Flash loan attacks exploit instant, uncollateralized borrowing to manipulate DeFi protocols, causing significant financial losses through rapid, temporary liquidity changes. Sybil attacks involve creating numerous fake identities to gain disproportionate influence in decentralized networks, undermining trust and consensus mechanisms. Explore deeper into how these distinct threats compromise blockchain security and financial integrity.
Why it is important
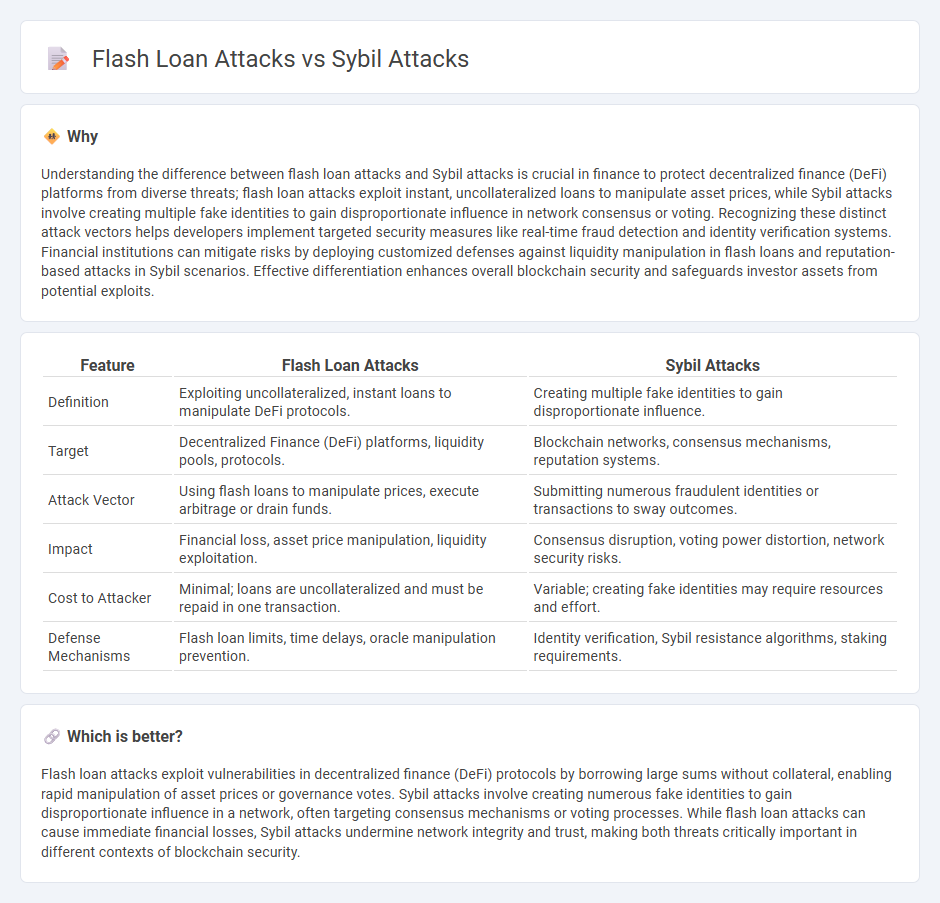
Understanding the difference between flash loan attacks and Sybil attacks is crucial in finance to protect decentralized finance (DeFi) platforms from diverse threats; flash loan attacks exploit instant, uncollateralized loans to manipulate asset prices, while Sybil attacks involve creating multiple fake identities to gain disproportionate influence in network consensus or voting. Recognizing these distinct attack vectors helps developers implement targeted security measures like real-time fraud detection and identity verification systems. Financial institutions can mitigate risks by deploying customized defenses against liquidity manipulation in flash loans and reputation-based attacks in Sybil scenarios. Effective differentiation enhances overall blockchain security and safeguards investor assets from potential exploits.
Comparison Table
| Feature | Flash Loan Attacks | Sybil Attacks |
|---|---|---|
| Definition | Exploiting uncollateralized, instant loans to manipulate DeFi protocols. | Creating multiple fake identities to gain disproportionate influence. |
| Target | Decentralized Finance (DeFi) platforms, liquidity pools, protocols. | Blockchain networks, consensus mechanisms, reputation systems. |
| Attack Vector | Using flash loans to manipulate prices, execute arbitrage or drain funds. | Submitting numerous fraudulent identities or transactions to sway outcomes. |
| Impact | Financial loss, asset price manipulation, liquidity exploitation. | Consensus disruption, voting power distortion, network security risks. |
| Cost to Attacker | Minimal; loans are uncollateralized and must be repaid in one transaction. | Variable; creating fake identities may require resources and effort. |
| Defense Mechanisms | Flash loan limits, time delays, oracle manipulation prevention. | Identity verification, Sybil resistance algorithms, staking requirements. |
Which is better?
Flash loan attacks exploit vulnerabilities in decentralized finance (DeFi) protocols by borrowing large sums without collateral, enabling rapid manipulation of asset prices or governance votes. Sybil attacks involve creating numerous fake identities to gain disproportionate influence in a network, often targeting consensus mechanisms or voting processes. While flash loan attacks can cause immediate financial losses, Sybil attacks undermine network integrity and trust, making both threats critically important in different contexts of blockchain security.
Connection
Flash loan attacks and Sybil attacks are interconnected through their exploitation of decentralized finance (DeFi) protocols' vulnerabilities. Flash loan attacks leverage instant, uncollateralized loans to manipulate asset prices or governance, while Sybil attacks involve creating multiple fake identities to gain disproportionate influence in voting systems. Both methods weaken the integrity of DeFi ecosystems by enabling unfair control and financial exploitation.
Key Terms
Identity verification
Sybil attacks exploit weak identity verification by creating multiple fake identities to manipulate system consensus, while flash loan attacks leverage instant, uncollateralized loans to exploit vulnerabilities in smart contracts without needing multiple identities. Effective identity verification mechanisms, such as decentralized identity protocols and robust KYC processes, are critical in preventing Sybil attacks but have limited impact on mitigating flash loan attacks. Explore more about the strategies and technologies enhancing security against these distinct blockchain threats.
Smart contracts
Sybil attacks exploit the creation of multiple fake identities to manipulate smart contract consensus mechanisms, undermining network integrity and governance. Flash loan attacks leverage instant, uncollateralized loans to manipulate DeFi protocols' price oracles, enabling attackers to drain funds through arbitrage or liquidation triggers. Explore detailed strategies to safeguard smart contracts against these evolving threats.
Collateral
Sybil attacks manipulate network consensus by creating multiple fake identities to gain disproportionate influence, often compromising decentralized governance and collateral verification processes. Flash loan attacks exploit uncollateralized, instant loans to manipulate asset prices or protocols, causing collateral liquidation or theft within a single transaction. Explore how collateral mechanisms can be fortified against these distinct threats to enhance blockchain security.
Source and External Links
What Is a Sybil Attack? - A Sybil attack manipulates peer-to-peer networks by a single entity creating multiple fake identities to gain disproportionate control or influence over the network, often used to disrupt blockchain or social media consensus mechanisms.
What is a sybil attack in crypto? - In crypto, a Sybil attack involves creating multiple fraudulent nodes to gain control over a blockchain network, threatening the network's integrity and security by compromising transaction finality and user privacy.
Sybil attack - Sybil attacks subvert network reputation systems by generating many fake identities, with documented examples including attacks on the Tor anonymity network and Bitcoin traffic, highlighting their real-world threat to privacy and security.
 dowidth.com
dowidth.com