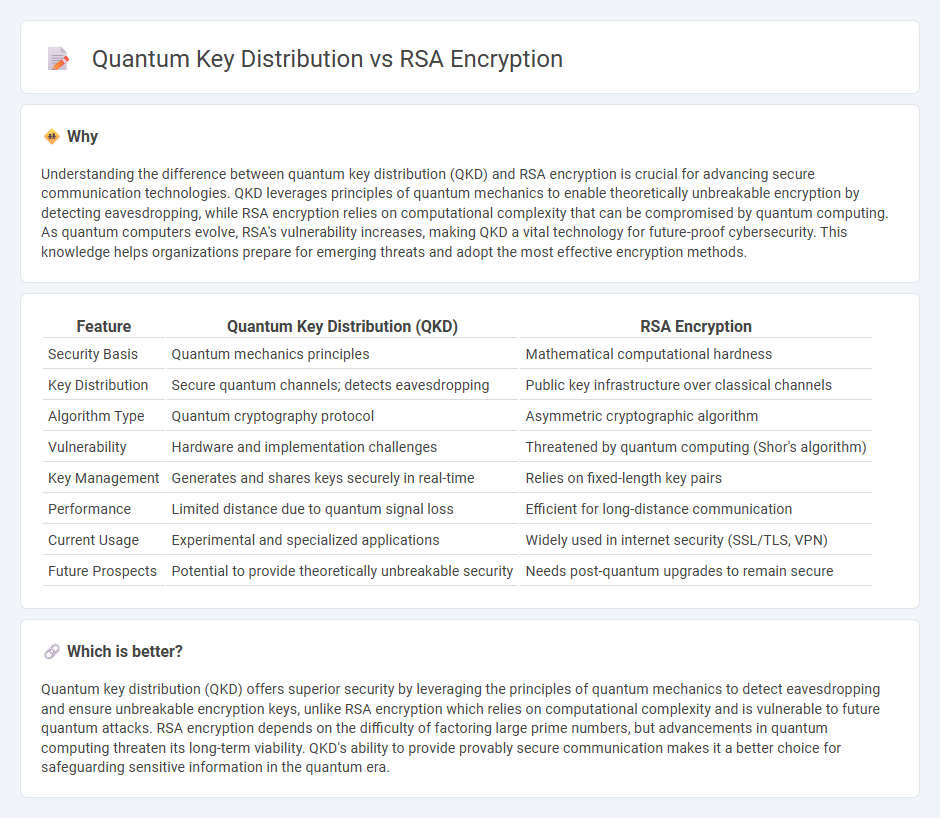
| Feature | Quantum Key Distribution (QKD) | RSA Encryption |
|---|---|---|
| Security Basis | Quantum mechanics principles | Mathematical computational hardness |
| Key Distribution | Secure quantum channels; detects eavesdropping | Public key infrastructure over classical channels |
| Algorithm Type | Quantum cryptography protocol | Asymmetric cryptographic algorithm |
| Vulnerability | Hardware and implementation challenges | Threatened by quantum computing (Shor's algorithm) |
| Key Management | Generates and shares keys securely in real-time | Relies on fixed-length key pairs |
| Performance | Limited distance due to quantum signal loss | Efficient for long-distance communication |
| Current Usage | Experimental and specialized applications | Widely used in internet security (SSL/TLS, VPN) |
| Future Prospects | Potential to provide theoretically unbreakable security | Needs post-quantum upgrades to remain secure |
Which is better?
Quantum key distribution (QKD) offers superior security by leveraging the principles of quantum mechanics to detect eavesdropping and ensure unbreakable encryption keys, unlike RSA encryption which relies on computational complexity and is vulnerable to future quantum attacks. RSA encryption depends on the difficulty of factoring large prime numbers, but advancements in quantum computing threaten its long-term viability. QKD's ability to provide provably secure communication makes it a better choice for safeguarding sensitive information in the quantum era.
Connection
Quantum key distribution (QKD) provides a secure method for sharing encryption keys by exploiting quantum mechanics principles, ensuring that any eavesdropping attempts are detectable. RSA encryption relies on the computational difficulty of factoring large prime numbers, but it is vulnerable to quantum attacks, specifically from quantum algorithms like Shor's algorithm. Integrating QKD with classical RSA encryption protocols aims to enhance cryptographic security by combining quantum-generated secure keys with established RSA frameworks, safeguarding data against future quantum threats.
Key Terms
Public-key cryptography
RSA encryption, a cornerstone of public-key cryptography, relies on the computational difficulty of factoring large prime numbers to secure data, whereas quantum key distribution (QKD) uses the principles of quantum mechanics to enable provably secure key exchange that is resistant to quantum attacks. RSA's security is threatened by advancements in quantum computing, particularly Shor's algorithm, which could efficiently break RSA keys, driving interest toward QKD as a future-proof alternative. Explore more about how quantum key distribution could revolutionize the future of secure communications beyond traditional public-key cryptography.
Quantum entanglement
RSA encryption relies on the computational difficulty of factoring large prime numbers, while quantum key distribution (QKD) leverages quantum entanglement to ensure secure communication by detecting eavesdropping through the disturbance of entangled photon states. Quantum entanglement enables QKD protocols like BB84 and E91 to generate shared, secret keys with provable security based on the laws of quantum mechanics, rendering classical attacks ineffective. Explore the critical role of quantum entanglement in revolutionizing secure communication by learning more about QKD advancements.
Shor's algorithm
RSA encryption relies on the computational difficulty of factoring large integers, a task rendered vulnerable by Shor's algorithm, which efficiently breaks RSA using quantum computing. Quantum key distribution (QKD) offers a quantum-safe alternative by enabling secure communication through the principles of quantum mechanics rather than computational complexity, making it resistant to attacks by quantum algorithms like Shor's. Explore further to understand how these cryptographic approaches impact the future of secure communications.
Source and External Links
RSA Algorithm in Cryptography - GeeksforGeeks - RSA is an asymmetric encryption algorithm using a public key for encryption and a private key for decryption, based on factorization of large numbers and modular arithmetic with key steps including key generation, encryption, and decryption.
What is the RSA algorithm? | Definition from TechTarget - RSA is a widely used public key cryptosystem that secures communications by using paired keys (public/private) that are mathematically linked, enabling encryption, decryption, digital signatures, and authentication over insecure networks.
RSA cryptosystem - Wikipedia - RSA relies on the computational difficulty of factoring large numbers, with key components n and e as the public key and d as the private key, enabling encryption and decryption through modular exponentiation and supporting message signing and verification.
 dowidth.com
dowidth.com