Flash loan attacks exploit instant, uncollateralized loans to manipulate DeFi protocols for rapid profit, often causing significant financial losses. Smart contract exploits target vulnerabilities within code, allowing attackers to drain assets or disrupt services systematically. Discover the nuances and protective strategies behind these evolving threats in decentralized finance.
Why it is important
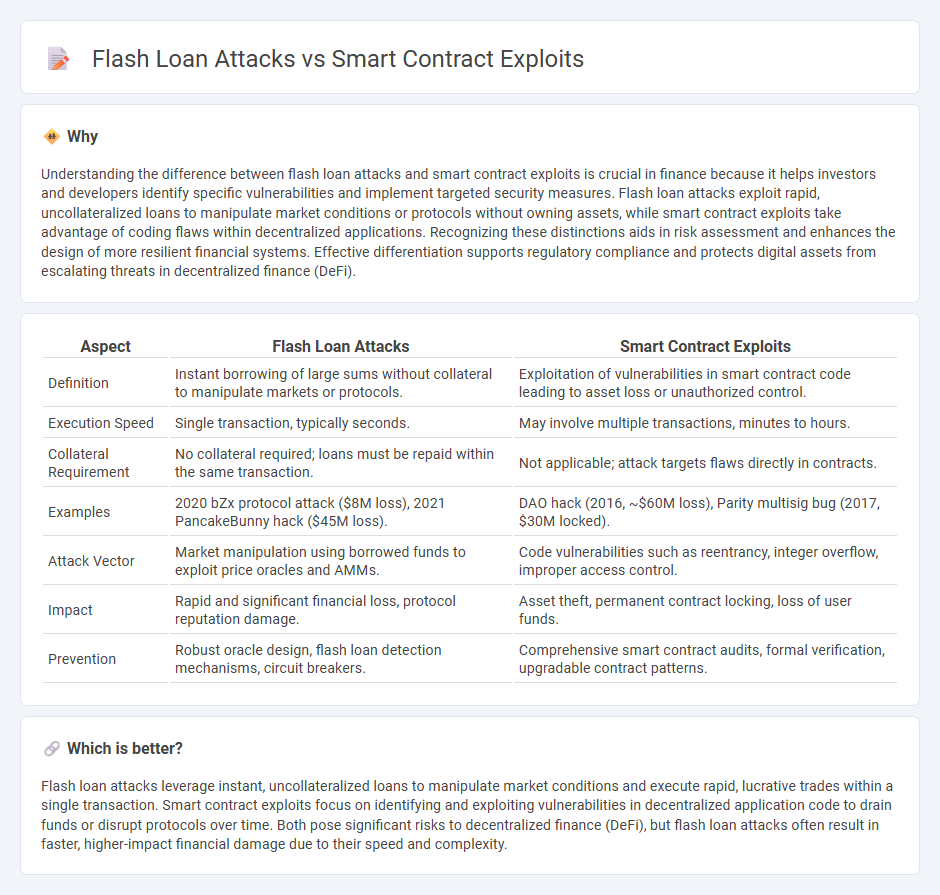
Understanding the difference between flash loan attacks and smart contract exploits is crucial in finance because it helps investors and developers identify specific vulnerabilities and implement targeted security measures. Flash loan attacks exploit rapid, uncollateralized loans to manipulate market conditions or protocols without owning assets, while smart contract exploits take advantage of coding flaws within decentralized applications. Recognizing these distinctions aids in risk assessment and enhances the design of more resilient financial systems. Effective differentiation supports regulatory compliance and protects digital assets from escalating threats in decentralized finance (DeFi).
