Post-quantum cryptography focuses on developing encryption algorithms resistant to quantum computer attacks, ensuring data security in the future quantum era. Zero-knowledge proofs allow one party to prove knowledge of information to another without revealing the information itself, enhancing privacy and authentication in blockchain and cryptographic systems. Explore the benefits and applications of post-quantum cryptography and zero-knowledge proofs to understand the future of secure digital communication.
Why it is important
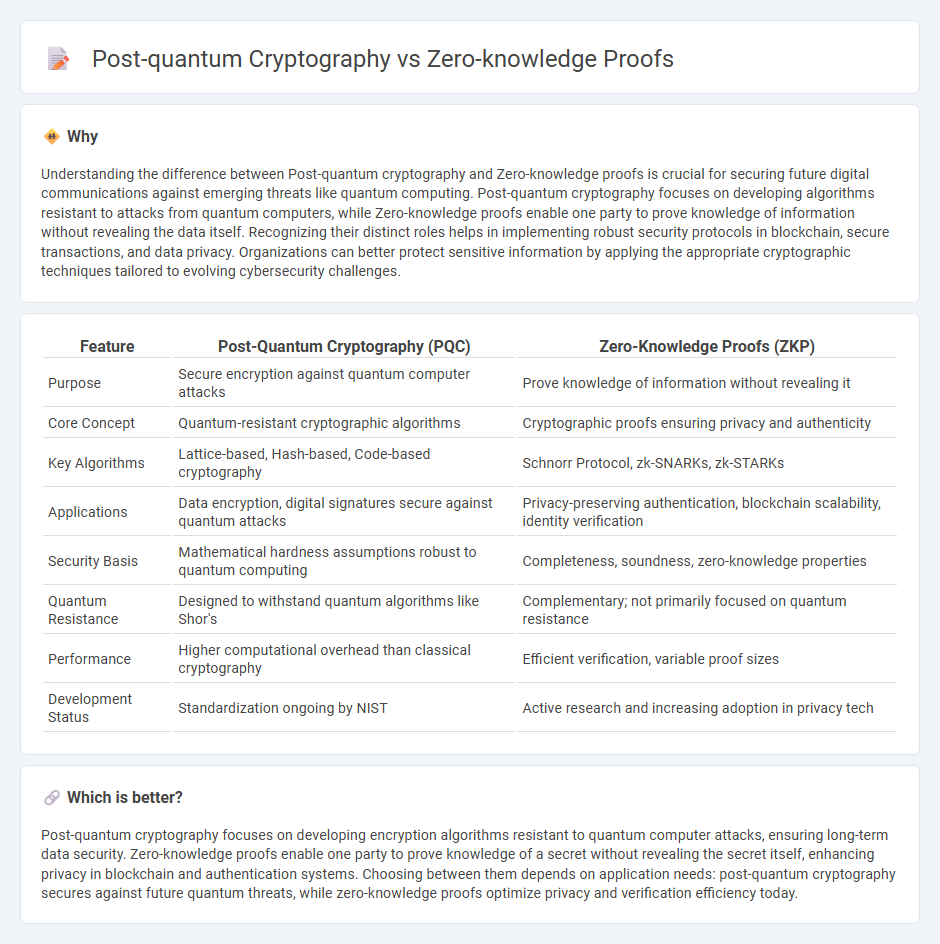
Understanding the difference between Post-quantum cryptography and Zero-knowledge proofs is crucial for securing future digital communications against emerging threats like quantum computing. Post-quantum cryptography focuses on developing algorithms resistant to attacks from quantum computers, while Zero-knowledge proofs enable one party to prove knowledge of information without revealing the data itself. Recognizing their distinct roles helps in implementing robust security protocols in blockchain, secure transactions, and data privacy. Organizations can better protect sensitive information by applying the appropriate cryptographic techniques tailored to evolving cybersecurity challenges.
