Zero Trust Architecture (ZTA) fundamentally redefines cybersecurity by assuming no implicit trust and continuously verifying every access request across the network, while Multifactor Authentication (MFA) enhances security by requiring users to provide multiple forms of identity verification before granting access. ZTA integrates various security measures, including MFA, to create a comprehensive framework that minimizes risk and limits potential breaches. Explore how these critical technologies reshape organizational security strategies and protect digital assets.
Why it is important
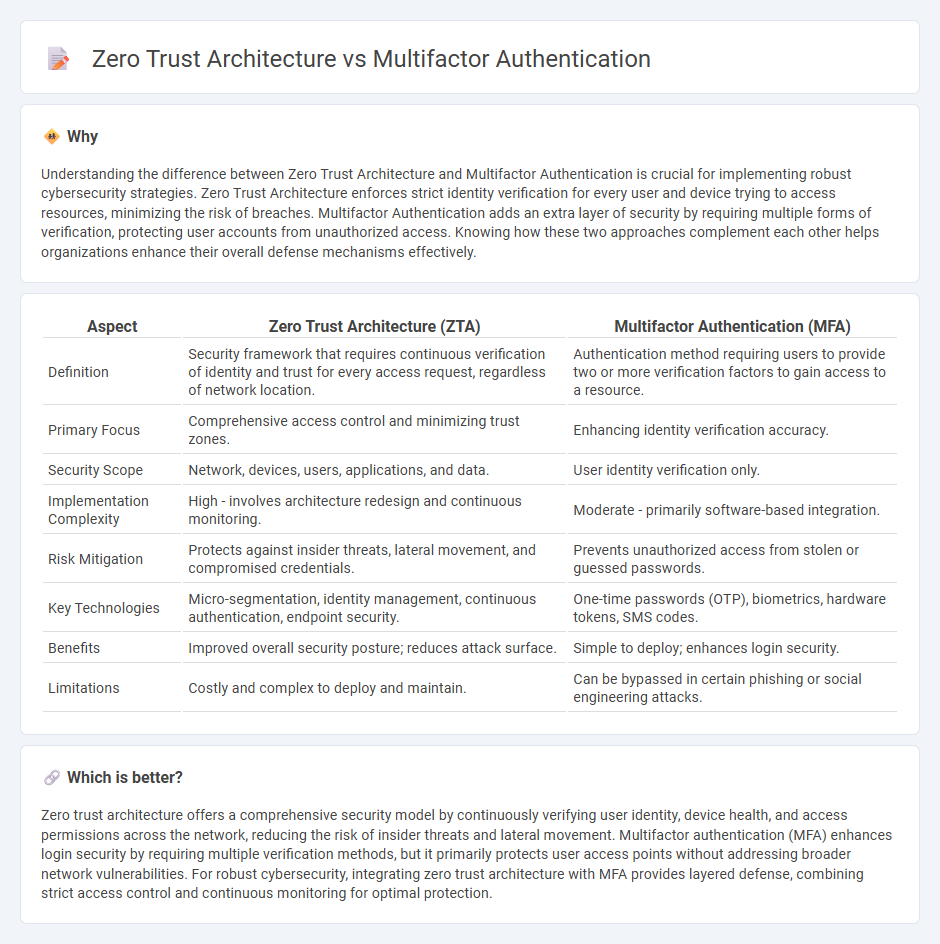
Understanding the difference between Zero Trust Architecture and Multifactor Authentication is crucial for implementing robust cybersecurity strategies. Zero Trust Architecture enforces strict identity verification for every user and device trying to access resources, minimizing the risk of breaches. Multifactor Authentication adds an extra layer of security by requiring multiple forms of verification, protecting user accounts from unauthorized access. Knowing how these two approaches complement each other helps organizations enhance their overall defense mechanisms effectively.
