Post-quantum cryptography focuses on developing encryption algorithms resistant to attacks by quantum computers, ensuring data security in the quantum era. Hybrid cryptographic systems combine traditional and post-quantum algorithms to provide a transitional layer of security against both classical and quantum threats. Explore the differences and advantages of these approaches to secure your data in the future.
Why it is important
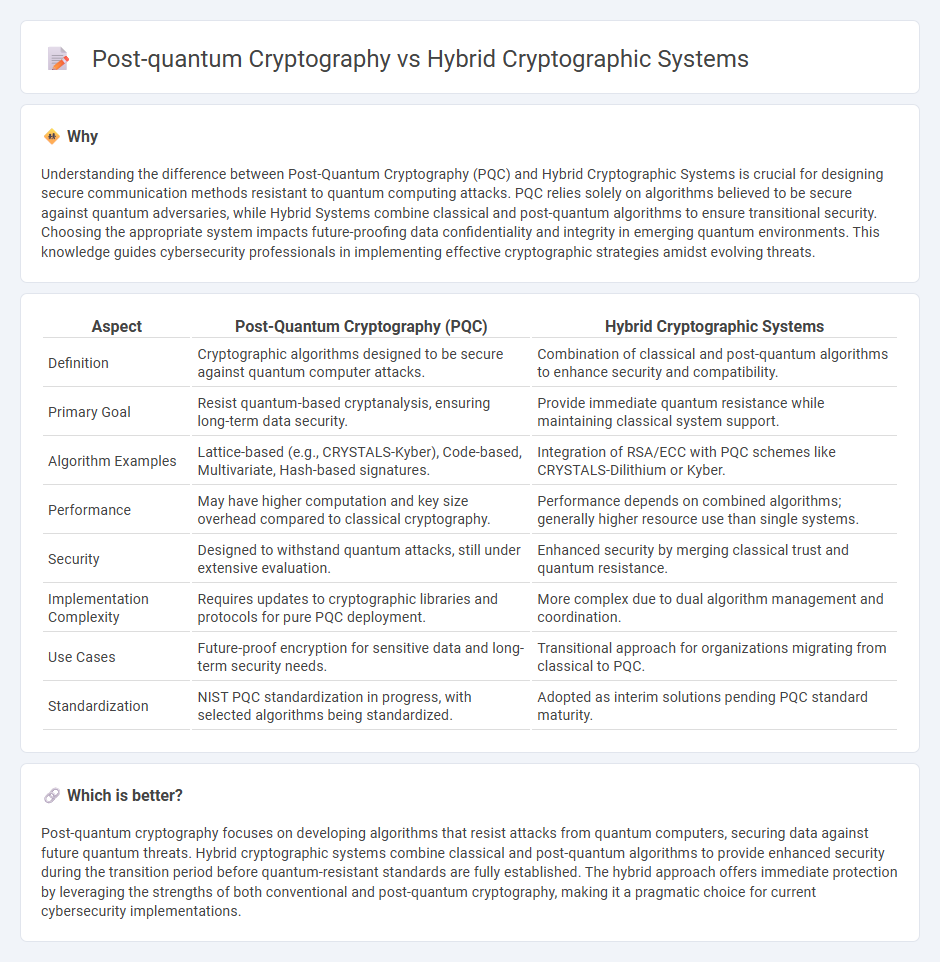
Understanding the difference between Post-Quantum Cryptography (PQC) and Hybrid Cryptographic Systems is crucial for designing secure communication methods resistant to quantum computing attacks. PQC relies solely on algorithms believed to be secure against quantum adversaries, while Hybrid Systems combine classical and post-quantum algorithms to ensure transitional security. Choosing the appropriate system impacts future-proofing data confidentiality and integrity in emerging quantum environments. This knowledge guides cybersecurity professionals in implementing effective cryptographic strategies amidst evolving threats.
