Quantum key distribution (QKD) leverages principles of quantum mechanics to enable ultra-secure communication by detecting eavesdropping through the behavior of quantum particles. Diffie-Hellman key exchange, a classical cryptographic method, allows two parties to securely generate a shared secret over an insecure channel using discrete logarithms. Explore the detailed differences and security implications between these two key exchange techniques for a deeper understanding.
Why it is important
Understanding the difference between quantum key distribution (QKD) and Diffie-Hellman key exchange is crucial for securing communication in the age of quantum computing, as QKD leverages quantum mechanics to provide theoretically unbreakable encryption. Diffie-Hellman, a classical cryptographic method, relies on the computational difficulty of discrete logarithms, which quantum algorithms like Shor's algorithm can easily solve, rendering it vulnerable. Knowledge of these distinctions enables cybersecurity professionals to adopt future-proof encryption methods that safeguard sensitive data against emerging quantum threats. Mastery of QKD principles supports the development of secure quantum communication networks essential for protecting critical infrastructure.
Comparison Table
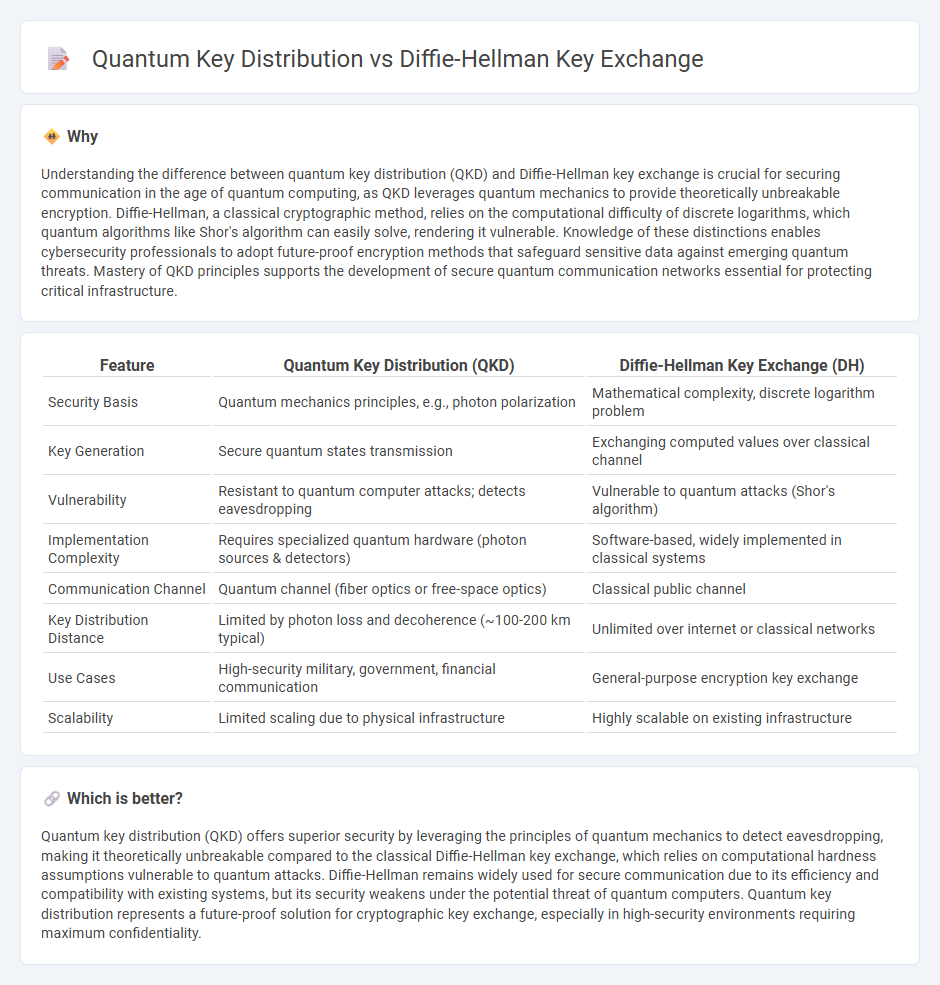
| Feature | Quantum Key Distribution (QKD) | Diffie-Hellman Key Exchange (DH) |
|---|---|---|
| Security Basis | Quantum mechanics principles, e.g., photon polarization | Mathematical complexity, discrete logarithm problem |
| Key Generation | Secure quantum states transmission | Exchanging computed values over classical channel |
| Vulnerability | Resistant to quantum computer attacks; detects eavesdropping | Vulnerable to quantum attacks (Shor's algorithm) |
| Implementation Complexity | Requires specialized quantum hardware (photon sources & detectors) | Software-based, widely implemented in classical systems |
| Communication Channel | Quantum channel (fiber optics or free-space optics) | Classical public channel |
| Key Distribution Distance | Limited by photon loss and decoherence (~100-200 km typical) | Unlimited over internet or classical networks |
| Use Cases | High-security military, government, financial communication | General-purpose encryption key exchange |
| Scalability | Limited scaling due to physical infrastructure | Highly scalable on existing infrastructure |
Which is better?