Comparison Table
| Aspect | Zero Trust Architecture (ZTA) | Multifactor Authentication (MFA) |
|---|---|---|
| Definition | Security framework that requires continuous verification of identity and trust for every access request, regardless of network location. | Authentication method requiring users to provide two or more verification factors to gain access to a resource. |
| Primary Focus | Comprehensive access control and minimizing trust zones. | Enhancing identity verification accuracy. |
| Security Scope | Network, devices, users, applications, and data. | User identity verification only. |
| Implementation Complexity | High - involves architecture redesign and continuous monitoring. | Moderate - primarily software-based integration. |
| Risk Mitigation | Protects against insider threats, lateral movement, and compromised credentials. | Prevents unauthorized access from stolen or guessed passwords. |
| Key Technologies | Micro-segmentation, identity management, continuous authentication, endpoint security. | One-time passwords (OTP), biometrics, hardware tokens, SMS codes. |
| Benefits | Improved overall security posture; reduces attack surface. | Simple to deploy; enhances login security. |
| Limitations | Costly and complex to deploy and maintain. | Can be bypassed in certain phishing or social engineering attacks. |
Which is better?
Zero trust architecture offers a comprehensive security model by continuously verifying user identity, device health, and access permissions across the network, reducing the risk of insider threats and lateral movement. Multifactor authentication (MFA) enhances login security by requiring multiple verification methods, but it primarily protects user access points without addressing broader network vulnerabilities. For robust cybersecurity, integrating zero trust architecture with MFA provides layered defense, combining strict access control and continuous monitoring for optimal protection.
Connection
Zero Trust Architecture relies on continuous verification of user identities and device integrity, making Multifactor Authentication (MFA) a crucial component for enforcing strict access controls. MFA enhances security by requiring multiple forms of verification, reducing the risk of unauthorized access even if credentials are compromised. Implementing MFA within Zero Trust frameworks strengthens protection against cyber threats by ensuring that access permissions are dynamically assessed based on robust identity proofing.
Key Terms
Authentication Factors
Multifactor authentication (MFA) requires users to provide two or more verification factors, such as passwords, biometrics, or hardware tokens, to enhance login security and reduce unauthorized access. Zero Trust Architecture (ZTA) integrates MFA as a critical component but focuses on continuous verification of user identity, device health, and network context, ensuring strict access controls regardless of location. Explore further to understand how MFA fits within the broader Zero Trust framework and elevates organizational security.
Least Privilege
Multifactor authentication (MFA) strengthens security by requiring multiple forms of verification, reducing the risk of unauthorized access, while Zero Trust Architecture (ZTA) enforces the principle of Least Privilege by continuously validating user permissions and limiting access to only what is necessary. ZTA integrates dynamic access controls and micro-segmentation to minimize insider threats and lateral movement within networks, going beyond MFA's static authentication layer. Explore how combining MFA and Zero Trust strategies enhances organizational security by strictly enforcing Least Privilege and adaptive access policies.
Continuous Verification
Multifactor authentication (MFA) enhances security by requiring multiple forms of verification, such as biometrics and passwords, to authenticate user identities, reducing the risk of unauthorized access. Zero Trust Architecture (ZTA) employs continuous verification by constantly validating user access based on real-time context, device health, and behavioral analytics, ensuring that no entity is implicitly trusted at any point. Explore how combining MFA with Zero Trust principles strengthens enterprise security frameworks and mitigates evolving cyber threats.
Source and External Links
What is Multifactor Authentication (MFA)? | Definition from TechTarget - Multifactor authentication (MFA) is an IT security technology requiring two or more independent authentication factors--what you know, have, or are--to verify user identity and provide layered defense against unauthorized access and cyberattacks.
What is Multi-Factor Authentication (MFA)? - OneLogin - MFA requires users to present multiple verification factors, such as passwords plus one-time codes or biometrics, significantly enhancing security beyond password-only logins to prevent unauthorized access.
What is Multi-Factor Authentication (MFA) and How does it Work? - RSA - MFA improves security by confirming identity through more than one method, for example combining a password with a one-time password (OTP), thus reducing the risk of unauthorized access to applications or data.
 dowidth.com
dowidth.com