Behavioral biometrics analyzes unique patterns such as typing rhythms, mouse movements, and touchscreen gestures to verify user identity, providing continuous and passive authentication in banking security. Two-factor authentication (2FA) enhances account protection by requiring users to present two distinct credentials, typically combining something they know (password) with something they have (a mobile device or hardware token). Explore deeper into how these security methods revolutionize fraud detection and customer experience in modern banking.
Why it is important
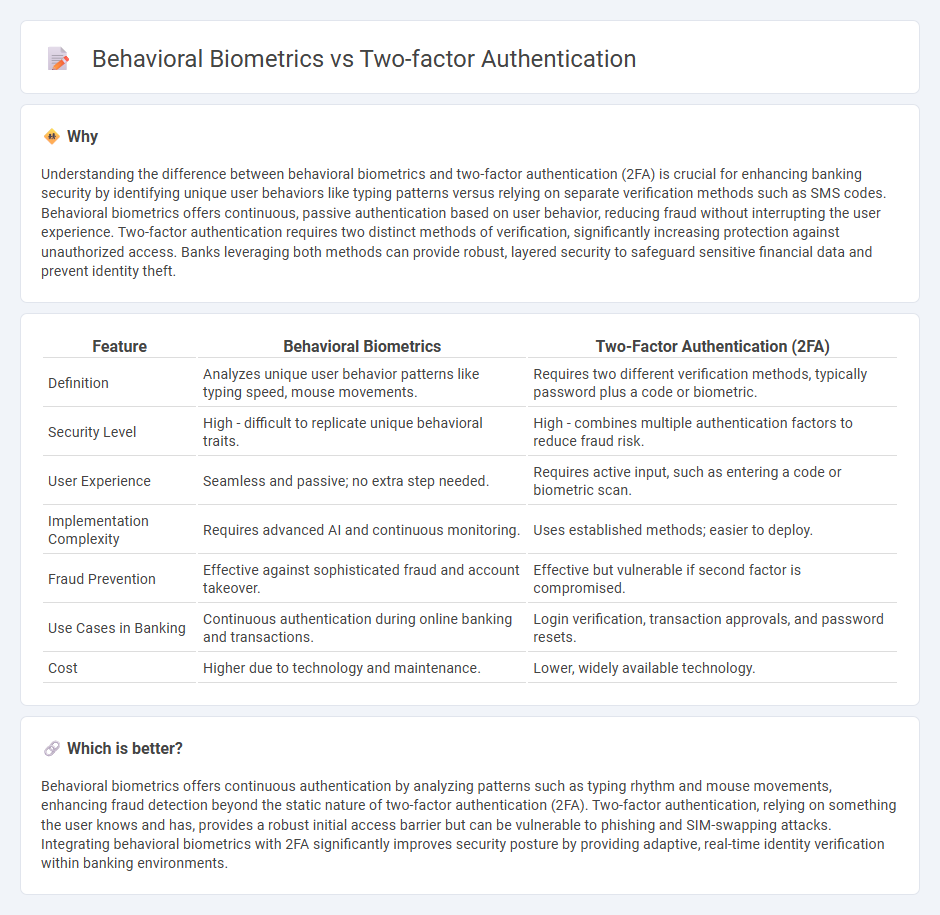
Understanding the difference between behavioral biometrics and two-factor authentication (2FA) is crucial for enhancing banking security by identifying unique user behaviors like typing patterns versus relying on separate verification methods such as SMS codes. Behavioral biometrics offers continuous, passive authentication based on user behavior, reducing fraud without interrupting the user experience. Two-factor authentication requires two distinct methods of verification, significantly increasing protection against unauthorized access. Banks leveraging both methods can provide robust, layered security to safeguard sensitive financial data and prevent identity theft.
Comparison Table
| Feature | Behavioral Biometrics | Two-Factor Authentication (2FA) |
|---|---|---|
| Definition | Analyzes unique user behavior patterns like typing speed, mouse movements. | Requires two different verification methods, typically password plus a code or biometric. |
| Security Level | High - difficult to replicate unique behavioral traits. | High - combines multiple authentication factors to reduce fraud risk. |
| User Experience | Seamless and passive; no extra step needed. | Requires active input, such as entering a code or biometric scan. |
| Implementation Complexity | Requires advanced AI and continuous monitoring. | Uses established methods; easier to deploy. |
| Fraud Prevention | Effective against sophisticated fraud and account takeover. | Effective but vulnerable if second factor is compromised. |
| Use Cases in Banking | Continuous authentication during online banking and transactions. | Login verification, transaction approvals, and password resets. |
| Cost | Higher due to technology and maintenance. | Lower, widely available technology. |
Which is better?
Behavioral biometrics offers continuous authentication by analyzing patterns such as typing rhythm and mouse movements, enhancing fraud detection beyond the static nature of two-factor authentication (2FA). Two-factor authentication, relying on something the user knows and has, provides a robust initial access barrier but can be vulnerable to phishing and SIM-swapping attacks. Integrating behavioral biometrics with 2FA significantly improves security posture by providing adaptive, real-time identity verification within banking environments.
Connection
Behavioral biometrics enhance two-factor authentication by analyzing unique user patterns like keystroke dynamics and mouse movements, adding an invisible security layer beyond passwords and physical tokens. This combination significantly reduces fraud risk in banking by continuously verifying user identity during transactions. Integrating these technologies creates adaptive authentication processes that improve both security and user experience.
Key Terms
Multi-factor Authentication (MFA)
Two-factor authentication (2FA) enhances security by requiring two distinct verification methods, typically combining something you know (password) with something you have (a code sent to a device), while behavioral biometrics analyze unique user behaviors such as typing patterns or mouse movements to continuously verify identity within multi-factor authentication (MFA) systems. MFA integrates multiple authentication layers, significantly reducing the risk of unauthorized access by layering 2FA with behavioral biometrics for dynamic, ongoing verification that adapts to user behavior. Explore how combining 2FA and behavioral biometrics in MFA can transform your security strategy and provide robust protection against evolving cyber threats.
User Behavior Analytics (UBA)
User Behavior Analytics (UBA) leverages behavioral biometrics by continuously monitoring patterns such as typing rhythm, mouse movements, and login times to detect anomalies that may indicate unauthorized access, offering a dynamic security layer beyond traditional two-factor authentication (2FA). Unlike 2FA, which relies on static codes or devices, UBA provides real-time risk assessment tailored to individual user behavior, significantly reducing false positives and improving threat detection accuracy. Explore how integrating UBA with multi-factor authentication can enhance overall cybersecurity resilience.
One-Time Password (OTP)
Two-factor authentication (2FA) commonly utilizes One-Time Passwords (OTP) sent via SMS or email to enhance security by requiring users to provide a password plus a temporary code. Behavioral biometrics, in contrast, analyzes unique user patterns such as typing speed and mouse movements to verify identity without relying on OTPs. Explore the advantages and deployment scenarios of these methods to determine the best fit for your security needs.
Source and External Links
What is Two-Factor Authentication (2FA)? - Two-factor authentication (2FA) is a security process requiring users to provide two different authentication factors to verify themselves.
What is two-factor authentication? | 2-step verification - Two-factor authentication (2FA) enhances security by requiring users to prove their identity through two distinct means before being granted access.
What Is Two-Factor Authentication (2FA)? - Two-factor authentication (2FA) is an identity and access management security method that requires two forms of identification to access resources and data.
 dowidth.com
dowidth.com