Zero Trust Architecture enforces strict identity verification and continuous monitoring, eliminating implicit trust within network perimeters. Unlike perimeter-based security, which relies on defined network boundaries vulnerable to breaches, Zero Trust ensures every access request is authenticated and authorized regardless of location. Explore how shifting from perimeter defenses to Zero Trust enhances cybersecurity resilience and reduces attack surfaces.
Why it is important
Understanding the difference between zero trust architecture and perimeter-based security is crucial as zero trust assumes no implicit trust and continuously verifies every user and device, enhancing protection against insider threats and lateral attacks. Perimeter-based security relies on distinct network boundaries, which can be vulnerable once breached. Zero trust improves cybersecurity by enforcing strict access controls and segmentation regardless of location. Organizations adopting zero trust reduce the risk of data breaches and adapt to modern, cloud-driven IT environments.
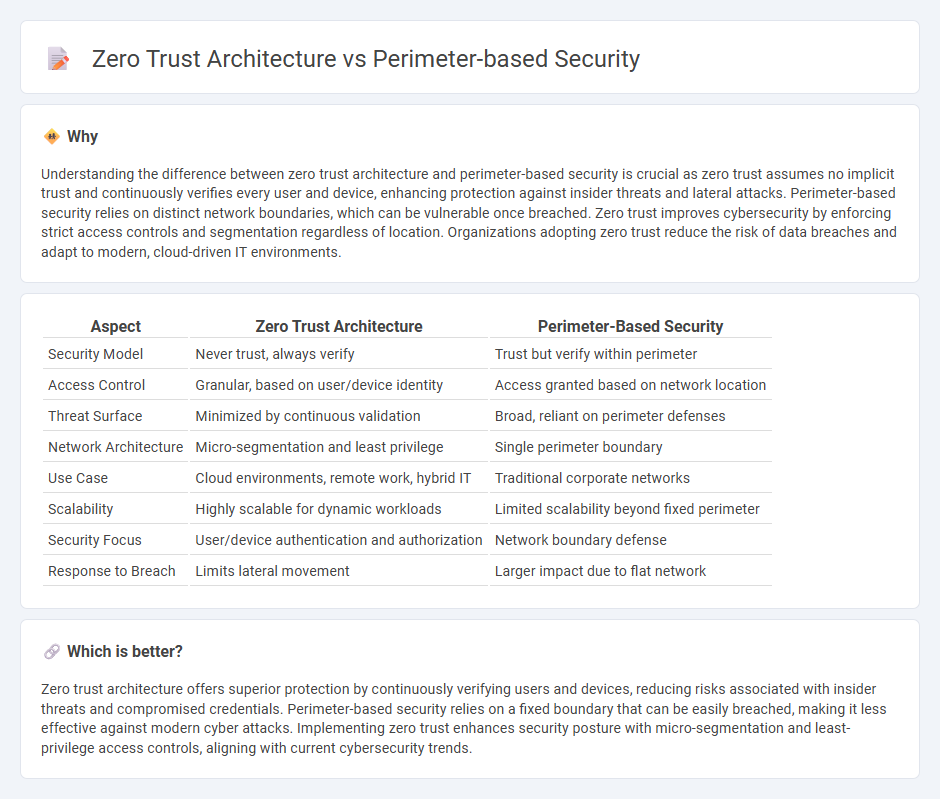
Comparison Table
| Aspect | Zero Trust Architecture | Perimeter-Based Security |
|---|---|---|
| Security Model | Never trust, always verify | Trust but verify within perimeter |
| Access Control | Granular, based on user/device identity | Access granted based on network location |
| Threat Surface | Minimized by continuous validation | Broad, reliant on perimeter defenses |
| Network Architecture | Micro-segmentation and least privilege | Single perimeter boundary |
| Use Case | Cloud environments, remote work, hybrid IT | Traditional corporate networks |
| Scalability | Highly scalable for dynamic workloads | Limited scalability beyond fixed perimeter |
| Security Focus | User/device authentication and authorization | Network boundary defense |
| Response to Breach | Limits lateral movement | Larger impact due to flat network |
Which is better?
Zero trust architecture offers superior protection by continuously verifying users and devices, reducing risks associated with insider threats and compromised credentials. Perimeter-based security relies on a fixed boundary that can be easily breached, making it less effective against modern cyber attacks. Implementing zero trust enhances security posture with micro-segmentation and least-privilege access controls, aligning with current cybersecurity trends.
Connection
Zero trust architecture and perimeter-based security both focus on protecting organizational networks but differ fundamentally in approach. Zero trust eliminates implicit trust by continuously verifying every user and device, regardless of location, while perimeter-based security relies on guarding the network boundary to prevent unauthorized access. Integrating zero trust principles strengthens perimeter defenses by ensuring strict access control and minimizing insider threats.
Key Terms
Network Perimeter
Network perimeter security relies on a defined boundary that separates trusted internal networks from untrusted external ones, using firewalls and intrusion detection systems to monitor and control traffic. Zero Trust Architecture eliminates the traditional perimeter, enforcing strict identity verification and micro-segmentation across all network access points regardless of location. Explore how shifting from perimeter-based security to Zero Trust can strengthen your organization's defense strategy.
Micro-segmentation
Perimeter-based security relies on a defined network boundary to protect assets, while Zero Trust Architecture (ZTA) eliminates implicit trust and verifies every access request regardless of location. Micro-segmentation in ZTA enhances security by dividing networks into granular zones, isolating workloads, and enforcing strict access controls to minimize lateral movement of threats. Explore how implementing micro-segmentation can strengthen your Zero Trust strategy and reduce attack surfaces effectively.
Identity and Access Management (IAM)
Perimeter-based security relies on defined network boundaries to restrict access, often depending on firewalls and VPNs, while Zero Trust Architecture (ZTA) emphasizes continuous verification of user identities and strict Identity and Access Management (IAM) policies regardless of network location. ZTA uses principles like least privilege access, multi-factor authentication (MFA), and context-aware access controls to minimize risks associated with internal threats and lateral movement within networks. Explore more on how modern IAM solutions transform security frameworks by adopting Zero Trust strategies.
Source and External Links
Network Perimeter Security - This webpage explains how perimeter security protects an organization's network boundaries from unauthorized access and threats using technologies like firewalls and intrusion detection systems.
What is Perimeter Security? Benefits and Key Elements - This article discusses perimeter security as the process of protecting a company's network boundaries from hackers, utilizing technologies such as firewalls and intrusion prevention systems.
The Perimeter Problem - This blog post highlights the challenges of traditional perimeter security due to issues like insider threats and the inability to effectively defend against modern threats.
 dowidth.com
dowidth.com