Quantum key distribution (QKD) leverages the principles of quantum mechanics to enable the secure exchange of encryption keys, offering theoretically unbreakable security by detecting any eavesdropping attempts. Secure Sockets Layer (SSL), now succeeded by Transport Layer Security (TLS), provides encryption and data integrity for internet communications through a combination of public-key and symmetric cryptography, widely adopted for securing web traffic. Explore the differences between QKD and SSL to understand the future of cryptographic security protocols.
Why it is important
Understanding the difference between Quantum Key Distribution (QKD) and Secure Sockets Layer (SSL) is crucial for enhancing cybersecurity strategies. QKD leverages quantum mechanics to provide theoretically unbreakable encryption by detecting eavesdropping, whereas SSL relies on classical cryptographic algorithms vulnerable to future quantum attacks. Organizations must distinguish between these technologies to future-proof data protection and ensure secure communication channels. This knowledge enables informed decisions on adopting cutting-edge security protocols aligned with evolving threat landscapes.
Comparison Table
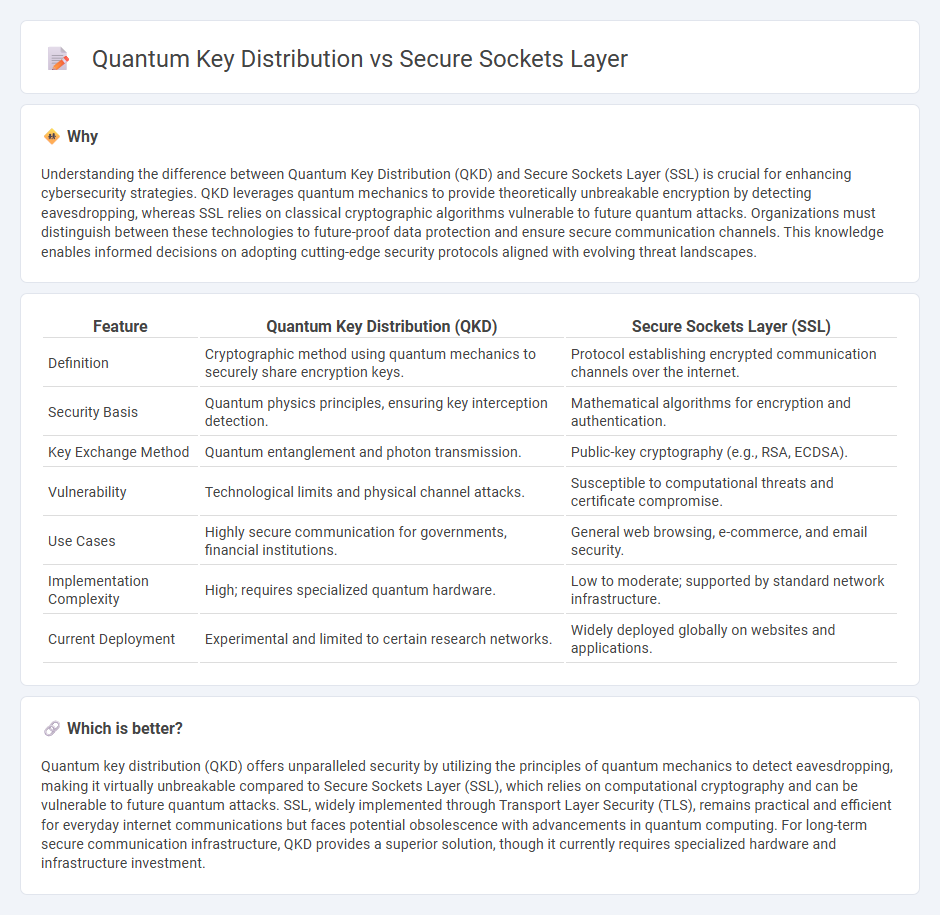
| Feature | Quantum Key Distribution (QKD) | Secure Sockets Layer (SSL) |
|---|---|---|
| Definition | Cryptographic method using quantum mechanics to securely share encryption keys. | Protocol establishing encrypted communication channels over the internet. |
| Security Basis | Quantum physics principles, ensuring key interception detection. | Mathematical algorithms for encryption and authentication. |
| Key Exchange Method | Quantum entanglement and photon transmission. | Public-key cryptography (e.g., RSA, ECDSA). |
| Vulnerability | Technological limits and physical channel attacks. | Susceptible to computational threats and certificate compromise. |
| Use Cases | Highly secure communication for governments, financial institutions. | General web browsing, e-commerce, and email security. |
| Implementation Complexity | High; requires specialized quantum hardware. | Low to moderate; supported by standard network infrastructure. |
| Current Deployment | Experimental and limited to certain research networks. | Widely deployed globally on websites and applications. |
Which is better?