Comparison Table
| Aspect | Flash Loan Attacks | Smart Contract Exploits |
|---|---|---|
| Definition | Instant borrowing of large sums without collateral to manipulate markets or protocols. | Exploitation of vulnerabilities in smart contract code leading to asset loss or unauthorized control. |
| Execution Speed | Single transaction, typically seconds. | May involve multiple transactions, minutes to hours. |
| Collateral Requirement | No collateral required; loans must be repaid within the same transaction. | Not applicable; attack targets flaws directly in contracts. |
| Examples | 2020 bZx protocol attack ($8M loss), 2021 PancakeBunny hack ($45M loss). | DAO hack (2016, ~$60M loss), Parity multisig bug (2017, $30M locked). |
| Attack Vector | Market manipulation using borrowed funds to exploit price oracles and AMMs. | Code vulnerabilities such as reentrancy, integer overflow, improper access control. |
| Impact | Rapid and significant financial loss, protocol reputation damage. | Asset theft, permanent contract locking, loss of user funds. |
| Prevention | Robust oracle design, flash loan detection mechanisms, circuit breakers. | Comprehensive smart contract audits, formal verification, upgradable contract patterns. |
Which is better?
Flash loan attacks leverage instant, uncollateralized loans to manipulate market conditions and execute rapid, lucrative trades within a single transaction. Smart contract exploits focus on identifying and exploiting vulnerabilities in decentralized application code to drain funds or disrupt protocols over time. Both pose significant risks to decentralized finance (DeFi), but flash loan attacks often result in faster, higher-impact financial damage due to their speed and complexity.
Connection
Flash loan attacks exploit the instantaneous, uncollateralized borrowing feature in DeFi platforms to manipulate asset prices or execute complex transactions within a single blockchain transaction. Smart contract exploits occur when flaws in the contract code are targeted to drain funds or alter logic. These attacks are connected as flash loans provide attackers with temporary capital to exploit vulnerabilities in smart contracts, amplifying the risk of significant financial losses in decentralized finance ecosystems.
Key Terms
Code Vulnerability
Smart contract exploits primarily arise from code vulnerabilities such as reentrancy, unchecked external calls, and improper input validation, which attackers manipulate to drain funds or alter contract behavior. Flash loan attacks exploit these vulnerabilities by borrowing large amounts of capital without collateral and executing complex, rapid transactions that manipulate price oracles, liquidity pools, and governance mechanisms. Explore in-depth analyses of these code vulnerabilities and attack vectors for enhanced blockchain security measures.
Liquidity Manipulation
Liquidity manipulation in smart contract exploits often involves artificially inflating or draining token pools to disrupt market balance and extract value. Flash loan attacks exploit these vulnerabilities by borrowing large amounts of capital without collateral, using it to manipulate prices or liquidity pools within a single transaction to achieve profit. Explore detailed analysis and case studies to understand the mechanisms and defenses against these sophisticated liquidity manipulation tactics.
Oracle Manipulation
Oracle manipulation poses a significant threat in smart contract exploits, often leveraged in flash loan attacks to manipulate asset prices and drain liquidity pools rapidly. These attacks exploit the reliance of decentralized finance (DeFi) platforms on external price feeds, causing skewed data that triggers unauthorized contract executions and financial losses. Explore how enhanced oracle designs and real-time monitoring can mitigate these vulnerabilities and strengthen DeFi security protocols.
Source and External Links
Smart Contract Security Risks: Today's 10 Top Vulnerabilities - Cobalt - Covers major smart contract exploits such as reentrancy attacks, integer overflow/underflow, access control flaws, front-running, and denial of service (DoS), explaining how they work and recommended mitigations.
Most Common Smart Contract Attacks - Hacken - Details the most frequent smart contract attacks including reentrancy, unchecked external calls, and block info dependency, focusing on how attackers exploit these vulnerabilities to drain funds or disrupt contracts.
12 Smart Contract Vulnerabilities and How to Mitigate Them - Explains vulnerabilities like oracle manipulation, flash loan attacks, and insecure randomness alongside reentrancy, providing specific examples of exploits and practical fixes such as using decentralized oracles.
 dowidth.com
dowidth.com