Homomorphic encryption enables computations on encrypted data without revealing the underlying information, enhancing privacy in cloud computing and secure data analysis. Asymmetric encryption relies on a pair of keys--public and private--for secure communication, commonly used in digital signatures and SSL/TLS protocols. Explore the unique advantages and applications of these encryption techniques to understand their impact on data security.
Why it is important
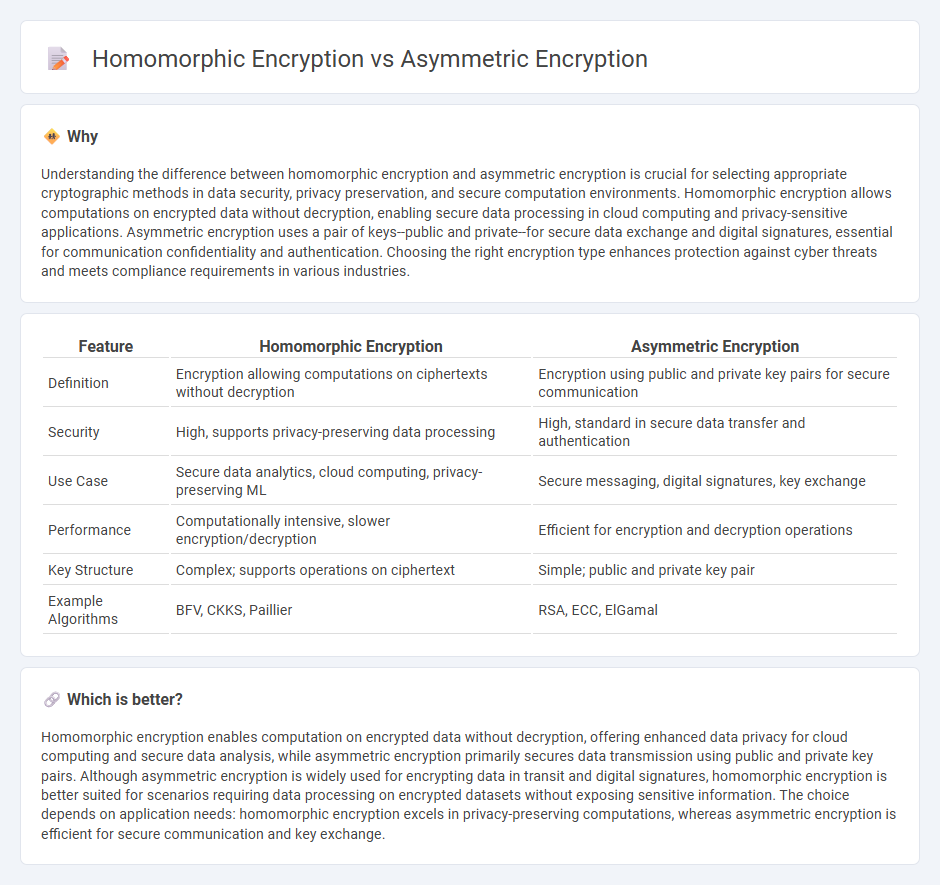
Understanding the difference between homomorphic encryption and asymmetric encryption is crucial for selecting appropriate cryptographic methods in data security, privacy preservation, and secure computation environments. Homomorphic encryption allows computations on encrypted data without decryption, enabling secure data processing in cloud computing and privacy-sensitive applications. Asymmetric encryption uses a pair of keys--public and private--for secure data exchange and digital signatures, essential for communication confidentiality and authentication. Choosing the right encryption type enhances protection against cyber threats and meets compliance requirements in various industries.
Comparison Table
| Feature | Homomorphic Encryption | Asymmetric Encryption |
|---|---|---|
| Definition | Encryption allowing computations on ciphertexts without decryption | Encryption using public and private key pairs for secure communication |
| Security | High, supports privacy-preserving data processing | High, standard in secure data transfer and authentication |
| Use Case | Secure data analytics, cloud computing, privacy-preserving ML | Secure messaging, digital signatures, key exchange |
| Performance | Computationally intensive, slower encryption/decryption | Efficient for encryption and decryption operations |
| Key Structure | Complex; supports operations on ciphertext | Simple; public and private key pair |
| Example Algorithms | BFV, CKKS, Paillier | RSA, ECC, ElGamal |
Which is better?
Homomorphic encryption enables computation on encrypted data without decryption, offering enhanced data privacy for cloud computing and secure data analysis, while asymmetric encryption primarily secures data transmission using public and private key pairs. Although asymmetric encryption is widely used for encrypting data in transit and digital signatures, homomorphic encryption is better suited for scenarios requiring data processing on encrypted datasets without exposing sensitive information. The choice depends on application needs: homomorphic encryption excels in privacy-preserving computations, whereas asymmetric encryption is efficient for secure communication and key exchange.
Connection
Homomorphic encryption and asymmetric encryption both utilize key pairs for secure data processing, enabling encryption and decryption with separate keys. Homomorphic encryption extends the functionality of asymmetric encryption by allowing computations directly on encrypted data without revealing the plaintext. This connection enhances data privacy and security in cloud computing and confidential data analysis applications.
Key Terms
Public/private key
Public/private key mechanisms in asymmetric encryption use separate keys for encryption and decryption, ensuring secure data exchange by allowing anyone to encrypt with the public key while only the holder of the private key can decrypt. Homomorphic encryption also leverages public/private key pairs but enables computations directly on encrypted data without needing decryption first, preserving privacy and data confidentiality during processing. Explore how these cryptographic techniques impact security and data privacy in modern digital communications.
Ciphertext
Asymmetric encryption uses a pair of public and private keys to secure ciphertext, ensuring that data can only be decrypted by the intended recipient. Homomorphic encryption enables computations to be performed directly on ciphertext without decryption, preserving data privacy throughout processing. Explore the unique applications and benefits of each encryption method in securing sensitive information.
Computation on encrypted data
Asymmetric encryption uses paired public and private keys to secure data, enabling decryption only by the private key holder, but requires data to be decrypted before computation. Homomorphic encryption allows direct computation on encrypted data without decryption, preserving confidentiality throughout processing and enabling secure cloud computing and data analysis. Explore the advantages and practical applications of homomorphic encryption to understand its impact on secure computations.
Source and External Links
What is Asymmetric Encryption? - IBM - Asymmetric encryption uses two keys, a public key for encryption and a private key for decryption, enabling secure data exchange without needing to share a secret key and is often combined with symmetric encryption for efficiency.
Asymmetric encryption | Cloud KMS - Asymmetric encryption uses a public/private key pair where data encrypted with a recipient's public key can only be decrypted by the recipient's private key, typically applied to encrypt small data like keys rather than large plaintexts.
What is an Asymmetric Encryption? - GeeksforGeeks - Known as public-key cryptography, this method uses a public key to encrypt data and a private key to decrypt it, allowing secure communication and digital signatures without exchanging secret keys beforehand.
 dowidth.com
dowidth.com