Zero Trust Architecture enforces strict identity verification for every user and device attempting to access resources, minimizing risks by assuming no implicit trust within the network perimeter. Least Privilege limits user permissions to the minimum necessary for their role, reducing potential attack surfaces and the impact of compromised accounts. Explore how combining these approaches can strengthen your organization's cybersecurity posture.
Why it is important
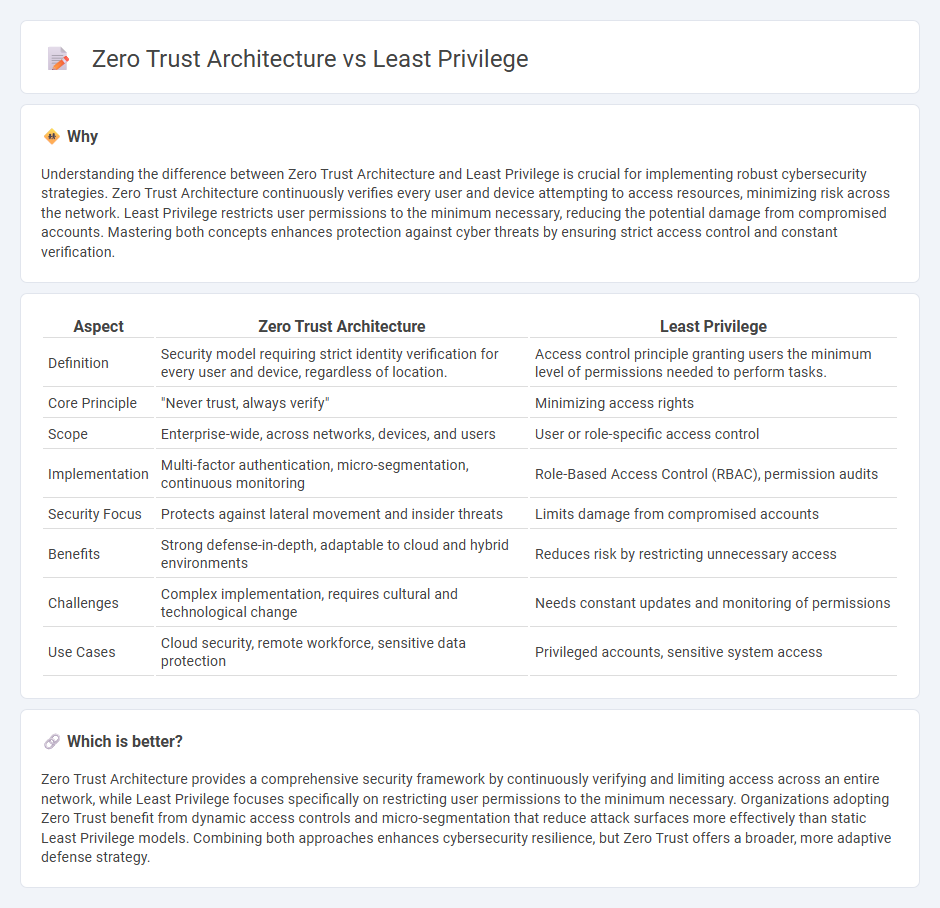
Understanding the difference between Zero Trust Architecture and Least Privilege is crucial for implementing robust cybersecurity strategies. Zero Trust Architecture continuously verifies every user and device attempting to access resources, minimizing risk across the network. Least Privilege restricts user permissions to the minimum necessary, reducing the potential damage from compromised accounts. Mastering both concepts enhances protection against cyber threats by ensuring strict access control and constant verification.
Comparison Table
| Aspect | Zero Trust Architecture | Least Privilege |
|---|---|---|
| Definition | Security model requiring strict identity verification for every user and device, regardless of location. | Access control principle granting users the minimum level of permissions needed to perform tasks. |
| Core Principle | "Never trust, always verify" | Minimizing access rights |
| Scope | Enterprise-wide, across networks, devices, and users | User or role-specific access control |
| Implementation | Multi-factor authentication, micro-segmentation, continuous monitoring | Role-Based Access Control (RBAC), permission audits |
| Security Focus | Protects against lateral movement and insider threats | Limits damage from compromised accounts |
| Benefits | Strong defense-in-depth, adaptable to cloud and hybrid environments | Reduces risk by restricting unnecessary access |
| Challenges | Complex implementation, requires cultural and technological change | Needs constant updates and monitoring of permissions |
| Use Cases | Cloud security, remote workforce, sensitive data protection | Privileged accounts, sensitive system access |
Which is better?
Zero Trust Architecture provides a comprehensive security framework by continuously verifying and limiting access across an entire network, while Least Privilege focuses specifically on restricting user permissions to the minimum necessary. Organizations adopting Zero Trust benefit from dynamic access controls and micro-segmentation that reduce attack surfaces more effectively than static Least Privilege models. Combining both approaches enhances cybersecurity resilience, but Zero Trust offers a broader, more adaptive defense strategy.
Connection
Zero trust architecture and least privilege are fundamentally connected through their shared goal of minimizing access risks by enforcing strict identity verification and limiting user permissions to only what is necessary. Zero trust operates on the principle of "never trust, always verify," continuously authenticating and authorizing every access request, while least privilege restricts users and systems from obtaining excessive access rights, reducing the attack surface. Implementing both together enhances cybersecurity posture by ensuring that even if credentials are compromised, unauthorized lateral movement and data breaches are significantly curtailed.
Key Terms
Access Control
Least privilege limits user and system access rights to the minimum necessary for their function, reducing the risk of unauthorized actions. Zero Trust Architecture enforces strict identity verification and continuous monitoring, assuming no implicit trust regardless of network location. Explore how these models redefine access control strategies for enhanced cybersecurity.
Authentication
Least privilege enforces strict access control by granting users the minimal level of permissions necessary to perform their tasks, significantly reducing the risk of unauthorized access during authentication processes. Zero Trust Architecture extends this concept by continuously verifying every authentication request, assuming no user or device is inherently trustworthy, and employing multifactor authentication and stringent identity verification protocols. Explore how combining least privilege principles with Zero Trust Authentication enhances overall cybersecurity resilience and access management.
Micro-Segmentation
Least privilege enforces user access rights to the minimum necessary for tasks, reducing potential attack surfaces within networks. Zero trust architecture extends this principle by continuously verifying identity and device context, often implemented through micro-segmentation to isolate workloads and minimize lateral movement of threats. Explore how micro-segmentation enhances security in zero trust frameworks for deeper insights.
Source and External Links
What is Least Privilege? - The principle of least privilege (PoLP) is a security concept in which a user is given only the minimum levels of access or permissions necessary to perform their job functions, reducing potential security risks.
What is principle of least privilege? - The principle of least privilege ensures users only have the access they truly need, minimizing the negative impact if an account is compromised or an insider threat occurs.
What Is Least Privilege & Why Do You Need It? - Least privilege restricts access rights for users, accounts, and computing processes to only those resources absolutely required, serving as a fundamental best practice to reduce security risk and minimize disruption.
 dowidth.com
dowidth.com