Trustless computing enables secure transactions without relying on intermediaries by using decentralized networks and consensus algorithms, reducing the risk of single points of failure. Digital signatures ensure data integrity and authenticate identity through cryptographic methods, providing non-repudiation and verifying the origin of messages or documents. Explore the differences and applications of trustless computing and digital signatures to understand their roles in enhancing cybersecurity.
Why it is important
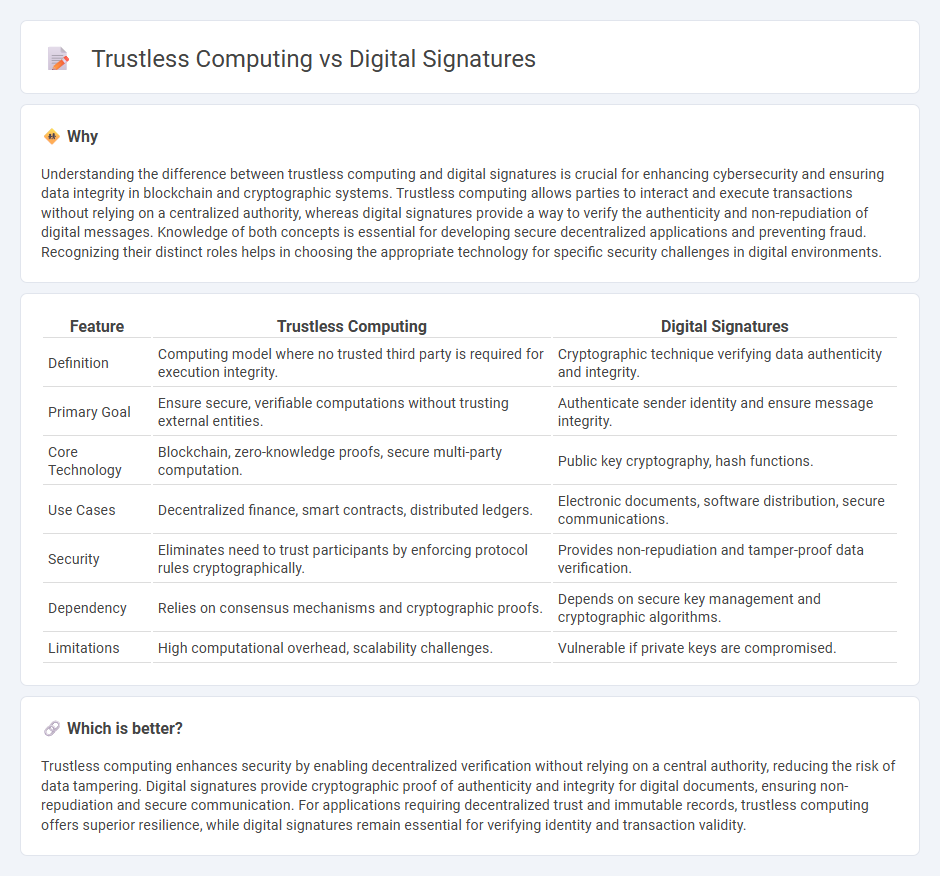
Understanding the difference between trustless computing and digital signatures is crucial for enhancing cybersecurity and ensuring data integrity in blockchain and cryptographic systems. Trustless computing allows parties to interact and execute transactions without relying on a centralized authority, whereas digital signatures provide a way to verify the authenticity and non-repudiation of digital messages. Knowledge of both concepts is essential for developing secure decentralized applications and preventing fraud. Recognizing their distinct roles helps in choosing the appropriate technology for specific security challenges in digital environments.
Comparison Table
| Feature | Trustless Computing | Digital Signatures |
|---|---|---|
| Definition | Computing model where no trusted third party is required for execution integrity. | Cryptographic technique verifying data authenticity and integrity. |
| Primary Goal | Ensure secure, verifiable computations without trusting external entities. | Authenticate sender identity and ensure message integrity. |
| Core Technology | Blockchain, zero-knowledge proofs, secure multi-party computation. | Public key cryptography, hash functions. |
| Use Cases | Decentralized finance, smart contracts, distributed ledgers. | Electronic documents, software distribution, secure communications. |
| Security | Eliminates need to trust participants by enforcing protocol rules cryptographically. | Provides non-repudiation and tamper-proof data verification. |
| Dependency | Relies on consensus mechanisms and cryptographic proofs. | Depends on secure key management and cryptographic algorithms. |
| Limitations | High computational overhead, scalability challenges. | Vulnerable if private keys are compromised. |
Which is better?
Trustless computing enhances security by enabling decentralized verification without relying on a central authority, reducing the risk of data tampering. Digital signatures provide cryptographic proof of authenticity and integrity for digital documents, ensuring non-repudiation and secure communication. For applications requiring decentralized trust and immutable records, trustless computing offers superior resilience, while digital signatures remain essential for verifying identity and transaction validity.
Connection
Trustless computing leverages cryptographic techniques to enable secure transactions without relying on a central authority. Digital signatures play a crucial role in this framework by providing verifiable proof of authenticity and integrity of data exchanged between parties. This connection ensures that trustless systems can validate participants and transactions efficiently, enhancing security in decentralized networks.
Key Terms
Cryptographic Algorithms
Cryptographic algorithms lie at the core of digital signatures, ensuring data authenticity and integrity through asymmetric key pairs and hash functions. Trustless computing leverages similar cryptographic principles but emphasizes decentralized consensus mechanisms like zero-knowledge proofs and secure multiparty computation for enhanced security without trusted intermediaries. Explore the intricate differences and applications of these cryptographic foundations to deepen your understanding of secure digital interactions.
Decentralization
Digital signatures play a crucial role in decentralized systems by ensuring data integrity and authenticating transactions without relying on a central authority. Trustless computing leverages blockchain technology and cryptographic protocols to facilitate secure interactions among untrusted parties, enhancing transparency and decentralization. Explore the nuances of decentralization through digital signatures and trustless computing to deepen your understanding of secure distributed networks.
Public Key Infrastructure (PKI)
Digital signatures rely heavily on Public Key Infrastructure (PKI) to ensure the authenticity and integrity of electronic documents by binding a public key with an identity verified by a trusted Certificate Authority (CA). Trustless computing, often associated with blockchain technology, eliminates the need for centralized intermediaries by using cryptographic algorithms and consensus mechanisms to validate transactions and identities securely. Explore the nuances between PKI-based digital signatures and trustless systems to understand their impact on cybersecurity.
Source and External Links
What is a Digital Signature? | DigiCert FAQ - Digital signatures use public key infrastructure to cryptographically bind a signer's identity to a document, ensuring authenticity and integrity, and are often legally recognized as equivalent to handwritten signatures.
What is a Digital Signature? | Definition from TechTarget - A digital signature is a mathematical technique that validates the authenticity and integrity of digital documents or messages, providing higher security than traditional signatures and often carrying legal weight.
Understanding digital signatures | Docusign - Digital signatures require a secure private key for signing, a corresponding public key for verification, and are invalidated if the document is altered after signing, ensuring tamper-proof transactions.
 dowidth.com
dowidth.com