Comparison Table
| Feature | Post-Quantum Cryptography (PQC) | Zero-Knowledge Proofs (ZKP) |
|---|---|---|
| Purpose | Secure encryption against quantum computer attacks | Prove knowledge of information without revealing it |
| Core Concept | Quantum-resistant cryptographic algorithms | Cryptographic proofs ensuring privacy and authenticity |
| Key Algorithms | Lattice-based, Hash-based, Code-based cryptography | Schnorr Protocol, zk-SNARKs, zk-STARKs |
| Applications | Data encryption, digital signatures secure against quantum attacks | Privacy-preserving authentication, blockchain scalability, identity verification |
| Security Basis | Mathematical hardness assumptions robust to quantum computing | Completeness, soundness, zero-knowledge properties |
| Quantum Resistance | Designed to withstand quantum algorithms like Shor's | Complementary; not primarily focused on quantum resistance |
| Performance | Higher computational overhead than classical cryptography | Efficient verification, variable proof sizes |
| Development Status | Standardization ongoing by NIST | Active research and increasing adoption in privacy tech |
Which is better?
Post-quantum cryptography focuses on developing encryption algorithms resistant to quantum computer attacks, ensuring long-term data security. Zero-knowledge proofs enable one party to prove knowledge of a secret without revealing the secret itself, enhancing privacy in blockchain and authentication systems. Choosing between them depends on application needs: post-quantum cryptography secures against future quantum threats, while zero-knowledge proofs optimize privacy and verification efficiency today.
Connection
Post-quantum cryptography and zero-knowledge proofs converge in enhancing cybersecurity against quantum computing threats by enabling secure verification processes without revealing sensitive information. Post-quantum algorithms provide cryptographic schemes resistant to quantum attacks, while zero-knowledge proofs allow one party to prove knowledge of a secret without exposing it, preserving privacy in quantum-safe protocols. This synergy strengthens secure communications, authentication, and blockchain systems in the emerging quantum era.
Key Terms
Computational hardness assumptions
Zero-knowledge proofs rely on computational hardness assumptions, such as the difficulty of discrete logarithms or factoring, to ensure that no knowledge beyond the validity of a statement is revealed, maintaining privacy in cryptographic protocols. Post-quantum cryptography aims to develop algorithms resistant to quantum attacks by leveraging problems believed to be hard for quantum computers, like lattice-based, code-based, or multivariate polynomial problems, which differ fundamentally from classical hardness assumptions. Explore deeper insights into the evolving landscape of computational hardness and its implications for secure cryptographic systems in the quantum era.
Lattice-based cryptography
Zero-knowledge proofs enable verification of information without revealing the data itself, offering privacy-preserving solutions crucial for secure transactions and authentication. Lattice-based cryptography underpins many post-quantum cryptographic schemes, providing resistance to quantum attacks through hard mathematical problems like shortest vector problem (SVP) and learning with errors (LWE). Explore how combining zero-knowledge proofs with lattice-based techniques enhances security frameworks in the quantum computing era.
Interactive protocols
Zero-knowledge proofs (ZKPs) enable one party to prove knowledge of a secret without revealing it, ensuring privacy in interactive protocols, while post-quantum cryptography (PQC) offers algorithms resistant to quantum attacks, safeguarding long-term data integrity. Interactive ZKPs rely on challenges and responses that maintain witness confidentiality, whereas PQC protocols primarily adapt or replace classical cryptographic primitives affected by quantum computers. Explore the advancements integrating zero-knowledge proofs with post-quantum resistant interactive protocols to strengthen future-proof security solutions.
Source and External Links
Zero-knowledge proof - Wikipedia - A zero-knowledge proof is a protocol where one party convinces another that a statement is true without revealing any additional information, illustrated by examples like "Where's Wally?" where the prover demonstrates knowledge without disclosing the location details.
Zero-Knowledge Proof (ZKP) -- Explained - Chainlink - Zero-knowledge proofs allow a prover to convince a verifier a statement about data is true without revealing the data itself, defined by completeness, soundness, and zero-knowledge properties, exemplified by a cave passphrase analogy showing knowledge without disclosure.
Zero-knowledge proofs explained in 3 examples - Circularise - Zero-knowledge proofs enable proving the validity of a statement without revealing anything beyond its truth, with intuitive analogies like the "Where's Wally?" example where knowledge is shown without location disclosure.
 dowidth.com
dowidth.com