Quantum-safe cryptography and hash-based cryptography represent critical advancements in securing digital information against emerging quantum computing threats. Quantum-safe cryptography utilizes algorithms designed to withstand decryption attempts by quantum computers, whereas hash-based cryptography relies on the collision-resistant properties of cryptographic hash functions to provide secure digital signatures. Discover how these technologies are shaping the future of cybersecurity and safeguarding sensitive data.
Why it is important
Understanding the difference between quantum-safe cryptography and hash-based cryptography is crucial for securing data against future quantum computing threats. Quantum-safe cryptography includes algorithms resistant to quantum attacks, while hash-based cryptography specifically uses hash functions for digital signatures with proven security. Organizations must adopt these technologies to protect sensitive information from being compromised by emerging quantum capabilities. Quantum-safe solutions ensure long-term data confidentiality and integrity in a quantum-enabled world.
Comparison Table
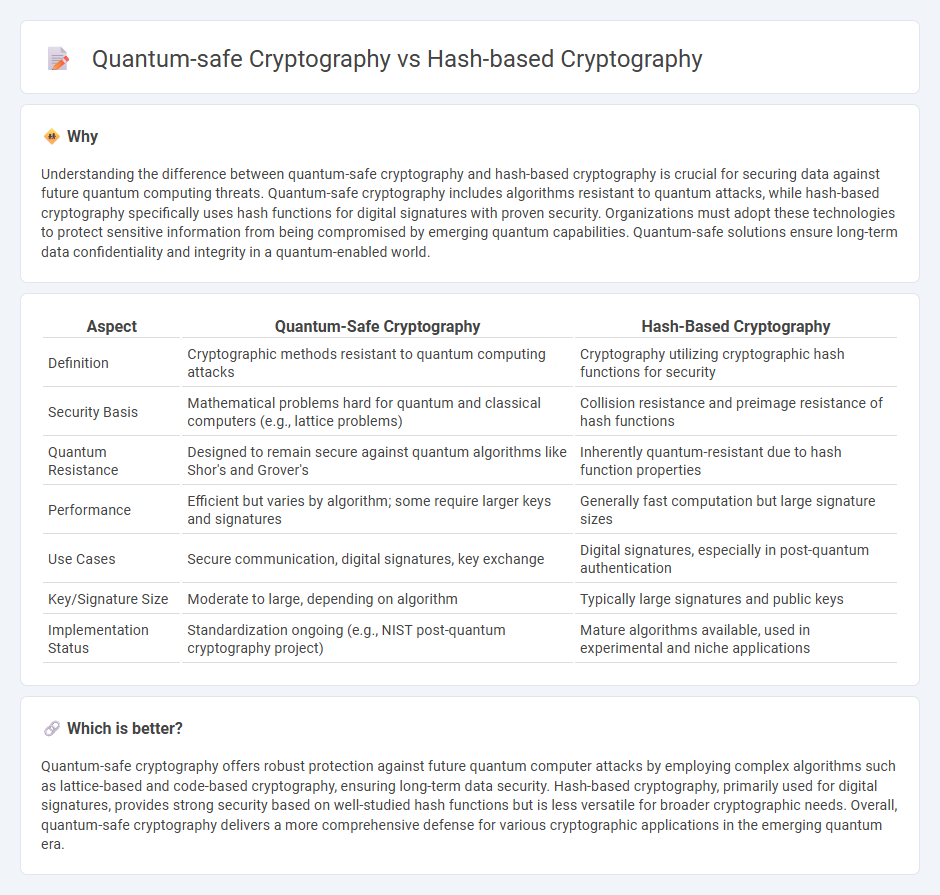
| Aspect | Quantum-Safe Cryptography | Hash-Based Cryptography |
|---|---|---|
| Definition | Cryptographic methods resistant to quantum computing attacks | Cryptography utilizing cryptographic hash functions for security |
| Security Basis | Mathematical problems hard for quantum and classical computers (e.g., lattice problems) | Collision resistance and preimage resistance of hash functions |
| Quantum Resistance | Designed to remain secure against quantum algorithms like Shor's and Grover's | Inherently quantum-resistant due to hash function properties |
| Performance | Efficient but varies by algorithm; some require larger keys and signatures | Generally fast computation but large signature sizes |
| Use Cases | Secure communication, digital signatures, key exchange | Digital signatures, especially in post-quantum authentication |
| Key/Signature Size | Moderate to large, depending on algorithm | Typically large signatures and public keys |
| Implementation Status | Standardization ongoing (e.g., NIST post-quantum cryptography project) | Mature algorithms available, used in experimental and niche applications |
Which is better?
Quantum-safe cryptography offers robust protection against future quantum computer attacks by employing complex algorithms such as lattice-based and code-based cryptography, ensuring long-term data security. Hash-based cryptography, primarily used for digital signatures, provides strong security based on well-studied hash functions but is less versatile for broader cryptographic needs. Overall, quantum-safe cryptography delivers a more comprehensive defense for various cryptographic applications in the emerging quantum era.
Connection
Quantum-safe cryptography and hash-based cryptography are connected through their shared goal of securing data against quantum computing attacks by utilizing algorithms resistant to quantum decryption methods. Hash-based cryptography leverages cryptographic hash functions to create secure digital signatures, making it a prominent candidate within the broader category of quantum-safe cryptographic techniques. This connection highlights their crucial role in developing next-generation security protocols capable of protecting sensitive information in a post-quantum world.
Key Terms
Hash functions
Hash-based cryptography leverages the security properties of hash functions, such as collision resistance and preimage resistance, to create digital signatures that remain secure even against quantum attacks. Quantum-safe cryptography encompasses a broader range of algorithms designed to withstand quantum computing threats, with hash-based schemes being a prominent and well-studied subset that uses hash functions for their simplicity and proven security assumptions. Explore the advantages and implementations of hash-based hash functions in the evolving landscape of quantum-safe cryptography to secure your data future-proof.
Quantum resistance
Hash-based cryptography offers strong quantum resistance by relying on the security properties of hash functions, which remain secure against quantum attacks such as Grover's algorithm. Quantum-safe cryptography encompasses various approaches including lattice-based, code-based, and multivariate cryptographic schemes, all designed to withstand adversaries equipped with quantum computers. Explore the latest research and implementation strategies to understand the future of secure communication in a quantum era.
Digital signatures
Hash-based cryptography relies on the collision resistance of hash functions to create secure digital signatures, making it resilient against attacks from quantum computers. Quantum-safe cryptography encompasses a broader range of algorithms, including lattice-based and code-based schemes, designed to secure digital signatures against both classical and quantum attacks. Explore the latest advancements in quantum-resistant digital signature methods for robust cybersecurity solutions.
Source and External Links
Hash-based cryptography - This form of cryptography involves using hash functions to construct cryptographic primitives, such as digital signatures, and is notable for its resistance to quantum attacks.
Hash-based Signatures: An illustrated Primer - This page provides an illustrated explanation of how hash-based signature schemes work, including generation and verification processes.
Post-quantum cryptography: Hash-based signatures - This article discusses hash-based signatures as a replacement for current public key cryptography, offering resistance against quantum computers.
 dowidth.com
dowidth.com