Comparison Table
| Aspect | Post-Quantum Cryptography (PQC) | Hybrid Cryptographic Systems |
|---|---|---|
| Definition | Cryptographic algorithms designed to be secure against quantum computer attacks. | Combination of classical and post-quantum algorithms to enhance security and compatibility. |
| Primary Goal | Resist quantum-based cryptanalysis, ensuring long-term data security. | Provide immediate quantum resistance while maintaining classical system support. |
| Algorithm Examples | Lattice-based (e.g., CRYSTALS-Kyber), Code-based, Multivariate, Hash-based signatures. | Integration of RSA/ECC with PQC schemes like CRYSTALS-Dilithium or Kyber. |
| Performance | May have higher computation and key size overhead compared to classical cryptography. | Performance depends on combined algorithms; generally higher resource use than single systems. |
| Security | Designed to withstand quantum attacks, still under extensive evaluation. | Enhanced security by merging classical trust and quantum resistance. |
| Implementation Complexity | Requires updates to cryptographic libraries and protocols for pure PQC deployment. | More complex due to dual algorithm management and coordination. |
| Use Cases | Future-proof encryption for sensitive data and long-term security needs. | Transitional approach for organizations migrating from classical to PQC. |
| Standardization | NIST PQC standardization in progress, with selected algorithms being standardized. | Adopted as interim solutions pending PQC standard maturity. |
Which is better?
Post-quantum cryptography focuses on developing algorithms that resist attacks from quantum computers, securing data against future quantum threats. Hybrid cryptographic systems combine classical and post-quantum algorithms to provide enhanced security during the transition period before quantum-resistant standards are fully established. The hybrid approach offers immediate protection by leveraging the strengths of both conventional and post-quantum cryptography, making it a pragmatic choice for current cybersecurity implementations.
Connection
Post-quantum cryptography focuses on developing encryption algorithms resistant to attacks by quantum computers, addressing vulnerabilities in classical cryptographic systems. Hybrid cryptographic systems integrate both classical and post-quantum algorithms to ensure security during the transition to quantum-resistant encryption. This combination provides robust protection by leveraging the strengths of established cryptography alongside emerging quantum-safe techniques.
Key Terms
Symmetric-Asymmetric Integration
Hybrid cryptographic systems combine symmetric and asymmetric encryption algorithms to enhance security and performance by leveraging the speed of symmetric ciphers and the key distribution strengths of asymmetric schemes. Post-quantum cryptography focuses on developing algorithms resistant to quantum attacks, often integrating with symmetric methods to maintain data integrity while addressing quantum vulnerabilities. Explore the evolving landscape of cryptographic integration to understand how hybrid approaches adapt to quantum threats and secure future communications.
Quantum-Resistant Algorithms
Hybrid cryptographic systems combine classical encryption techniques with quantum-resistant algorithms, ensuring security against both current and future quantum threats. Quantum-resistant algorithms such as lattice-based, hash-based, and code-based cryptography provide robust defenses against quantum computing attacks, making them essential components of post-quantum cryptographic strategies. Explore detailed comparisons of hybrid versus purely post-quantum approaches to understand the future landscape of secure communication.
Key Exchange Mechanisms
Hybrid cryptographic systems combine traditional public key algorithms like RSA or ECC with post-quantum algorithms such as lattice-based or code-based schemes to enhance security during key exchange processes. These systems ensure quantum resistance while maintaining compatibility with existing infrastructure, addressing vulnerabilities posed by quantum computing advancements. Explore the evolving landscape of key exchange mechanisms to secure communication in the quantum era.
Source and External Links
Hybrid Cryptosystem - In cryptography, a hybrid cryptosystem combines the efficiency of symmetric-key encryption with the security advantages of public-key encryption, enhancing both data encryption and key exchange.
What Is A Hybrid Cryptosystem? - This resource explains how hybrid cryptosystems work by leveraging symmetric encryption for data speed and asymmetric encryption for secure key exchange.
Hybrid Encryption | Tink - The Hybrid Encryption primitive in Tink combines symmetric and asymmetric encryption to provide efficient and secure data encryption methods.
 dowidth.com
dowidth.com