Quantum key distribution (QKD) offers superior security by leveraging the principles of quantum mechanics to detect eavesdropping, making it theoretically unbreakable compared to the classical Diffie-Hellman key exchange, which relies on computational hardness assumptions vulnerable to quantum attacks. Diffie-Hellman remains widely used for secure communication due to its efficiency and compatibility with existing systems, but its security weakens under the potential threat of quantum computers. Quantum key distribution represents a future-proof solution for cryptographic key exchange, especially in high-security environments requiring maximum confidentiality.
Connection
Quantum key distribution (QKD) and Diffie-Hellman key exchange both enable secure cryptographic key exchange but operate on fundamentally different principles. QKD leverages quantum mechanics to detect eavesdropping and ensure secure key generation, while Diffie-Hellman relies on mathematical hardness assumptions in classical computing environments. Integration of QKD with traditional protocols like Diffie-Hellman enhances overall communication security, addressing potential vulnerabilities in classical key exchange methods.
Key Terms
Public Key Exchange (Diffie-Hellman)
Diffie-Hellman key exchange enables secure public key exchange through mathematical problems like discrete logarithms, providing confidentiality over insecure channels but remains vulnerable to quantum attacks from algorithms such as Shor's. Unlike quantum key distribution which leverages quantum mechanics to detect eavesdropping, Diffie-Hellman relies on classical cryptographic assumptions that quantum computing threatens to break. Explore the fundamental differences and security implications between these key exchange mechanisms to deepen your understanding.
Quantum Entanglement (Quantum Key Distribution)
Diffie-Hellman key exchange relies on computational hardness assumptions for secure key generation, making it vulnerable to quantum attacks, whereas Quantum Key Distribution (QKD) uses quantum entanglement to ensure unconditional security through the laws of quantum mechanics. Quantum entanglement in QKD enables the detection of eavesdropping by observing changes in entangled particle states, providing a fundamentally secure communication channel. Explore deeper insights into how quantum entanglement revolutionizes cryptographic security by visiting our comprehensive guide.
Eavesdropping Detection (Quantum Key Distribution)
Diffie-Hellman key exchange relies on computational hardness assumptions, making it vulnerable to eavesdropping if an attacker has sufficient computational power, whereas Quantum Key Distribution (QKD) enables real-time detection of eavesdropping through quantum state disturbances. QKD exploits the principles of quantum mechanics, such as the no-cloning theorem and quantum entanglement, to ensure that any interception attempt alters the quantum states, alerting communicating parties to potential security breaches. Explore the fundamental differences and security advantages of these protocols in protecting sensitive communications.
Source and External Links
How Diffie-Hellman Key Exchange Provides Encrypted ... - Diffie-Hellman key exchange is a method for two parties to securely agree on a shared symmetric key over a public network by using large prime numbers and modular exponentiation, without ever revealing their private secrets.
What is Diffie-Hellman Key Exchange? - Diffie-Hellman key exchange enables two parties to securely establish a shared secret key over a public channel, which can then be used for symmetric encryption, typically by raising numbers to a selected power without transmitting the actual key components.
Diffie-Hellman Keys - Win32 apps - After agreeing on a prime number and a generator, each party computes their public key from their secret key, exchanges public keys, and then each independently calculates an identical session key for encrypting communications, even if the channel is insecure.
 dowidth.com
dowidth.com