Zero-knowledge proofs enable one party to prove knowledge of a secret without revealing the secret itself, ensuring privacy and security in cryptographic protocols. Oblivious transfer allows a sender to transfer information to a receiver without knowing which piece of information was received, enhancing secure multi-party computations. Explore the fundamental differences and applications of these cutting-edge cryptographic techniques to understand their impact on secure digital communication.
Why it is important
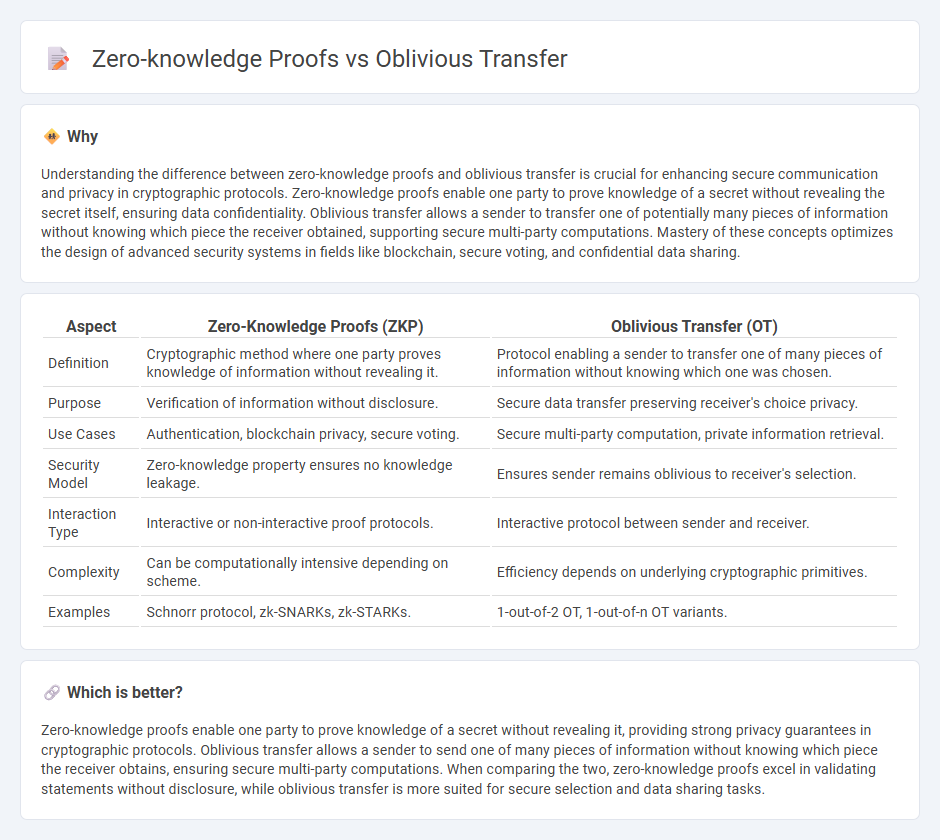
Understanding the difference between zero-knowledge proofs and oblivious transfer is crucial for enhancing secure communication and privacy in cryptographic protocols. Zero-knowledge proofs enable one party to prove knowledge of a secret without revealing the secret itself, ensuring data confidentiality. Oblivious transfer allows a sender to transfer one of potentially many pieces of information without knowing which piece the receiver obtained, supporting secure multi-party computations. Mastery of these concepts optimizes the design of advanced security systems in fields like blockchain, secure voting, and confidential data sharing.
Comparison Table
| Aspect | Zero-Knowledge Proofs (ZKP) | Oblivious Transfer (OT) |
|---|---|---|
| Definition | Cryptographic method where one party proves knowledge of information without revealing it. | Protocol enabling a sender to transfer one of many pieces of information without knowing which one was chosen. |
| Purpose | Verification of information without disclosure. | Secure data transfer preserving receiver's choice privacy. |
| Use Cases | Authentication, blockchain privacy, secure voting. | Secure multi-party computation, private information retrieval. |
| Security Model | Zero-knowledge property ensures no knowledge leakage. | Ensures sender remains oblivious to receiver's selection. |
| Interaction Type | Interactive or non-interactive proof protocols. | Interactive protocol between sender and receiver. |
| Complexity | Can be computationally intensive depending on scheme. | Efficiency depends on underlying cryptographic primitives. |
| Examples | Schnorr protocol, zk-SNARKs, zk-STARKs. | 1-out-of-2 OT, 1-out-of-n OT variants. |
Which is better?
Zero-knowledge proofs enable one party to prove knowledge of a secret without revealing it, providing strong privacy guarantees in cryptographic protocols. Oblivious transfer allows a sender to send one of many pieces of information without knowing which piece the receiver obtains, ensuring secure multi-party computations. When comparing the two, zero-knowledge proofs excel in validating statements without disclosure, while oblivious transfer is more suited for secure selection and data sharing tasks.
Connection
Zero-knowledge proofs and oblivious transfer are cryptographic protocols enabling secure information exchange without revealing underlying data. Zero-knowledge proofs allow one party to verify knowledge of a secret without disclosing it, while oblivious transfer lets a sender transmit one of many pieces of data without knowing which piece the receiver obtained. Both concepts underpin privacy-preserving technologies in secure multiparty computation and blockchain applications.
Key Terms
Privacy
Oblivious transfer enables secure data exchange where the sender remains unaware of the receiver's chosen information, preserving privacy through selective disclosure. Zero-knowledge proofs allow one party to prove knowledge of a secret without revealing the secret itself, enhancing privacy by minimizing the information shared. Explore deeper insights into how these cryptographic protocols safeguard privacy in digital communication.
Cryptographic Protocol
Oblivious transfer enables secure data exchange where the sender remains unaware of which piece of information the receiver obtains, ensuring privacy through cryptographic protocols. Zero-knowledge proofs allow one party to prove knowledge of a secret without revealing the secret itself, enhancing verification while preserving confidentiality in cryptographic systems. Explore how these cryptographic protocols differ and complement each other in secure communications.
Information Leakage
Oblivious transfer protocols ensure that a sender transfers one of many possible pieces of information without knowing which piece was received, minimizing information leakage by design. Zero-knowledge proofs allow a prover to convince a verifier of a statement's validity without revealing any additional information beyond the truth of the statement itself. Explore deeper insights on how these cryptographic primitives balance functionality and privacy in safeguarding sensitive data.
Source and External Links
Oblivious Transfer - University of Illinois Urbana-Champaign - Oblivious transfer is a cryptographic primitive where a sender has multiple messages and a receiver chooses to learn exactly one without the sender knowing which was chosen, ensuring security so the sender does not know the receiver's choice and the receiver learns nothing about unchosen messages.
Oblivious transfer - Wikipedia - In cryptography, oblivious transfer is a protocol allowing a sender to transfer one of many pieces of information to a receiver while remaining oblivious to what was transferred; it underpins secure multiparty computation and comes in several forms, including Rabin's and 1-out-of-2 oblivious transfers.
Lecture 10 1 Oblivious Transfer - UCLA - Rabin oblivious transfer simulates a noisy channel where the sender sends a bit and the receiver randomly receives the bit or an erasure, while 1-out-of-2 oblivious transfer allows the receiver to select exactly one bit from a pair without the sender knowing which was received.
 dowidth.com
dowidth.com