Flash loan attacks exploit temporary, uncollateralized loans to manipulate DeFi protocols for instant profit, often draining liquidity pools within seconds. Reentrancy attacks exploit smart contract vulnerabilities by repeatedly calling a function before the previous execution completes, enabling unauthorized fund withdrawals. Discover how these threats impact decentralized finance security and preventative measures.
Why it is important
Understanding the difference between flash loan attacks and reentrancy attacks is crucial in finance to safeguard decentralized finance (DeFi) platforms from vulnerabilities. Flash loan attacks exploit uncollateralized loans to manipulate asset prices or execute complex transactions within a single block. Reentrancy attacks involve repeatedly calling a function before the previous execution completes, allowing attackers to drain funds from smart contracts. Distinguishing these threats enables developers and investors to implement targeted security measures and protect digital assets effectively.
Comparison Table
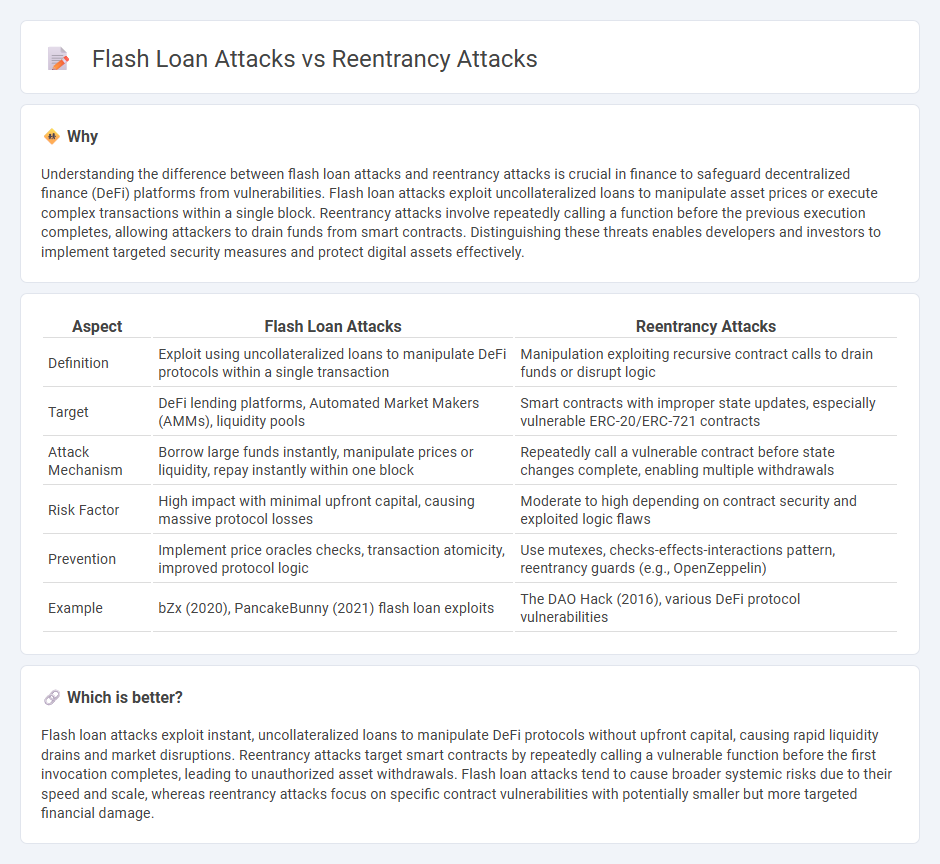
| Aspect | Flash Loan Attacks | Reentrancy Attacks |
|---|---|---|
| Definition | Exploit using uncollateralized loans to manipulate DeFi protocols within a single transaction | Manipulation exploiting recursive contract calls to drain funds or disrupt logic |
| Target | DeFi lending platforms, Automated Market Makers (AMMs), liquidity pools | Smart contracts with improper state updates, especially vulnerable ERC-20/ERC-721 contracts |
| Attack Mechanism | Borrow large funds instantly, manipulate prices or liquidity, repay instantly within one block | Repeatedly call a vulnerable contract before state changes complete, enabling multiple withdrawals |
| Risk Factor | High impact with minimal upfront capital, causing massive protocol losses | Moderate to high depending on contract security and exploited logic flaws |
| Prevention | Implement price oracles checks, transaction atomicity, improved protocol logic | Use mutexes, checks-effects-interactions pattern, reentrancy guards (e.g., OpenZeppelin) |
| Example | bZx (2020), PancakeBunny (2021) flash loan exploits | The DAO Hack (2016), various DeFi protocol vulnerabilities |
Which is better?
Flash loan attacks exploit instant, uncollateralized loans to manipulate DeFi protocols without upfront capital, causing rapid liquidity drains and market disruptions. Reentrancy attacks target smart contracts by repeatedly calling a vulnerable function before the first invocation completes, leading to unauthorized asset withdrawals. Flash loan attacks tend to cause broader systemic risks due to their speed and scale, whereas reentrancy attacks focus on specific contract vulnerabilities with potentially smaller but more targeted financial damage.
Connection
Flash loan attacks exploit temporary, uncollateralized loans to manipulate vulnerable DeFi protocols, often triggering reentrancy attacks by repeatedly calling a function before the initial transaction completes. Both attack vectors leverage smart contract weaknesses to drain funds, with flash loans providing the capital and reentrancy enabling repeated exploitation of contract logic. The intersection of these techniques elevates the risk of significant financial loss in decentralized finance ecosystems.
Key Terms
Smart Contracts
Reentrancy attacks exploit vulnerabilities in smart contracts by allowing malicious actors to repeatedly call a function before the previous execution completes, draining funds or manipulating contract state. Flash loan attacks leverage the ability to borrow large amounts of cryptocurrency instantly within a single transaction, often combining market manipulation or reentrancy to exploit DeFi protocols. Explore in-depth techniques and protective measures against these threats to secure smart contracts effectively.
Liquidity
Reentrancy attacks exploit vulnerabilities in smart contract code by repeatedly calling a function before the initial execution completes, often draining liquidity pools in decentralized finance (DeFi) platforms. Flash loan attacks leverage instantaneous, uncollateralized loans to manipulate market conditions or exploit price oracles, leading to massive liquidity extraction within a single transaction. Explore the mechanics of these attacks and their impact on liquidity security in DeFi protocols.
Atomicity
Reentrancy attacks exploit the lack of atomicity in smart contract functions, allowing attackers to repeatedly call a function before the initial execution completes and manipulate contract states. Flash loan attacks leverage atomic transactions to borrow large amounts of capital without collateral, enabling arbitrage or price manipulation within a single transaction block. Explore the mechanics of these vulnerabilities further to strengthen decentralized finance security.
Source and External Links
A Broad Overview of Reentrancy Attacks in Solidity Contracts - A reentrancy attack exploits a smart contract vulnerability where an attacker contract repeatedly calls a victim contract's withdrawal function before the victim updates its balance, draining funds continuously.
Solodit Checklist Explained (8): Reentrancy Attack - Cyfrin - Reentrancy attacks occur when an attacker uses a fallback function to recursively call a victim contract's withdraw function before the victim updates the attacker's balance, enabling repeated unauthorized withdrawals.
Reentrancy Attacks and The DAO Hack Explained - Chainlink Blog - The infamous DAO hack was caused by a reentrancy vulnerability where the contract sent Ether before updating the sender's balance, allowing attackers to repeatedly withdraw funds before the state update.
 dowidth.com
dowidth.com