Quantum key distribution (QKD) offers unparalleled security by utilizing the principles of quantum mechanics to detect eavesdropping, making it virtually unbreakable compared to Secure Sockets Layer (SSL), which relies on computational cryptography and can be vulnerable to future quantum attacks. SSL, widely implemented through Transport Layer Security (TLS), remains practical and efficient for everyday internet communications but faces potential obsolescence with advancements in quantum computing. For long-term secure communication infrastructure, QKD provides a superior solution, though it currently requires specialized hardware and infrastructure investment.
Connection
Quantum Key Distribution (QKD) enhances Secure Sockets Layer (SSL) by providing theoretically unbreakable encryption keys through quantum mechanics, which SSL protocols use to establish secure communication channels. SSL relies on cryptographic keys for data encryption, and QKD ensures these keys are generated and shared with absolute security against eavesdropping. Integrating QKD with SSL can significantly strengthen cybersecurity by preventing key interception in network transmissions.
Key Terms
Encryption
Secure Sockets Layer (SSL) uses classical encryption algorithms like AES and RSA to protect data, relying on computational complexity for security, while Quantum Key Distribution (QKD) leverages quantum mechanics principles to enable theoretically unbreakable encryption by securely sharing cryptographic keys. SSL is widely adopted for internet security but remains vulnerable to future quantum computing attacks, whereas QKD provides forward secrecy resistant to both classical and quantum attacks. Explore more about how these encryption methods compare in securing digital communications against evolving threats.
Quantum Cryptography
Quantum cryptography leverages principles of quantum mechanics to provide unprecedented security in data transmission, contrasting traditional Secure Sockets Layer (SSL) protocols that rely on complex mathematical algorithms vulnerable to future quantum attacks. Quantum Key Distribution (QKD) enables two parties to generate a shared, secret encryption key using quantum bits (qubits) that are inherently resistant to interception or duplication, ensuring data confidentiality even against quantum computers. Explore the advancements and practical applications of quantum cryptography to understand its transformative impact on secure communications.
Key Exchange
Secure Sockets Layer (SSL) uses asymmetric cryptography for key exchange, typically relying on RSA or Diffie-Hellman algorithms, providing secure channel establishment but remaining vulnerable to future quantum attacks. Quantum Key Distribution (QKD) leverages principles of quantum mechanics to enable information-theoretic secure key exchange, detecting eavesdropping through quantum state disturbances, thus offering enhanced security against quantum computing threats. Explore the intricacies of SSL and QKD key exchange mechanisms to understand evolving cybersecurity solutions.
Source and External Links
Secure Socket Layer (SSL) - GeeksforGeeks - SSL is an Internet security protocol created by Netscape in 1995, designed to encrypt data and secure communications by using a two-layered protocol over TCP, providing privacy, authentication, and data integrity between sender and receiver.
Transport Layer Security - Wikipedia - TLS, the successor to SSL, is a cryptographic protocol that secures communications by providing private, authenticated, and reliable encrypted connections over networks like the Internet, using a handshake to negotiate encryption keys before data transmission.
What is SSL (Secure Sockets Layer)? | Definition from TechTarget - SSL secures web client-server connections by encrypting data with public/private key cryptography, enabling privacy, authentication, and integrity, and was the first widely adopted network protocol that laid the foundation for secure e-commerce and trusted Internet communications.
 dowidth.com
dowidth.com