Homomorphic encryption allows computations on encrypted data without revealing the underlying information, enabling secure data processing in cloud computing and privacy-preserving applications. Oblivious transfer is a cryptographic protocol that ensures a sender transmits one of many possible pieces of information without knowing which piece was received, enhancing privacy in secure multiparty computations. Explore the differences and use cases of these advanced cryptographic techniques to understand their impact on secure communication.
Why it is important
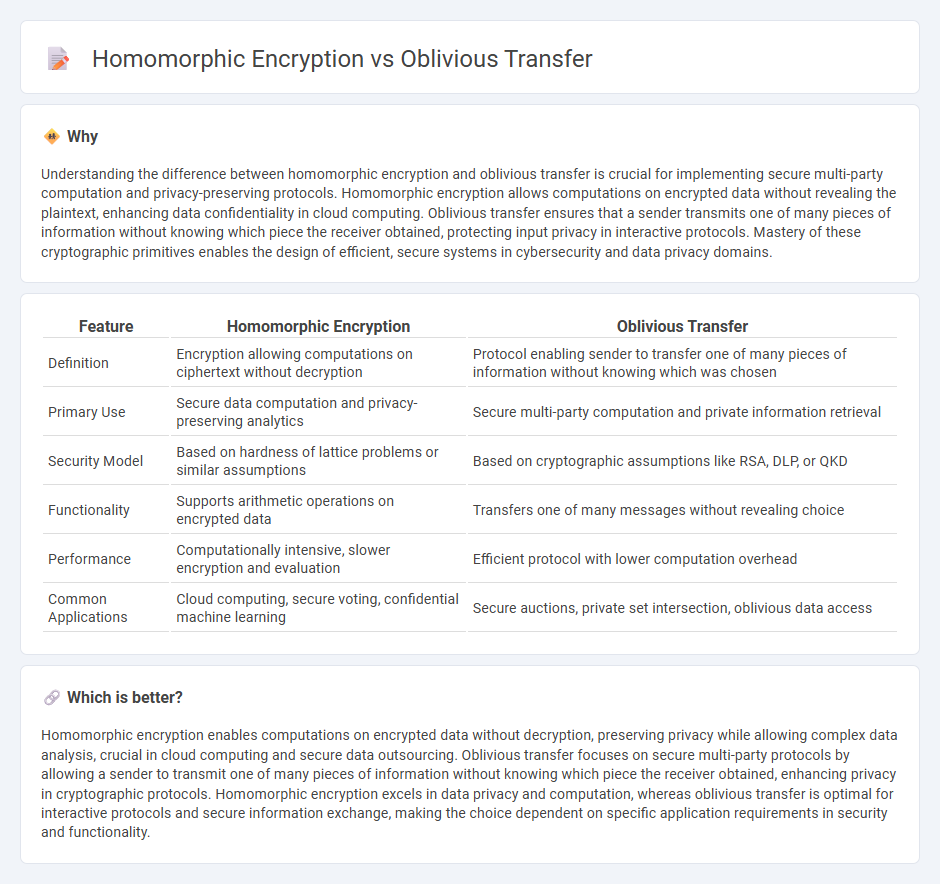
Understanding the difference between homomorphic encryption and oblivious transfer is crucial for implementing secure multi-party computation and privacy-preserving protocols. Homomorphic encryption allows computations on encrypted data without revealing the plaintext, enhancing data confidentiality in cloud computing. Oblivious transfer ensures that a sender transmits one of many pieces of information without knowing which piece the receiver obtained, protecting input privacy in interactive protocols. Mastery of these cryptographic primitives enables the design of efficient, secure systems in cybersecurity and data privacy domains.
Comparison Table
| Feature | Homomorphic Encryption | Oblivious Transfer |
|---|---|---|
| Definition | Encryption allowing computations on ciphertext without decryption | Protocol enabling sender to transfer one of many pieces of information without knowing which was chosen |
| Primary Use | Secure data computation and privacy-preserving analytics | Secure multi-party computation and private information retrieval |
| Security Model | Based on hardness of lattice problems or similar assumptions | Based on cryptographic assumptions like RSA, DLP, or QKD |
| Functionality | Supports arithmetic operations on encrypted data | Transfers one of many messages without revealing choice |
| Performance | Computationally intensive, slower encryption and evaluation | Efficient protocol with lower computation overhead |
| Common Applications | Cloud computing, secure voting, confidential machine learning | Secure auctions, private set intersection, oblivious data access |
Which is better?
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy while allowing complex data analysis, crucial in cloud computing and secure data outsourcing. Oblivious transfer focuses on secure multi-party protocols by allowing a sender to transmit one of many pieces of information without knowing which piece the receiver obtained, enhancing privacy in cryptographic protocols. Homomorphic encryption excels in data privacy and computation, whereas oblivious transfer is optimal for interactive protocols and secure information exchange, making the choice dependent on specific application requirements in security and functionality.
Connection
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy throughout processing. Oblivious transfer is a cryptographic protocol that allows a sender to transmit one of many pieces of information without knowing which piece the receiver obtained. These technologies are connected in secure multiparty computation, where homomorphic encryption processes encrypted inputs while oblivious transfer facilitates private data exchange, ensuring data confidentiality and integrity.
Key Terms
Data Privacy
Oblivious transfer enables secure data exchange where a sender transmits one of many pieces of information without knowing which piece the receiver obtains, ensuring strong privacy in multi-party computations. Homomorphic encryption allows computations on encrypted data without revealing the inputs, preserving confidentiality throughout the process and enabling privacy-preserving data analytics. Discover how these advanced cryptographic techniques revolutionize data privacy by exploring their unique use cases and security advantages.
Secure Computation
Oblivious transfer enables secure computation by allowing one party to send multiple pieces of data while the receiver selects one piece without revealing their choice, ensuring privacy in communication protocols. Homomorphic encryption allows computations on encrypted data without decryption, preserving data confidentiality in secure multiparty computations. Explore detailed comparisons and use cases to understand how these cryptographic techniques enhance secure computation.
Cryptographic Protocols
Oblivious transfer is a fundamental cryptographic protocol enabling secure data exchange where a sender transmits one of many pieces of information without knowing which piece was chosen, ensuring privacy and data minimization. Homomorphic encryption allows computations to be performed directly on encrypted data without decryption, preserving confidentiality throughout the process and enabling secure multiparty computation. Explore the detailed mechanisms and use cases of these protocols to enhance secure communication and data privacy strategies.
Source and External Links
Oblivious transfer - Wikipedia - Oblivious transfer (OT) is a cryptographic protocol where a sender transfers one of many pieces of information to a receiver but remains oblivious as to which piece was transferred; it was first introduced by Rabin in 1981 and later generalized to forms like 1-out-of-2 OT, fundamental in secure multiparty computation.
Oblivious Transfer - University of Illinois Urbana-Champaign - Oblivious transfer is a primitive cryptographic protocol where the sender has multiple messages and the receiver obtains exactly one based on a choice bit, with the sender remaining unaware of which was chosen, securing both parties' privacy without a trusted authority.
Lecture 10 1 Oblivious Transfer - UCLA - Rabin's oblivious transfer models a probabilistic transfer where the sender sends a bit that the receiver receives with probability 1/2 without the sender knowing if the bit was received, while the 1-out-of-2 oblivious transfer allows a receiver to get exactly one bit from a pair without the sender knowing which one.
 dowidth.com
dowidth.com